As organizations adopt more cloud-based infrastructure and applications, identity has become a critical layer for protecting systems and data. Okta’s platform gives security teams the tools they need to help secure access at every stage of the user journey: before, during, and after authentication.
Capabilities like Identity Security Posture Management and Identity Threat Protection enable continuous evaluation and mitigation of access risks. This helps ensure that only trusted users, including non-human identities, can reach sensitive resources.
Okta goes far beyond SSO and MFA. It weaves core identity capabilities into a unified security layer that is orchestrated, integrated, and built to support any environment.
Okta Identity Security Posture Management
Before authentication begins, organizations must implement a continuous security posture and access governance model to ensure only the right identities are authorized and active.
Okta Identity Security Posture Management helps with identity visibility, management, and remediation. This delivers a “one-stop shop” for identifying and prioritizing identity risk. In addition, its contextualization capabilities show user accounts along with their required privileges, activities, and stages in the employee lifecycle to mitigate threats and support compliance.
Identity Security Posture Management’s identity graph engine connects to a variety of identity data, breaking the silos and building context-rich visibility. This empowers security teams to make decisions that will improve their overall identity security posture.
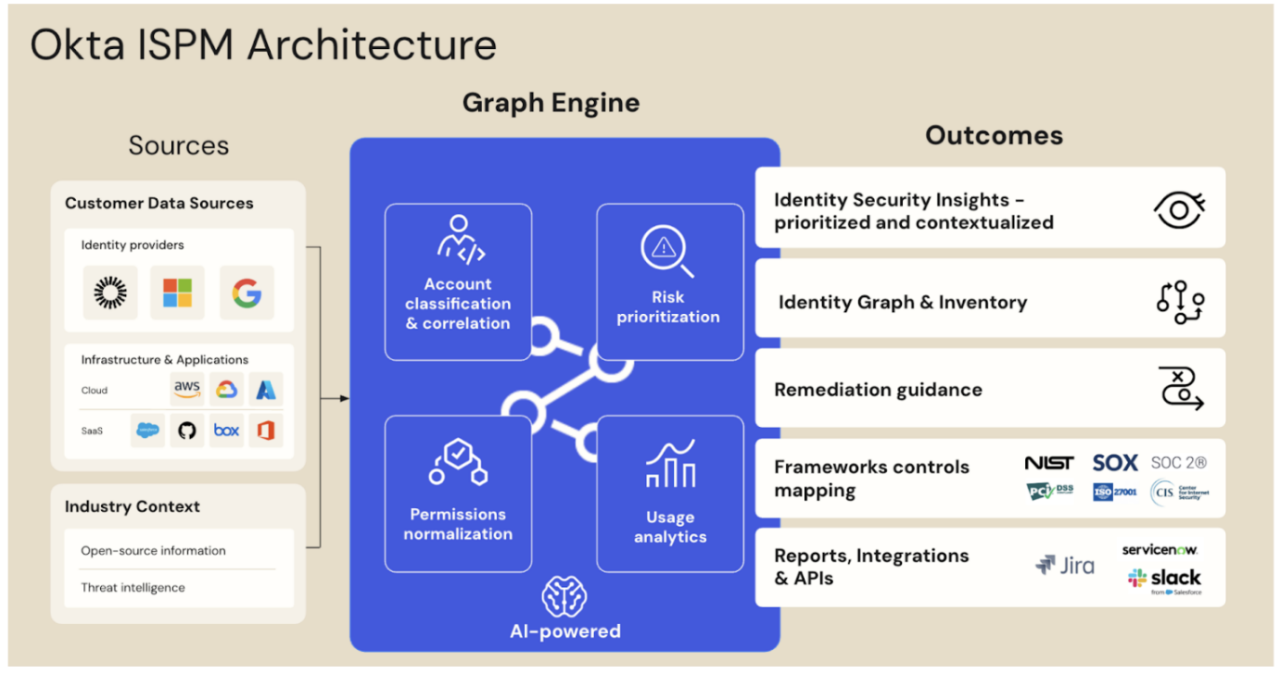
As organizations embrace multi-cloud and SaaS environments, security teams often struggle to maintain visibility and control over their identity landscape and identity security posture.
New challenges result in an increased attack surface and higher exposure to security breaches.
Fragmented identity data across multiple systems creates blind spots, making it difficult to identify and mitigate potential risks.
The proliferation of dormant accounts and/or the failure to de-provision accounts contributes to potential vulnerabilities.
Modern IAM solutions offer effective tools such as MFA and compliance frameworks to protect access, but customers lack the confidence that these are deployed properly.
Identity Security Posture Management empowers organizations to take a proactive stance to reduce their identity attack surfaces and addresses these challenges by providing:
A centralized view of identity security posture across their entire ecosystem
A proactive approach to detect vulnerabilities, misconfigurations, and policy violations
A fast path to prioritization and resolution of the most critical identity security issues, such as inconsistent MFA enforcement or excessive privileged access
Okta Identity Security Posture Management helps customers protect enterprise-critical assets and customer data across key aspects of the attack surface. The diagram below represents the key aspects mapping to the NIST publications.
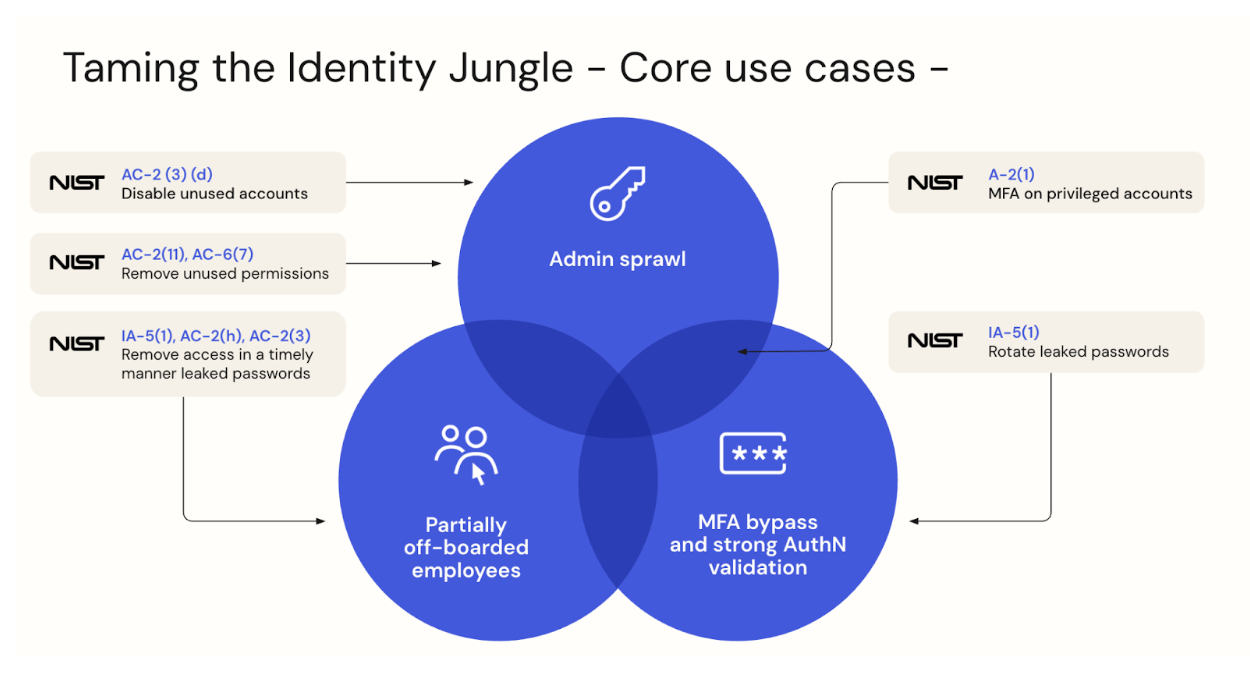
But Identity Security Posture Management doesn’t stop at identifying issues. With combined Unified Okta platform capabilities, Okta can automatically remediate them.
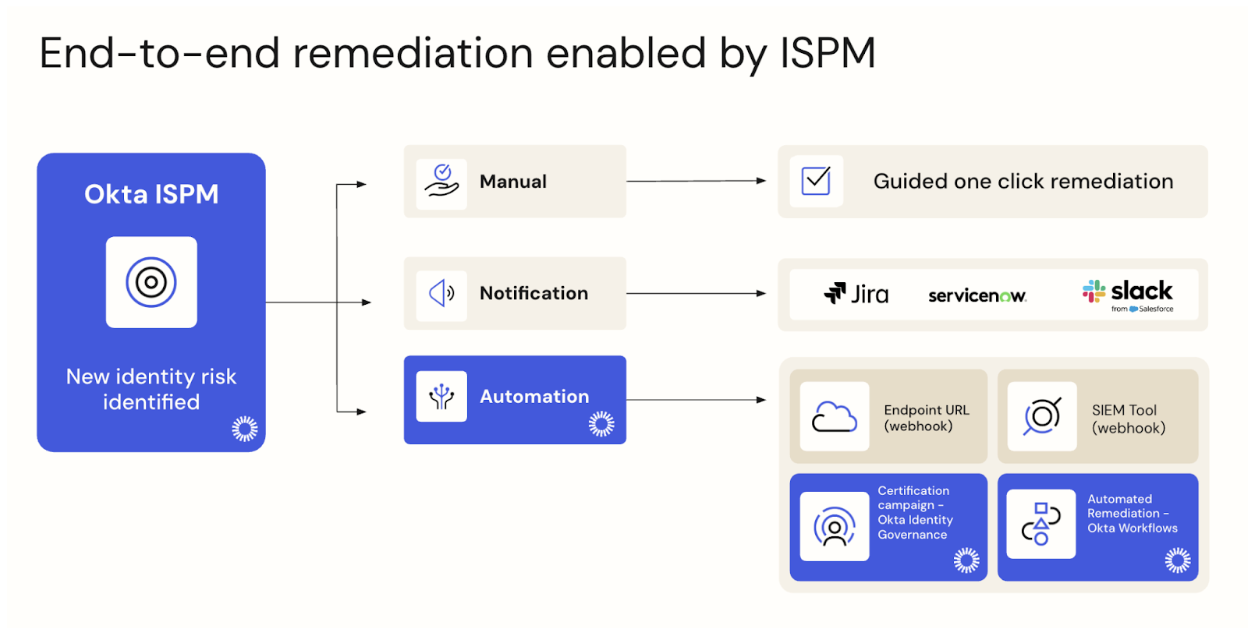
Okta Identity Governance
Okta Identity Governance strengthens pre-authentication posture with robust access governance controls. It enables:
Least privilege access by assigning only what is necessary, when it's needed
Just-in-time (JIT) access through automated provisioning workflows
Continuous access review of all entitlements to identify and remediate standing privileges
Policy-based deprovisioning to prevent orphaned or stale accounts
Together, Identity Security Posture Management and OIG ensure that access is tightly scoped, continuously governed, and risk aware — even before a user attempts to authenticate.
Okta authentication
The diagram below outlines how the Okta platform delivers defense in depth across every stage of access — before, during, and after authentication. Let’s take a closer look at how each layer works.
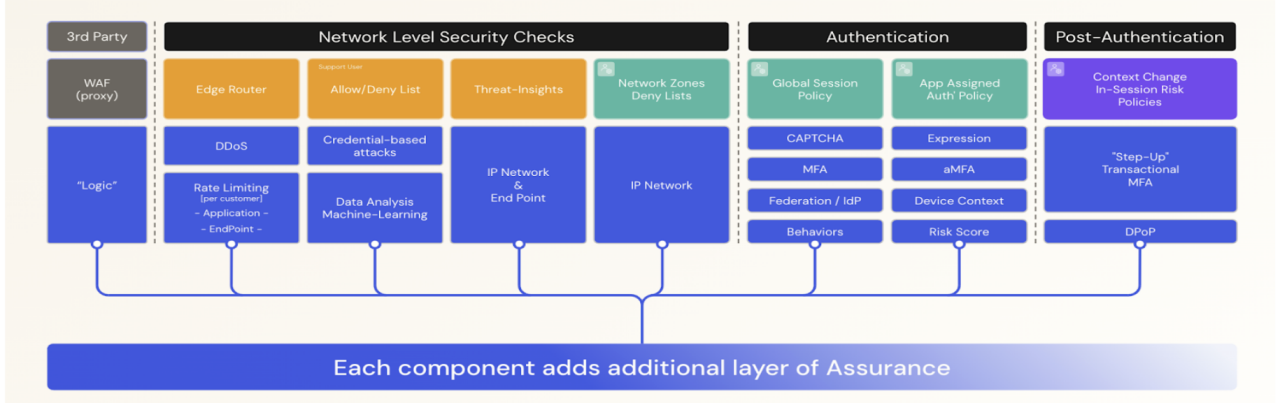
Before authentication: Strengthening defenses from the start
The security journey starts before a user even tries to authenticate. In pre-authentication, Okta applies network-level checks to block suspicious activity early and ensure only legitimate users can begin the authentication process.
Here’s how it works.
Edge router
At this layer, Okta enforces rate limits and provides built-in protection against Distributed Denial of Service (DDoS) attacks. Below is a breakdown of how the platform defends against DDoS threats.
Okta employs advanced techniques to help mitigate DDoS attacks.
AWS Shield Advanced integration: Okta utilizes AWS Shield Advanced for comprehensive DDoS detection and protection, covering infrastructure and application layer attacks, including HTTP floods.
AWS WAF for enhanced filtering: Okta employs AWS WAF for automatic filtering based on IP addresses, geographic blocking, and HTTP header information.
Multi-layered customer protection: Okta implements various protective measures at the cell/customer org level, including
Separate Okta cells, limiting the impact of DDoS attacks
Filtering of inbound URL requests at the web proxy level
Rate limiting to prevent DoS through resource utilization
Lockout detection caused by unknown devices
Rate Limiting: Okta APIs are subject to rate limits to protect the service for additional protection from bot attacks. These rate limits are enforced for each client, API endpoint, and org level.
Allow/deny list
Okta supports more than 19,000 customers and secures 10s of billions of logins every month, giving Okta broad visibility into identity-based threats across industries and environments. To enhance protection, the platform continuously monitors its global attack surface and uses anonymized signals to improve detection models. These insights strengthen Okta’s defense-in-depth approach without compromising customer data or privacy.
One of the key tools in this strategy is the dynamic allow/block list, which provides an additional layer of protection for all customers. By detecting threats in real time and adjusting security protocols accordingly, Okta helps ensure a proactive defense against a variety of cyberthreats, including credential stuffing, phishing, and brute-force attacks. This collective security framework strengthens the protection of every Okta customer.
Okta ThreatInsight
Okta ThreatInsight analyzes patterns in sign-in activity across the platform to identify potentially malicious IP addresses and help prevent credential-based attacks. This protection is powered by anonymized signals and designed to strengthen defenses without exposing customer data.
Examples of threats it helps detect and block include
Password spraying
Credential stuffing
Brute-force cryptographic attacks
Because ThreatInsight evaluates the origin of sign-in attempts across Okta endpoints, it helps establish a security baseline that benefits all customers.
Org-level network policies
A network zone is a configurable boundary that a customer can use to grant or restrict access to computers and devices in your organization based on the IP address requesting access. You can define a network zone by specifying one or more individual IP addresses, ranges of IP addresses, or geographic locations.
After you define one or more network zones, you can use them in Okta sign-on policies, app sign-on policies, VPN notifications, and routing rules to provide pre-auth decisions. For example, creating a block list will automatically block access from specific IP addresses or geo locations.
During authentication: Org-level policies during authentication are based on the context
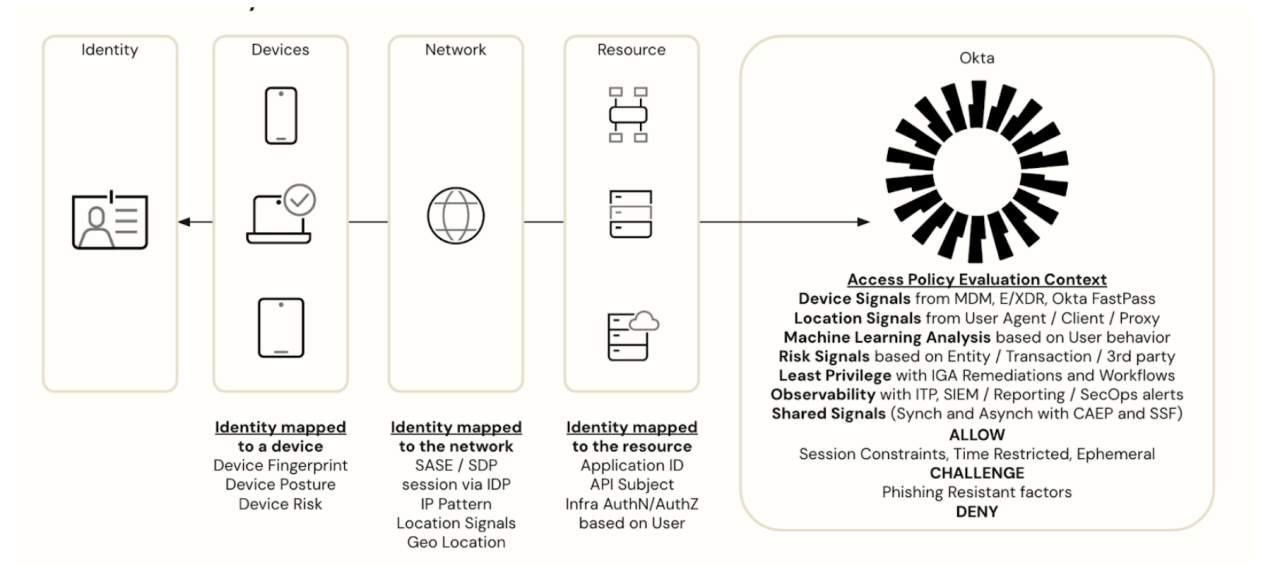
The above diagram is a reference diagram influenced by the CISA and NIST models. Now, let's look at a reference diagram that represents the ZTA through the lens of identity-powered security. At a high level, we want to control access from the assets on the left to the resources on the right, and we want that access to be underpinned by the capabilities on the bottom.
This architecture reflects the pillars of the CISA maturity model: identity, devices, networks, applications, and data. Automation, orchestration, visibility, and analytics span across all five.
With Okta serving as the identity control plane, security teams can leverage signals from identity objects and devices as they move through the network. We’ll explore how that works in the next section, where we check on two main policies within Okta during the authentication phase.
Global session policies
Global session policies provide the context Okta needs to determine the next step in the authentication flow. Once a user is identified, these policies evaluate multiple signals — such as device, network, user behavior, risk level, and the resource being accessed — to decide what action to take.
Actions may include allowing access, prompting for a challenge, or setting the time before the next prompt. Behaviors like sign-in velocity, new device usage, or unexpected geolocation are also evaluated during this phase.
You can configure global session policies to require any factors supported by your environment. Primary and secondary factor conditions in the policy rule determine which authentication steps are triggered.
All orgs have a default global session policy that applies to all users. Policies can be categorized by grouping users from high to low levels based on their access or the location they access from, for example, a trusted vs. untrusted network.
To further strengthen access decisions, the global session policy enforces the assurance level defined in the authentication policy for the specific resource being accessed. This ensures that users meet the required authentication standards based on the sensitivity of the resource.
Global session policy also controls Okta's global session management. Okta supports CAPTCHA services to increase org security and prevent automated sign-in attempts. You can integrate one of two providers: hCaptcha or reCAPTCHA v2.
The vendor implementations supported by Okta are both invisible. They each run risk-analysis software in the background during user sign-in to determine the likelihood that the user is a bot. This risk analysis is based on the settings you configure with your chosen provider.
Application authentication policies
Authentication policies enforce the factor requirements when users sign in to apps or perform specific actions. While these policies share some conditions with global session policies, they serve distinct purposes. Users who gain access to Okta through the global session policy do not automatically have access to their apps.
You can create a unique policy for each app in your organization or create a few policies that can be shared across multiple apps. Additionally, Okta provides preset policies for apps with standard sign-on requirements. If you need to change an app's sign-on requirements later, you can easily modify its policy or switch to a different one.
Application authentication policies are based on several contexts within Okta. Let’s dive into each section below.
Okta Adaptive MFA
As user and risk levels continually evolve, your security should adapt accordingly. Okta Adaptive MFA allows for dynamic policy changes and step-up authentication in response to changes in user behavior, device context, location, and other factors. Adaptive MFA supports detection and authentication challenges for riskier situations such as:
- Use of weak or breached passwords
- Proxy usage
- Geographic location or zone changes
- Brute force and denial-of-service attacks
- Use of new or untrusted devices
- Indicators of anomalous behavior
Okta supports a broad range of multi-factor authentication (MFA) methods, aligned with NIST assurance levels. These include possession factors, biometric combinations, knowledge factors, and blended approaches. The table below categorizes each factor by type.
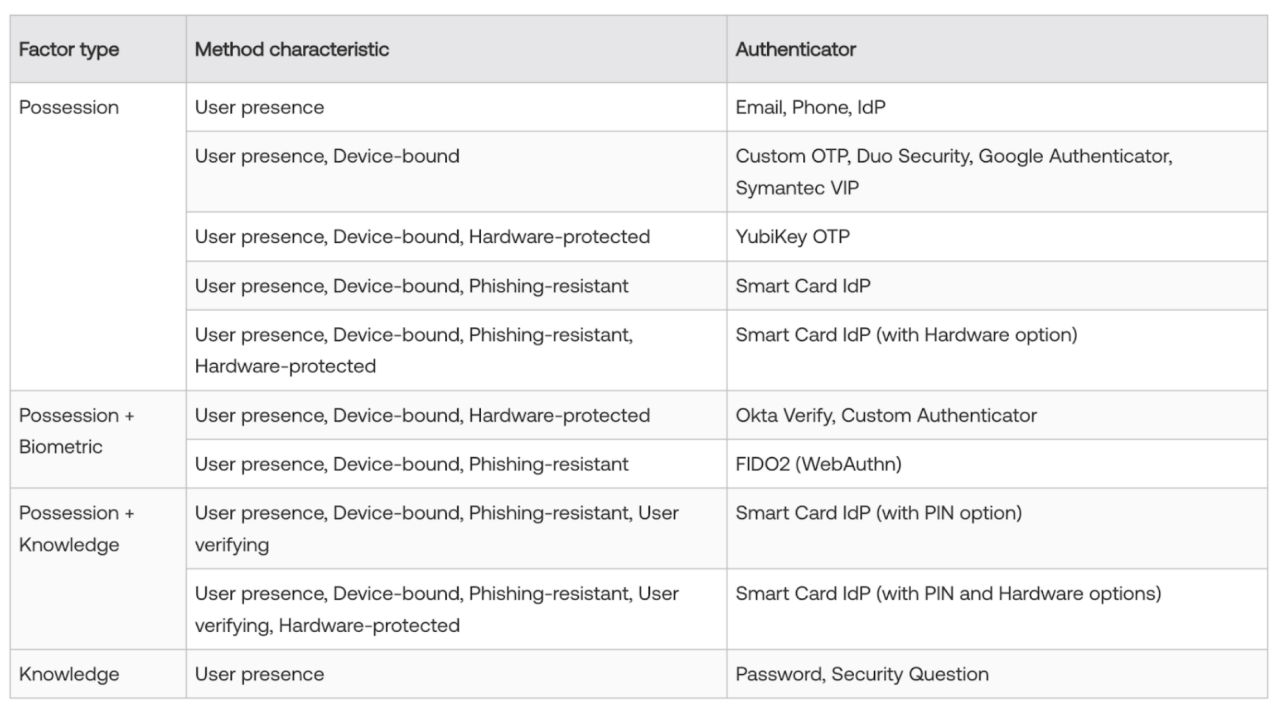
Authentication factor characteristics
Authentication factors can be categorized based on their method characteristics:
Device-bound: tied to a specific device
Hardware-protected: require a physical device for authentication
Phishing-resistant: prevent the sharing of authentication data, protecting users from phishing attacks. For more, see Phishing-resistant authentication and Okta’s phishing resistance solutions.
User presence: require human interaction.
User-verifying: confirm the identity of the person authenticating.
Okta FastPass is a phishing-resistant, passwordless authenticator that ensures secure access to Okta-protected apps. As an Okta Verify client installed locally on a device, Okta FastPass acts as a device-bound authenticator that continuously monitors for potential threats. It determines whether a device is managed or unmanaged based on device validation through Device Assurance and Device Trust features.
FastPass can also enforce device hygiene policies for non-managed devices to ensure secure access to corporate applications. Additionally, it integrates with Endpoint Detection and Response (EDR) signals, collecting and sending them to Okta for evaluation during the sign-in process.
Okta Device Trust contextual access management solutions enable organizations to safeguard sensitive corporate resources by allowing access only from trusted, managed devices. With the disappearance of traditional corporate perimeters, users now access applications from various clients, platforms, and browsers.
As part of Okta's Zero Trust security model, Device Trust ensures users access applications from trustworthy devices. Managed devices are considered to have higher trust, requiring minimal assurance, while non-managed devices require a higher level of trust.
With Device Assurance policies, you can check sets of security-related device attributes as part of your authentication policies. For example, you can configure a policy to verify whether a specific operating system version or security patch is installed before allowing access to Okta-protected resources. Integrating device checks into your authentication policies allows you to set minimum security requirements for devices attempting to access your organization's systems and applications.
You can integrate Okta Verify with your organization's EDR solution. When users attempt to access a protected resource, Okta Verify probes their device for context and trust signals. These signals are then evaluated against the authentication policies configured in the Okta Admin Console. This integration extends device posture evaluation by leveraging signals captured by your EDR client running on the same device.
Application policies define the level of assurance a user must meet to authenticate into a specific resource. These policies are based on in-depth integrations and various factors, such as user identity, device type, and geolocation.
After authentication: Continuous monitoring and Identity Threat Protection
The battle doesn’t end once the user is authenticated. In the post-authentication phase, Okta continues to monitor user activity, applying identity threat protection (ITP) strategies to detect and respond to ongoing risks.
Continuous monitoring
Okta continuously monitors identity signals after authentication to detect anomalies. This includes changes in user behavior, such as unexpected access attempts or deviations from typical usage patterns, helping security teams respond to threats in real time. If anomalies are detected, Okta can trigger automatic remediation actions, such as universal logout, or run a workflow to temporarily lock the account for further investigation.
Identity Threat Protection
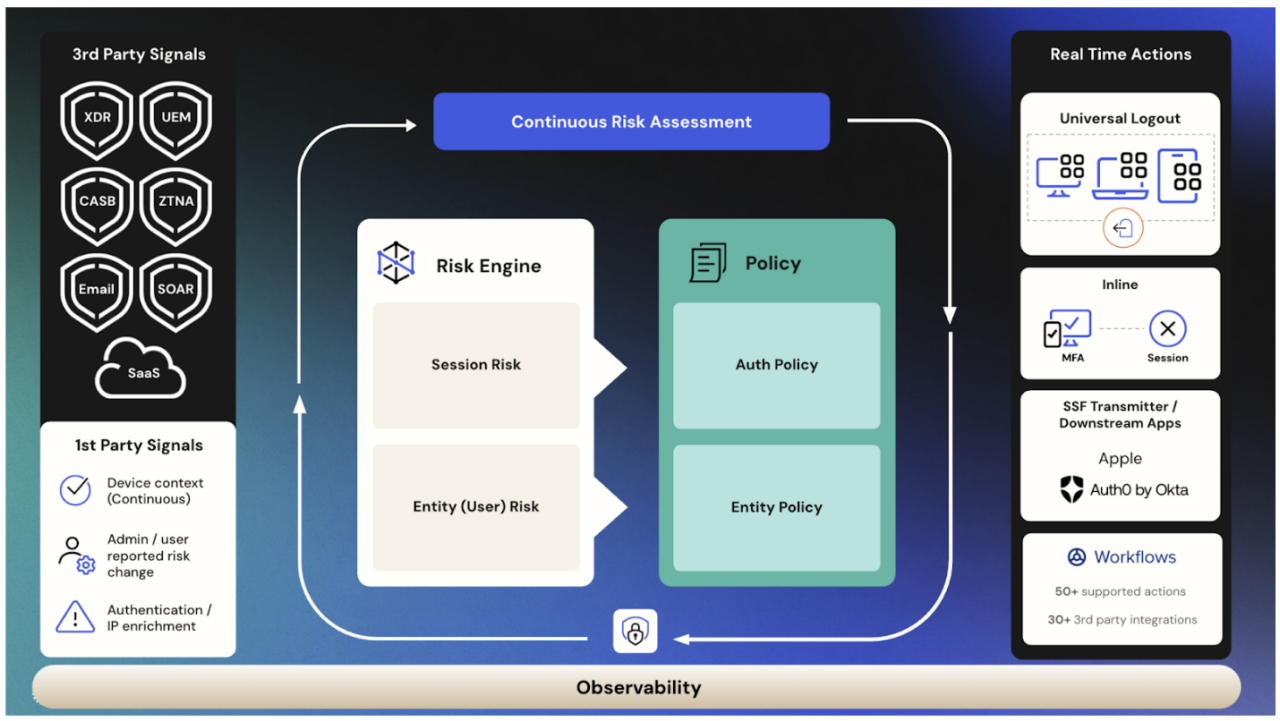
In today’s digital world, identity security is critical, and Identity Threat Protection from Okta offers a dynamic, user-focused approach. At its core, from the diagram above you can see Identity Threat Protection collects third-party signals from a variety of threat surfaces (e.g., endpoint, ZTNA, email) and first-party signals from Okta platforms like Okta Verify. This helps continuously assess the risk and monitor for any changes in context that might indicate a security threat.
The risk engine plays a crucial role by evaluating session risks during login and analyzing factors like IP and device context. But it doesn’t stop there. Identity Threat Protection tracks a user’s overall identity through entity user risk, which encompasses the user’s risk profile across all touchpoints, including device, application, network, and data. This holistic approach is akin to a credit score, assessing the overall risk of a user based on native and third-party risk signals like malware or account takeovers.
On the right side of the system, policies dictate specific actions based on real-time risk assessments. These can include universal logout or step-up MFA for higher-risk scenarios and streaming risk context downstream using the same Shared Signals Framework (SSF).
With the SSF, you can configure a shared signal receiver integration with security events providers to inform your users' entity risk detection settings for an entity risk policy. This allows the security events provider to transmit risk signals to Okta. You can uncover more potential identity threats by receiving risk signals from security event providers.
A holistic approach to cybersecurity
Okta’s Identity Security Fabric is a modern, orchestrated approach to cyber defense built to protect every phase of the identity lifecycle, starting long before a user authenticates. It begins with governance and Identity Security Posture Management, establishing least privilege, enforcing just-in-time access, and continuously reviewing entitlements to eliminate standing privileges and reduce attack surface. This proactive posture ensures only the right identities exist, and only when needed.
From there, authentication is context aware and adaptive, powered by strong policy frameworks, phishing-resistant methods like FastPass, and granular device and session intelligence. Access decisions are not static; they reflect real-time context, risk levels, and trust signals across users and devices.
Security doesn't stop after sign-in. With Identity Threat Protection, Okta continuously monitors post-authentication activity, correlating risk signals across the environment and enabling automatic remediation for suspicious behavior — whether that means enforcing step-up authentication, revoking access, or triggering security workflows.
These capabilities are not isolated controls — they function as an interconnected identity security fabric. Governed access, secure authentication, and continuous monitoring work in concert to deliver a resilient, scalable, and intelligent layer of defense.
In a world where identities are the new perimeter, Okta empowers organizations to make identity the foundation of their security strategy, providing the visibility, control, and adaptability needed to secure access across today’s dynamic and distributed environments.






