Identity is no longer simply a login management system. It’s the most targeted layer in your infrastructure, and often the least connected. It's how users access data, how services interact, and, increasingly, how attackers get in. What used to be an admin function is now the foundation of your entire security posture.
Our eBook, Secure Identity. Secure Everything., outlines a modern approach to identity that helps organizations move from patchwork controls to unified, scalable security. It introduces a framework for building identity into the core of your architecture, one that strengthens visibility, reduces risk, and adapts to the realities of cloud-first environments.
In the sections that follow, we’ll examine what that approach looks like in practice. We’ll explore the core principles of a modern identity strategy, how it helps close visibility gaps and reduce risk, and why leading teams are making identity the anchor of their enterprise security model.
Why identity became the center of enterprise security
Most traditional security models were built around the assumption of a hardened perimeter. But today’s environments are defined by distributed infrastructure, cloud-based applications, and users accessing resources from unmanaged devices and networks. While the perimeter still exists, it no longer represents the boundaries of access or risk.
What remains consistent across this sprawl is identity. It’s the primary control plane for enforcing policy, authorizing access, and logging activity. Whether it’s a contractor accessing a SaaS platform, a developer running a continuous integration and continuous deployment (CI/CD) pipeline, or an internal user authenticating to a cloud dashboard, identity connects everything. That consistency makes it a high-value target.
Credential theft and abuse remain among the most successful attack vectors. Threat actors don’t need to break in; they log in, often by exploiting weak authentication methods, misconfigured access policies, or gaps in visibility across identity systems. Even strong identity security measures like multi-factor authentication (MFA) or single sign-on (SSO) can be ineffective if they’re not applied consistently across the environment.
The attack surface has shifted, so identity security can’t function as a standalone system or an administrative task. It has to be treated as what it is: a critical layer of your security architecture. It needs to enforce controls in real time, integrate at all levels with other tools, and provide visibility across every type of identity, human and machine. Without that, you rely on fragmented controls, manual oversight, and outdated assumptions.
And that’s exactly what attackers are counting on.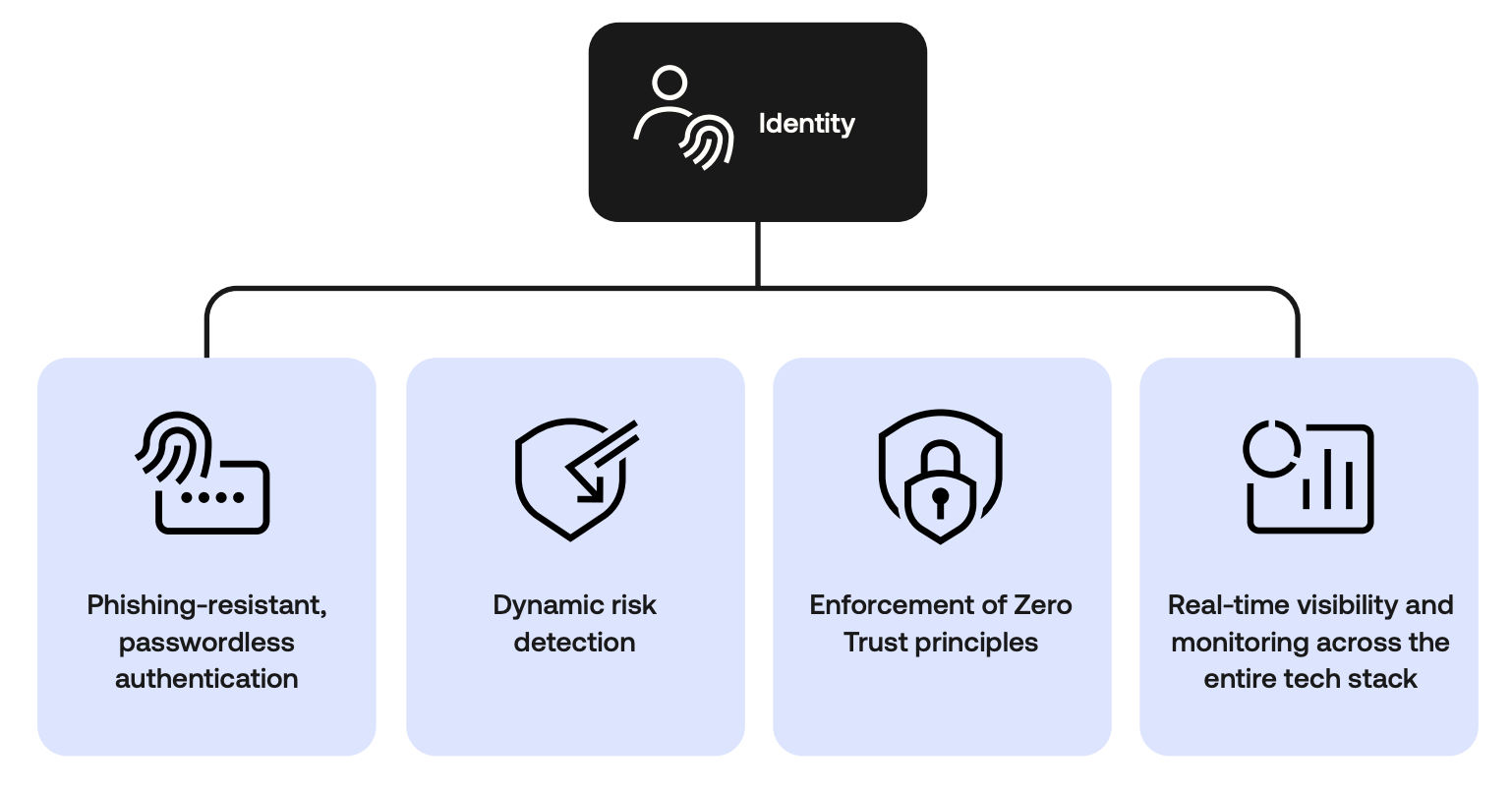
What identity looks like when it’s working
Once identity becomes part of your core security architecture, it needs to do more than authenticate users. It should connect systems, enforce consistent policies, and give teams the tools to make fast, informed decisions.
That’s the purpose of an identity fabric.
Rather than layering tools on top of each other, an identity fabric weaves identity, access, and context into a single framework. It gives security teams unified control, smarter integrations, and a more adaptive approach to access. Here’s how it works.
Unified access and centralized control
When identities are spread across disconnected systems, security gaps multiply. Standing access goes unnoticed, policies drift, and non-human accounts often get overlooked. A centralized approach closes those gaps.
With an identity fabric, every user, whether human or machine, is governed through a single system of control. Access policies are easier to enforce, audit trails stay intact, and permissions can be updated or revoked without delay.
Integration across your stack
Identity systems should not operate in silos. They need to communicate with the rest of your security ecosystem, sharing signals, adapting policies, and enabling faster response. Traditional IAM systems often connect superficially, with limited signal sharing and no real coordination between tools. An identity fabric changes that by enabling deep integration between identity services, security tools, cloud platforms, and data sources.
That integration is two-way. Identity systems ingest behavioral and contextual signals from the rest of your stack, then return enriched insights to power smarter policy decisions, alerting, and automated response.
Context-aware security
Access decisions should reflect risk in real time. A login that seems safe at 9:00 a.m. might look very different at 3:00 a.m. from an unmanaged device. Static policies don’t account for changes in behavior, unusual logins, or signs of compromise.
An identity fabric uses signals like location, device posture, and behavioral analytics to assess context and adjust access accordingly. A user on a trusted device may pass through without friction. One logging in from an unrecognized location might trigger a step-up challenge. The goal is to match the level of control to the level of risk automatically and without slowing down the business.
Built-in governance and scale
With access reviews, certifications, and logging built into your identity architecture, audit readiness becomes part of daily operations. An identity fabric supports this by embedding governance at the control layer. Teams can apply policies uniformly, automate enforcement, and scale without creating more complexity. New systems, new users, and new services can be brought in quickly while still meeting internal and external requirements.
What a unified identity strategy enables
When access, risk, and context are unified across systems, identity stops causing a bottleneck. It becomes the control plane for your entire security stack.
Security teams can detect and respond to threats with far more speed and context. Access decisions aren’t based on static policies alone. Instead, they reflect real-time authentication data, device posture, and behavior patterns pulled from across the environment. A session that looks suspicious can be blocked instantly, and a user whose risk profile changes mid-session can be re-evaluated on the fly.
Users benefit from the same context-aware approach. With phishing-resistant authentication and adaptive access flows in place, low-risk logins move faster, while higher-risk activity prompts additional checks. Instead of slowing everyone down, additional checks happen when needed, not across the board.
In cloud-based and hybrid environments, where workloads shift constantly and infrastructure is distributed, that kind of flexibility is critical. A unified identity platform ensures that access policies follow the identity, not the device or location. Every authentication method, system, and session aligns with a central security posture.
Identity becomes the thread connecting enforcement across your stack, from internal teams to external vendors, from human to machine identities. The result is stronger security, cleaner architecture, and a system that can scale without creating new blind spots.
Use cases where identity makes the biggest impact
The biggest returns on identity strategy show up in areas where legacy tools fall short, such as:
Non-human identities with overextended access
Service accounts, automation tools, and AI agents often operate behind the scenes, with broad privileges and little oversight. Without proper governance, they become blind spots. A modern identity strategy brings these accounts into view so that you can discover, monitor, and manage their access at every stage of the lifecycle.
Missing context in real-time decisions
Static logs and batch reports leave teams guessing. When a risky login or privilege escalation occurs, delays in detection give attackers time to move. With real-time context from identity systems, teams can flag anomalies early and trigger automated responses before damage spreads.
Compliance that's always playing catch-up
Audits, certifications, and access reviews shouldn’t require a scramble. A modern platform helps automate the governance process, from continuous policy enforcement to real-time reporting. That means fewer surprises and stronger alignment with evolving regulations.
How to start moving toward a modern identity strategy
For many teams, the shift to modern identity doesn’t happen simultaneously. Most organizations are still dealing with a mix of cloud services, legacy systems, and manual processes that weren’t designed to work together. And with limited time, talent, or budget, re-architecting everything overnight isn’t realistic.
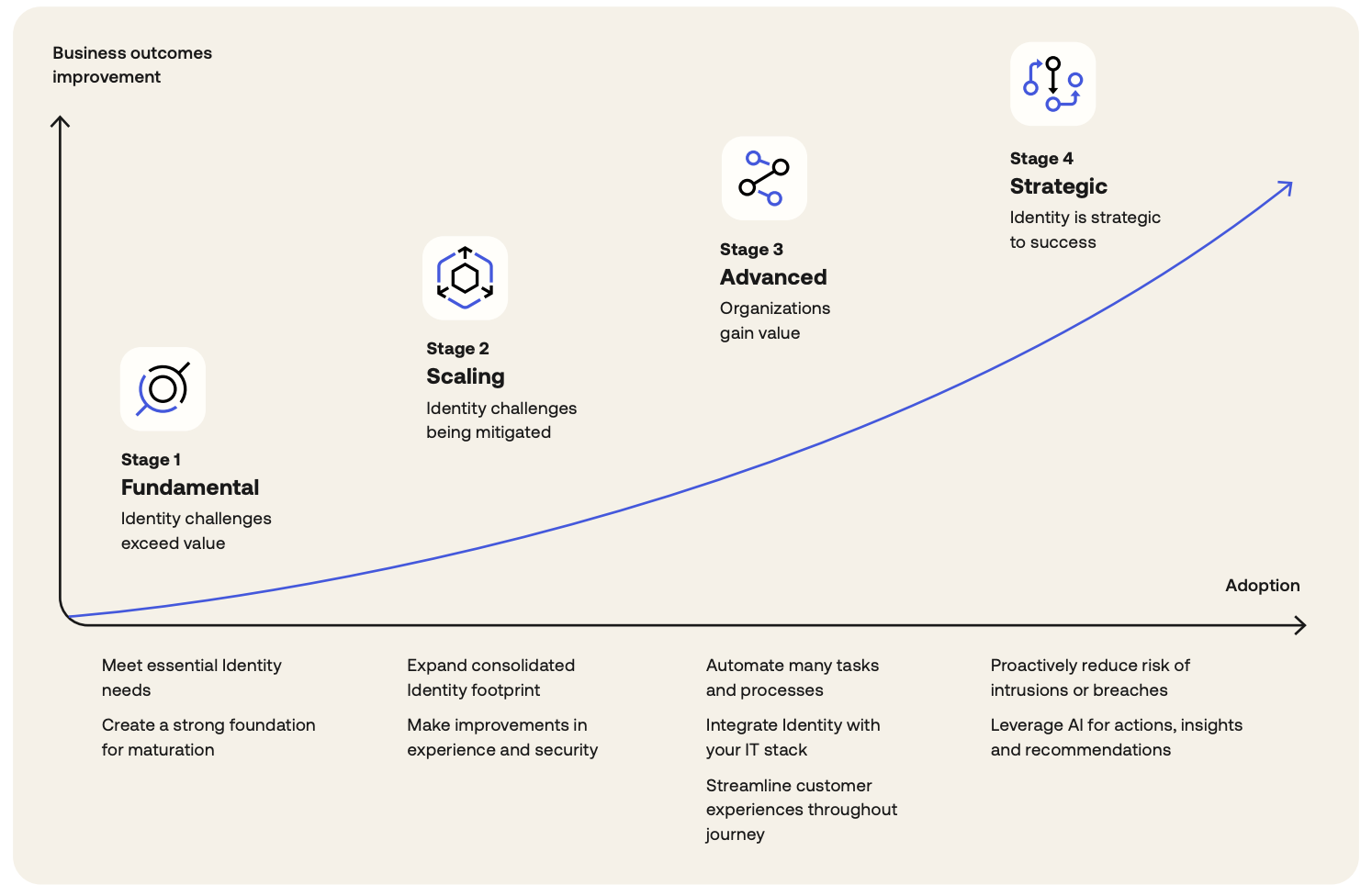
But progress doesn’t require a complete rebuild. The most effective identity strategies evolve in stages, not a single phase.
The first step is visibility. Before you can reduce risk or enforce policies consistently, you need a clear picture of every identity in your environment. That includes employees, contractors, third parties, service accounts, and machine identities. Knowing who has access, what they can reach, and how they’re authenticated creates the foundation for smarter decisions and faster responses.
Once that foundation is in place, automation is the next priority. Manual provisioning, one-off approvals, and static rules are hard to maintain and even harder to scale. By automating high-impact workflows like onboarding, offboarding, and access reviews, security teams reduce human error and regain time to focus on other strategic initiatives.
Integration is the third building block. A modern identity strategy depends on connectivity between your identity platform and the systems around it, including HR platforms, endpoint managers, cloud services, and security tools. When policies, authentication methods, and risk signals flow across the stack, identity can support enforcement in real time, not just during login.
It's important to note that none of this is guesswork. The Identity Maturity Model outlined in our Secure Identity. Secure Everything. provides a structured way to assess where you are today and what steps to prioritize next. Whether you're still in the early phases or ready to advance your architecture, the model helps identify gaps, chart progress, and align identity strategy with broader business goals.
Identity security starts here
To sum it up, the security landscape has changed, and identity is no longer an isolated system. It’s the layer that connects users, services, and infrastructure across your environment. The way you manage it now will define how well your organization can defend, adapt, and scale going forward.
Ready to move from fragmented tools to a more unified, resilient approach? Secure Identity. Secure Everything. is a great place to start. It lays out the core principles of a modern identity strategy, including how to assess where you are today and what steps to take next.
Download our identity security eBook today and take the first step toward an identity that strengthens your security posture.
Prefer to see it in action? Our on-demand webinar walks through real-world identity threats and shows how to stop them with better visibility, smarter enforcement, and faster remediation.






