Top 10 Ways To Automate IT & Security Tasks With Okta Workflows
In this difficult economic climate, today’s companies are forced to continue innovating despite tighter budget constraints. At the same time, security breaches are only getting worse. Verizon indicates that 74% of breaches involved human error of some kind, a costly consequence of managing critical IT and security infrastructure with manual processes.
To keep up, companies must embrace automation to achieve consistent, long-term growth. Indeed, Bain & Company finds that companies that invest heavily in automation reduce costs by 22% and free up staff to do higher-value work.
That’s where Okta can help.
Introducing Okta Workflows, our no-code identity automation and orchestration platform. From customizing lifecycle management to automating critical security and IT tasks, Workflows’ drag and drop interface makes it easy for anyone to automate identity processes at scale.
Okta customers have seen tangible impacts, with the approximate amount of total dollars and total time saved by using Workflows equating to $5B and 130M hours.
These calculations represent an approximate amount of total savings based on Okta customers over one year (between May 2022 - May 2023)
To enable you to start saving time and money with Workflows automation, we’re sharing our top 10 most popular Workflows templates:
Customizing on/offboarding processes by extending LCM
IT admins can spend days and even weeks provisioning/deprovisioning employees by using error-prone, manual processes with custom code and scripts. Consequently, IT admins frequently encounter errors (duplicate account creation, users not having access to necessary applications) which can be detrimental to the productivity of new employees.
With Workflows, customers minimize these costly inefficiencies by automating the customization of lifecycle management. Overall, customers on average see a 75% reduction in time spent to onboard and offboard employees.
Top use cases for customizing lifecycle management:
- Assign temporary group membership: Enable agile workforces to be productive on their first day, whether they are vendors, partners, interns, etc
- Transfer assets upon offboarding (GDrive): Ensure business continuity when employees leave by transferring important assets automatically to their manager
- Send a welcome email to new app users: Facilitate a smooth onboarding process for new employees to hit the ground running on their first day.
- Create guest users for Office 365: Grant users access across multiple tenants so they can execute their tasks on the Microsoft platform.
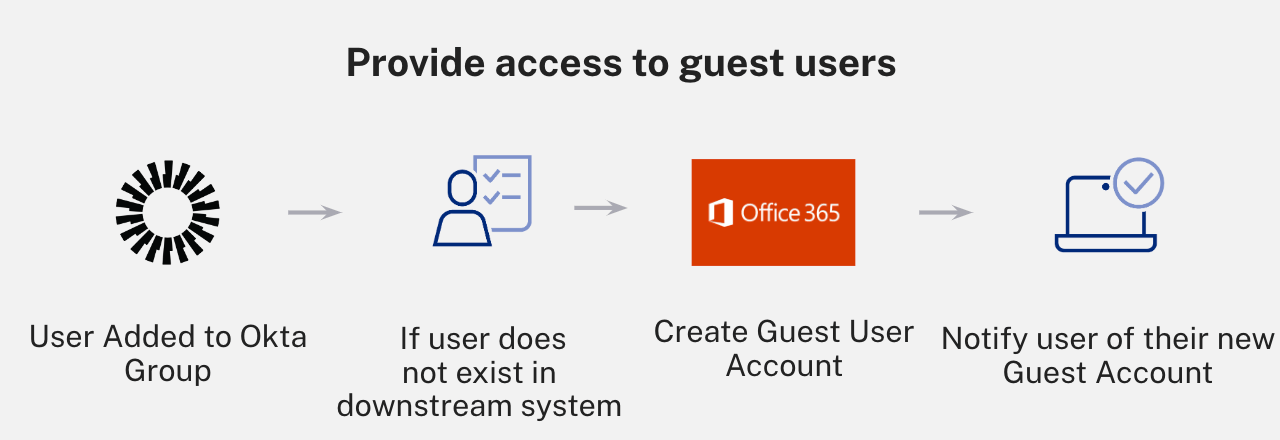
Provide access to guest users
Automate Operational Tasks and Maintenance
IT departments spend countless hours every week to maintain operational IT tasks. Using manual processes results in errors like paying for unused licenses, costing organizations thousands of dollars monthly and compromising their security compliance.
Today, IT departments leverage Workflows to simplify complex tech stacks and reduce the time needed to build/maintain custom scripts by 85%.
Top use cases for automating operational tasks and maintenance:
- Identify & suspend inactive users: Reduce costs by freeing up expensive application licenses and ensure that access is only granted to authorized users.
- Automate IT/security reports: Generate custom reports to audit security status and visualize data to derive meaningful insights.
- Automate communication + alerts: Ensure timely and accurate delivery of important information to relevant stakeholders to proactively respond to critical events.
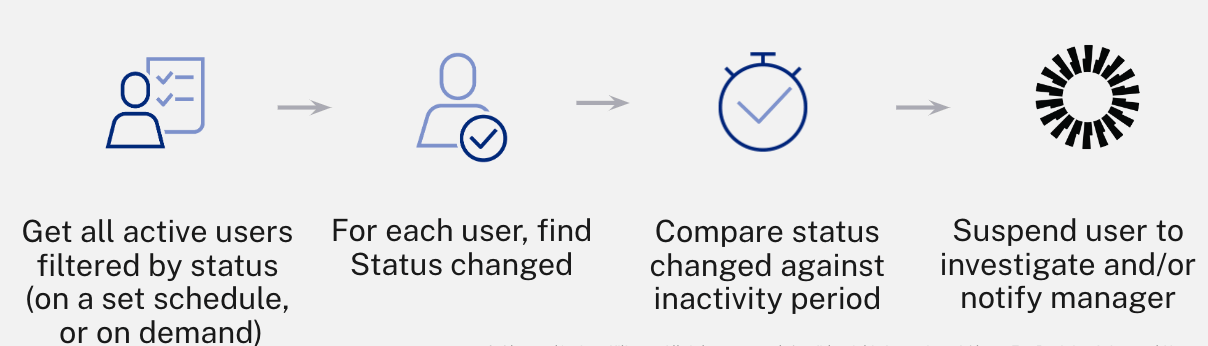
Discovery and notification of stale accounts
Protect Against Cyber Attacks with Security Automation
As mentioned above, security breaches have become increasingly prevalent and can easily cost organizations millions of dollars to recover.
Not only does automating security with Workflows decrease the probability of a breach by eliminating human error, but also enables you to implement solutions that proactively prevent an attack from happening or responding immediately to potentially suspicious behavior. . IBM Security reports a 65.2% difference in average breach cost between companies with fully deployed security automation compared to those with none deployed.
Top use cases for security automation:
- Respond to suspicious activity: Mitigate internal and external security risks with automated flows that can manage suspicious activity and end-user devices
- Track and alert for potential account takeovers: Proactively prevent data breaches by forcing re-authentication or clearing the user session to disrupt hackers.
- Temporarily exempt users from MFA: Allow users who have lost their phone to login via a different authentication policy for a predetermined amount of time
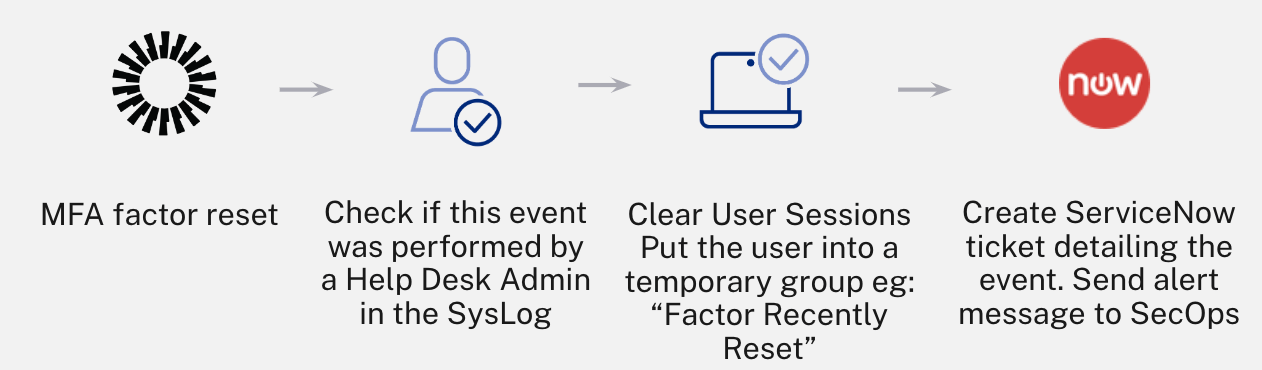
Tracking and alerting to prevent account takeovers
Ultimately, Workflows has been crucial towards helping customers scale IT & security processes to keep up with today’s unpredictable landscape. With its no-code interface and pre-built connectors/templates, customers can easily automate top use cases, including on/offboarding, operational tasks, security, and much more.
To learn more about how you can save time and money with Workflows, refer to our helpful docs below:

