Okta Privileged Access is generally available
We are thrilled to announce the general availability of Okta Privileged Access, our new privileged access management (PAM) offering, beginning this week. Okta Privileged Access is a powerful solution that elevates your security infrastructure and helps provide controlled access to your critical systems, applications, and data. This empowers your IT and security teams to mitigate the risk of unauthorized access, streamline your security operations, and support compliance with regulatory requirements. In an era where digital threats loom large, enhancing risk reduction and the integrity of your organization's critical resources is paramount.
Okta Privileged Access comes equipped with a rich set of features designed to meet the dynamic challenges of modern cybersecurity. Here's a glimpse into the capabilities that set our offering apart.
- Just-in-time (JIT) infrastructure access: JIT access ensures users have access to systems and resources for the shortest time necessary, minimizing the window of vulnerability and enhancing overall security.
- Privileged access requests: Empower your team with the ability to request and obtain privileged access swiftly and securely. Our streamlined process ensures that access is granted only when needed, reducing the risk of unauthorized usage.
- Privileged account vaulting: Safeguard your organization's most critical accounts by securely vaulting and managing privileged credentials. This feature protects against unauthorized access and mitigates the risk of credential misuse.
- Secrets management: Securely store and manage sensitive information such as API keys, passwords, and encryption keys. Our secrets vaulting safeguards critical data from unauthorized access.
- Cloud infrastructure entitlement discovery and analysis: Gain insight into your cloud infrastructure access entitlements. Identify and rectify excessive privileges, reducing the attack surface and enhancing overall security posture.
- Session Recording: Keep a watchful eye on all privileged sessions with our session recording feature. Detailed logs and recordings provide visibility into user activities, aiding in forensic analysis and compliance requirements.
Privileged Access: A key pillar of our unified solution for Workforce Identity
Imagine having a single pane of glass that grants comprehensive control over all your security services. With our PAM solution, we make this a reality. The Okta platform securely stores and manages identities while providing critical capabilities like auditing and reporting.
Okta's unification strategy allows our products to work together to help customers achieve their security goals more efficiently and effectively. For instance, customers can set up a transactional multi-factor authentication (MFA) policy rule in access management. Okta will then enforce the policy rule before granting access to privileged resources protected by Okta Privileged Access. This is an effective strategy to protect critical resources, especially when leveraging phishing-resistant authenticators like Okta Fastpass.
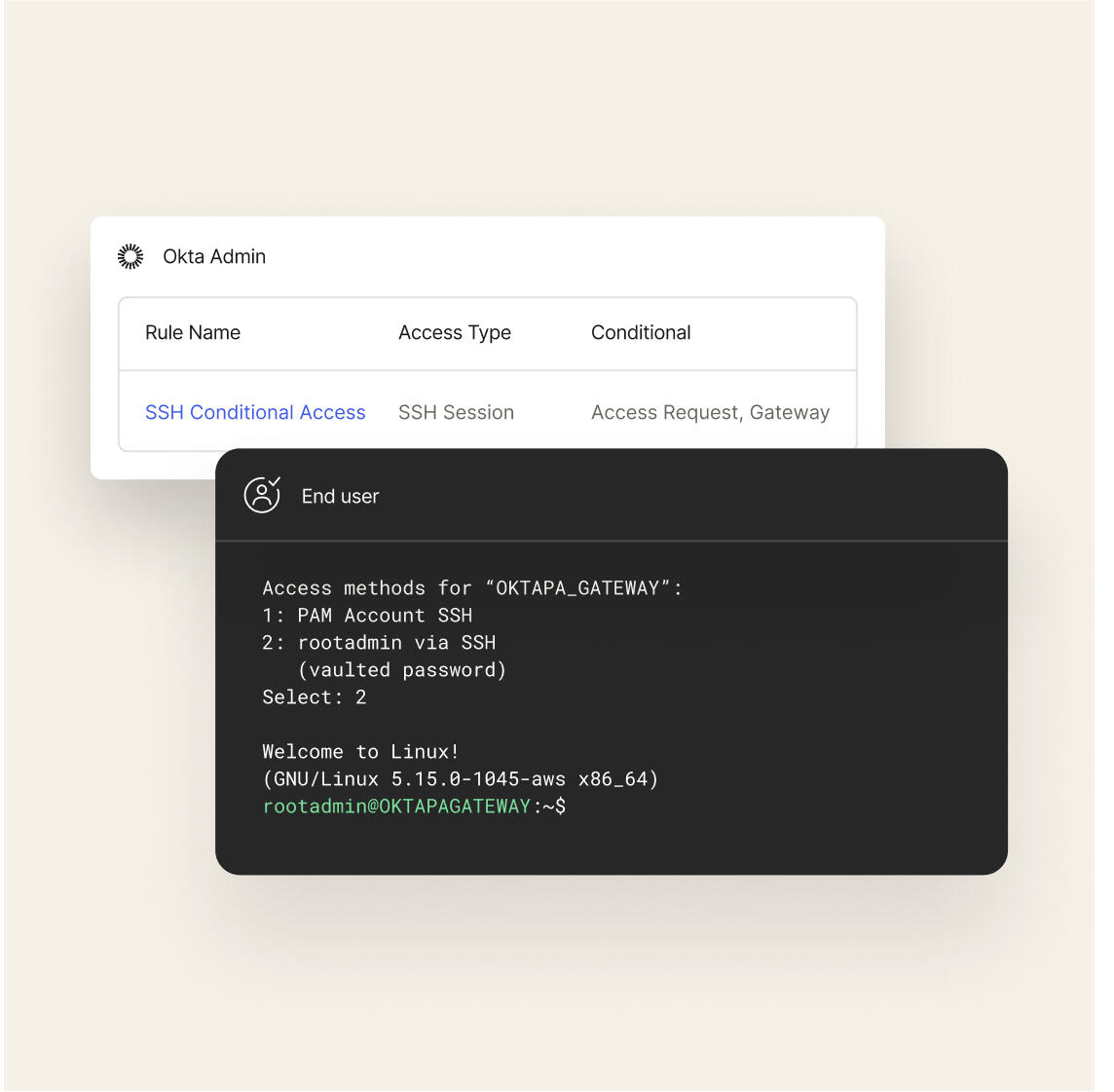
JIT access to a server via SSH
As another example, Okta Privileged Access allows customers to implement access request/approval workflows that must be satisfied before end users can access resources. Okta Privileged Access is directly integrated with Okta Identity Governance, allowing administrators to create customizable approval workflows that match their unique requirements while providing a seamless end-user experience for approving access requests. From privileged access requests to cloud infrastructure entitlement discovery and analysis, our solution seamlessly integrates all your security needs into a centralized interface.
Approval required to access a privileged server
If you're looking for a way to protect your organization's most critical assets, look no further than Okta Privileged Access. With its robust suite of features, you can fortify your defenses and safeguard your data against potential threats. Whether you're a business owner or a security professional, Okta Privileged Access gives you the power to take control of your security posture and stay ahead of the curve. So why wait? Contact our Sales team for more information and start using Okta Privileged Access today. Experience the peace of mind of knowing your data is safe and secure.