Rethinking AD: The Four Stages of Separation, Part 2
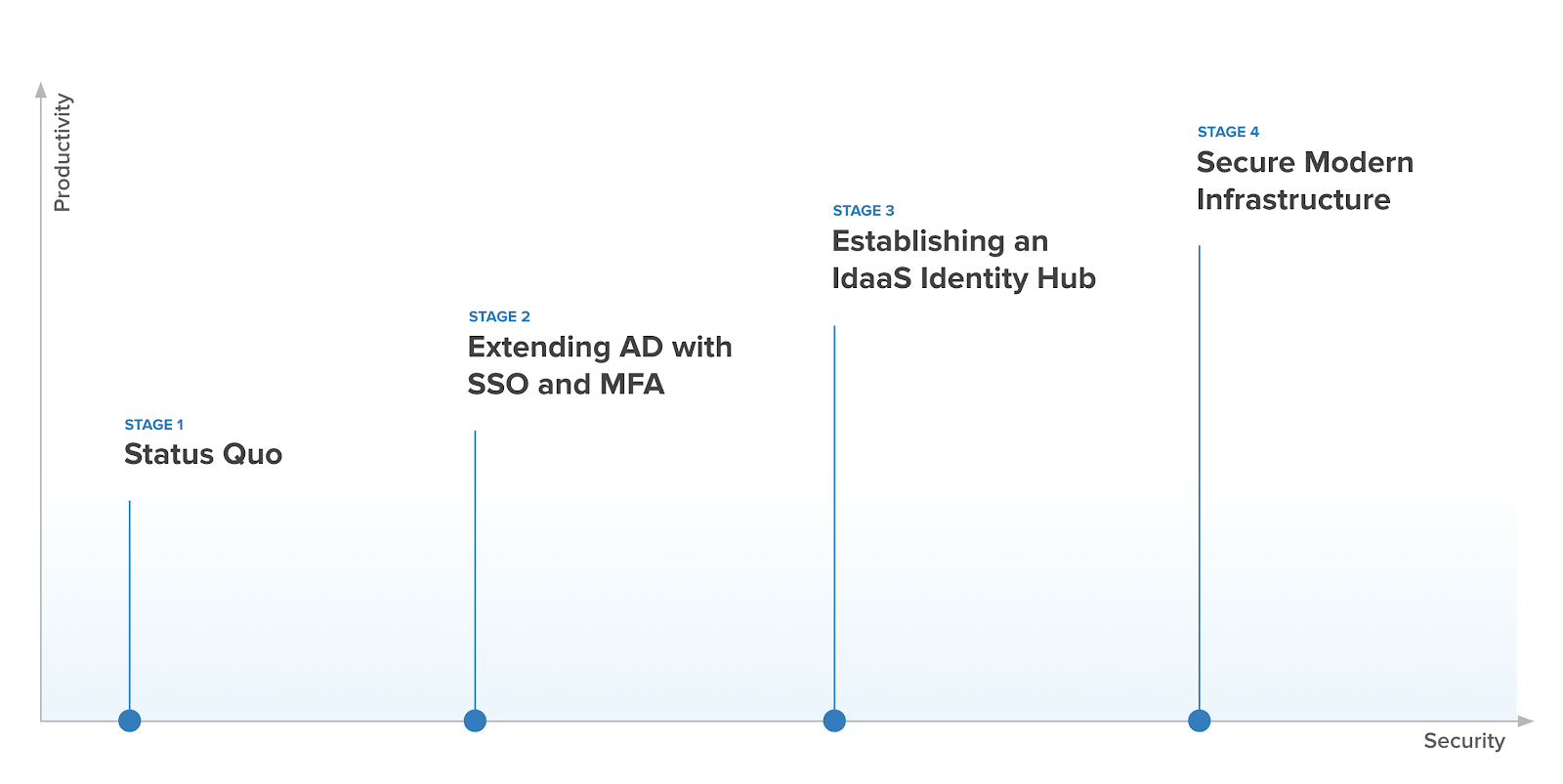
In part one of The Four Stages of Separation from Active Directory (AD), we covered stages 1 - 3: 1. Where are you today? 2. Make sure you’re safe, and 3. Get everyone together. In part 2, we’ll cover Stages 4.1 and 4.2, and we’ll describe a few customers who started this journey and detail where they are today.
Still wondering why you should even consider breaking up with Active Directory? Read our reasons Why It’s Time to Break Up with Active Directory, and learn about the Top 5 Things You Can Look Forward to When You Rethink Active Directory—then meet me back here.
We developed the Rethink AD Maturity Model as a journey based on the combined experiences of Okta customers. It follows how they’ve successfully tackled IT modernization with a specific focus on reducing their Active Directory footprint. We’ll walk a hypothetical company through the four stages, describe why the various components are important, and how Okta can help with them. Let’s start with how you got to where you are today.
Stage 4.1 — Bring Your Own Device (BYOD): Secure Modern Infrastructure
It all started in marketing. Those creative types just had to have Macs. Which would have been fine, even after iPhones came along. But once Android launched, everything got more complicated.
The way our customers and partners were modernizing, we were forced to adapt from a “widget” company to a “technology” company, hiring developers, practicing DevOps, DevSecOps, and everything else. Overnight, Macbooks became cool because all the developers had them, and suddenly so did everyone else. So now we’re left trying to secure all of these devices, and all the corporate data on them.
Where did all these devices come from?
Not that long ago, the only type of computing device in the workplace was a Windows-based PC. And while Mac-based devices existed, they didn’t in meaningful numbers, if at all, in most organizations. At the same time, Active Directory, created to manage Windows-based PCs, did a great job through GPOs, System Center Configuration Manager (SCCM), and other methods to manage Windows devices. This remains true today.
However, as soon as smartphones arrived, the number of Android and iOS devices in the workplace exploded. So while multiple generations of the same device began to exist at once, the percentage of Mac-based laptops at the office was increasing as well. A device explosion occurred, generating enormous heterogeneity and making it very difficult for IT departments to keep up, Why? AD and the tools around it are designed for Windows-only devices. Some organizations attempted to force workers to draw solely from an approved list of one or two devices in a Choose Your Own Device (CYOD) approach, but either through protest or poor adoption, employees made it clear that using their own devices was a priority, and employers had to follow suit if they wanted to compete for the top talent.
Device management or bust
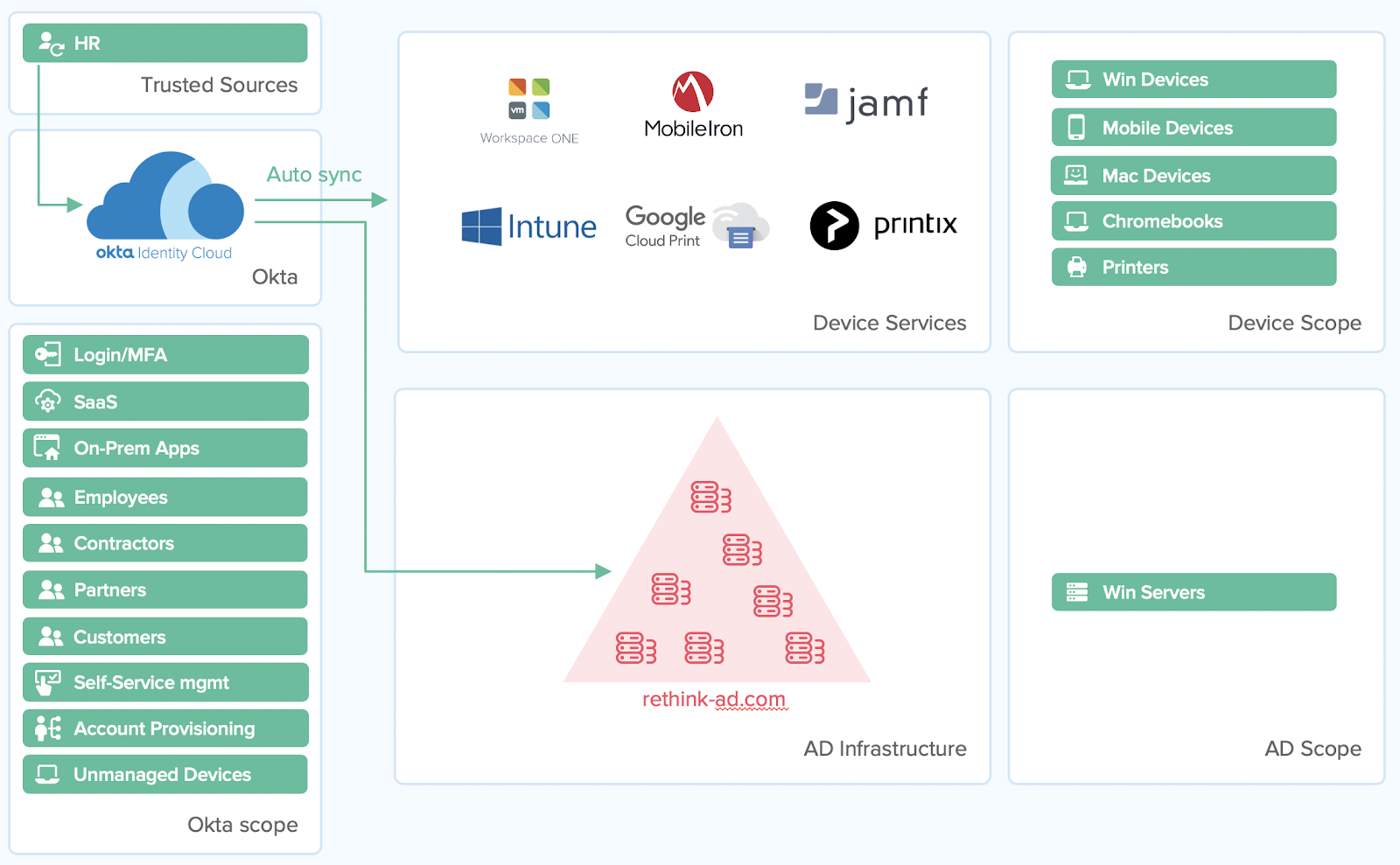
Addressing this challenge, Unified Endpoint Management (UEM) and Mobile Device Management (MDM) technologies like VMware Workspace One and MobileIron arose. These solutions were specifically designed to manage a wide variety of device types and ensure that they were properly secured, up-to-date, and safe to use, among other things. Such was the depth and complexity demanded by users, that certain device management vendors like JAMF also gained prominence by specializing in a single device type (i.e., macOS).
Apart from mobile phones and computers, other service providers manage devices such as printers, WiFi, and networking hardware using modern, cloud-based or serverless solutions, through existing standards like LDAP.
Broadly speaking, device management is needed because the original ecosystem of Windows-only devices that existed when Active Directory was first released no longer exists. Instead, non-Windows computers, smartphones, mobile devices, tablets, and Chromebooks have taken their place. Device management solutions ensure that all types of devices are properly secured, configured, and managed. Many of the policies that AD formerly supported, via GPOs, are conveyed via device management, while Okta manages the users. Together, they address most of the higher demands for user and device management that are out of AD’s reach by elevating the organization’s cloud and mobile security.
Stage 4.2 — Infrastructure is cool: Secure Modern Infrastructure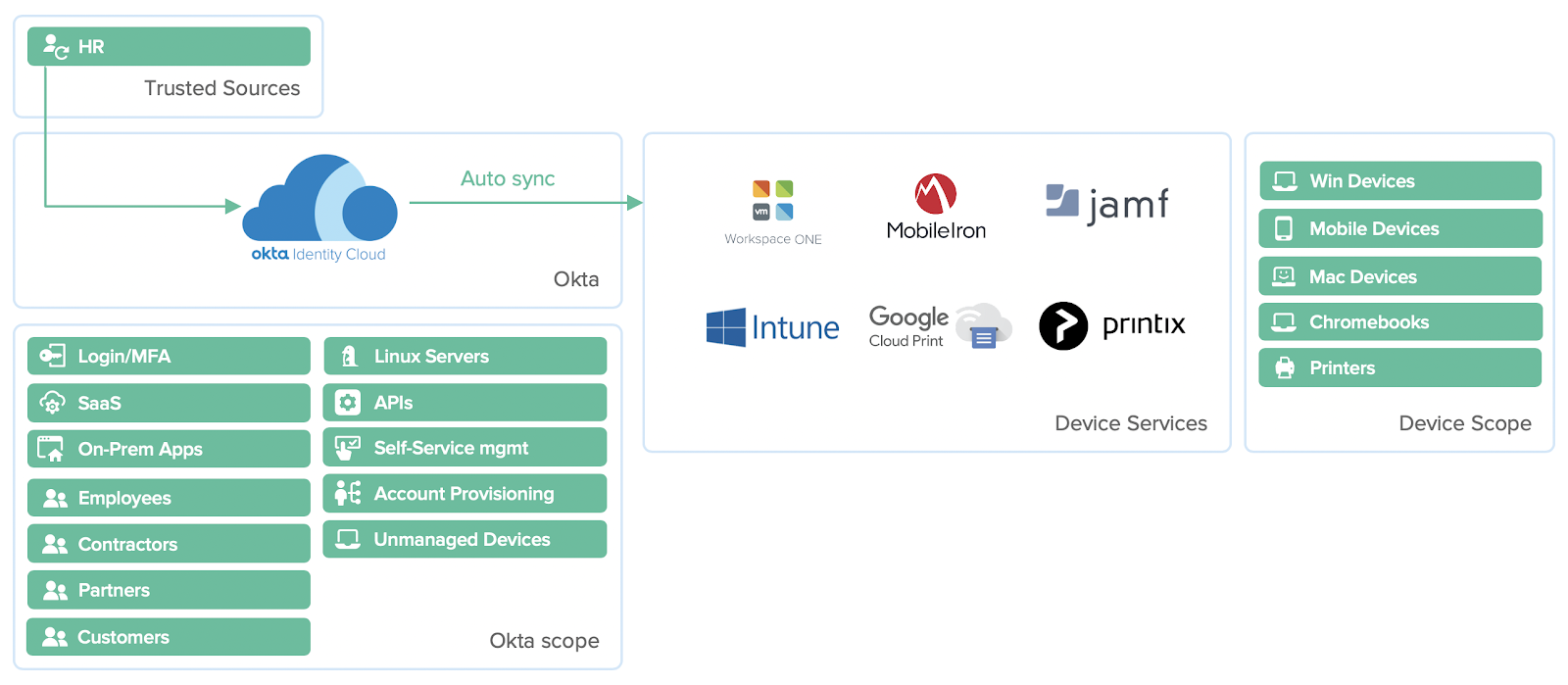
Chris’ mobile app team started working more closely with Jane, the lead for the enterprise infrastructure team. Jane started transitioning our apps from a classic three-tier web server, app server, database architecture to a more modern design. Part of this change was moving to containers and microservices for all new apps and shifting from the current data center to a multi-cloud environment across several cloud platforms. During this transition, her team would like a way to simplify their server access (which is predominantly Linux) to something more modern, but still leverage standard protocols like SSH.
Fine-grained awesomeness
All the changes to AD we’ve discussed so far are related to IT’s front end — users, devices, secure app access, etc. What about the stuff behind the scenes? The servers that run the apps and the plumbing that connect apps to databases and each other? Do the changes we’re making in AD impact them? How does Okta support these resources, if at all?
To date, most organizations practice server micromanagement, which means that each individual server contains administrative accounts, and admins manage each server as separate entities. And while tools like SCCM exist to help automate management for Windows resources, Linux is a totally different beast, needing a Linux-specific approach that Windows has a hard time delivering. For this reason, admins typically maintain shared accounts and passwords to access these servers, which make for poor security, and weak auditing and tracking.
Okta’s Advanced Server Access (ASA) gets rid of admin accounts in the conventional sense, and each administrator uses their own identity, which ASA uses to create individual SSH sessions each time. Admins wishing to access the server resource are minted a new certificate, specific to that session. This provides fine-grain controls for each session, as well as monitoring and tracking of admin usage. And if an admin ever leaves, deprovisioning their identity automatically removes their rights to the server—without the need to change every password on every server they’ve accessed. This simplifies deprovisioning overall and minimizes impact to the remaining staff. What’s more, this is done in real-time.
In general, as more and more workloads are shifted to dynamic infrastructure, where resources are spun and down on-demand, the need for tools like SCCM, which suffer from complexity and the brittleness of being proprietary, will shrink.
Infrastructure isn’t just servers
As the numbers of apps proliferate and are controlled via API gateways, more scalable solutions are needed to help manage and secure them. This is especially true when APIs are the top target for bad actors seeking access to critical data or ways to enter into your environment. Okta’s API Access Management solution secures those APIs en masse by integrating to API gateways like Mulesoft and others.
How does Okta help organizations rethink AD today?
While describing the use cases of our fictional customer was fun, the use cases themselves are very much rooted in reality. Okta’s customers have gone through similar scenarios themselves, and some are in varying stages of their own Rethink AD journey. Let’s look through a few of these customers in their own terms, review why they began, and see where they are today:
1. A global operations and logistics firm
|
Headcount: |
~5,000 |
|
Rethink AD Maturity: |
Stage 3.5 |
|
Initial Driver: |
High mobility and collaboration needs. Heavy investment in cloud resources and apps. Predominantly modern users. |
|
Biggest gains: |
Securing cloud apps and access. Rolling out MFA quickly. |
|
Biggest challenge: |
Legacy design did not enable cloud adoption. |
|
What’s next: |
Device management across their mixed mobile, Windows, and Mac devices. |
2. A multinational software consultancy
|
Headcount: |
~10,000 |
|
Rethink AD Maturity: |
Stage 4 |
|
Initial Driver: |
Began as a heavy Microsoft shop. Every laptop was Windows. Fragility and availability of AD was poor and caused by legacy footprint and outages. |
|
Biggest gains: |
Automated provisioning and deprovisioning. |
|
Biggest challenges: |
Eliminating dependencies, staying disciplined, and never adding to AD. |
|
What’s next: |
Shifting network management away from AD and eliminating AD. |
3. A global marketing consultancy
|
Headcount: |
~1,000 |
|
Rethink AD Maturity: |
Stage 2.5 |
|
Initial Driver: |
Heavy Microsoft shop. High number of creatives. Shifted towards Macs and BYOD. |
|
Biggest gains: |
Improved customer experience. Using best-of-breed security and productivity tools. BYOD. |
|
Biggest challenges: |
Dealing with complexities of consolidating their AD environment. Fortunately, Okta helped with that, reducing times and costs by several-fold. |
|
What’s next: |
Zero Trust is their next strategic initiative, and completing Rethink AD will actually help them get there. |
Let Okta help you take your first steps
Okta supports the core of the rethink AD effort. It was designed as a modern alternative for certain aspects of AD, but not for all. In reality, most organizations require a mix of solutions, and Okta is designed to work well with every one of them.
Recognize that some groups or teams within your organization may be in a better position to modernize and more easily rethink AD. Others may have more specific needs. In either case, it may make sense to rethink those groups first, modernizing each individual group, one at a time.
Lastly, while it seems like a daunting task, most worthwhile things are. Remember, rethinking your dependency on Active Directory does not necessarily mean replacing AD overnight. It’s about helping your organization understand what AD handles well and what it handles poorly—and then freezing its expansion. Just because it worked well in the past, doesn’t mean it will do so going forward. And once the growth of AD is stopped, organizations can start to retire the bad pieces, one at a time.