In today's environment of sophisticated phishing and deepfake attacks, relying on a password and multi-factor authentication (MFA) is no longer enough. Organizations need to assert a user's real-world identity, especially during critical moments like account onboarding and password recovery.
Consider these scenarios:
- To secure new-hire onboarding, you need to verify that the remote employee who receives and signs in to a company-issued laptop is the same individual who was hired and authorized for access.
- In financial services, a new high-value client needs to be onboarded. You must confirm their identity with certainty before they can access their account and make transactions, preventing a fraudster from using stolen credentials.
- In healthcare, a patient tries to reset their portal password to access sensitive medical records. A simple password reset might be too risky, requiring a liveness check to prevent a fraudster from gaining access.
- For an e-commerce marketplace, you need to ensure the person applying to be a seller is who they say they are, matching their real-world identity to their business registration to prevent fraudulent sellers from joining your platform.
- Citizen-facing government agencies, such as those who handle unemployment benefits, need high assurance that new applicants are who they say they are to quickly approve new claims during a surge (e.g., furloughed federal employees during a government shutdown).
Enter identity verification (IDV). For organizations that require a specific vendor or an in-house solution, Okta provides the flexible framework necessary to integrate almost any IDV solution.. This helps organizations reduce fraud, streamline onboarding, and deliver secure, user-friendly digital experiences.
What is IDV?
IDV helps ensure that the person presenting the information is the rightful owner of that identity. This process typically involves various methods, like document verification, liveness checks, biometrics, fingerprints, knowledge-based questions, and more. Identity verification adds an extra layer of assurance in every user interaction.
How does IDV work in Okta?
Okta’s bring-your-own IDV provider (BYO IDV) capability uses a standard that delegates the heavy lifting of document checks, liveness detection, and data matching to IDV vendors. This gives you the flexibility to choose your own vendor or integrate an in-house solution that meets your needs. The benefits of this approach include:
- Specialization: Okta handles security policy, while the third-party vendor handles their expertise of ID verification.
- Standardization: The connection uses OpenID Connect (OIDC) and Pushed Authorization Requests (PAR) for secure, reliable communication between Okta and the IDV vendor/solution.
High-level IDV flow
Wondering how this process works under the hood? Here’s a high-level look at how Okta orchestrates an identity verification flow from start to finish:
- The admin adds an IDV vendor as an identity provider: Then the admin configures it in the Okta Account Management Policy.
- Trigger the Okta Account Management Policy: The user attempts an action that triggers an Okta Account Management Policy (e.g., enrolling a new authenticator, self-service password reset, or unlocking an account).
- Okta-initiated request: Okta identifies that the policy requires identity verification. It securely sends a request (POST /oauth2/par) containing the user's ID and required verification parameters, such as first name, last name, and more, to the IDV vendor’s authorization server.
- User redirect: The IDV vendor responds with a session URI. Okta uses this to redirect the user's browser from the Okta sign-in page and to the vendor's dedicated verification flow.
- Verification: The user completes the verification directly with the vendor.
- Vendor response: Upon completion, the IDV vendor sends a response back to Okta. This response contains the status of VERIFIED or FAILED.
- Okta policy evaluation: Okta evaluates the assurance level returned by the vendor. The policy is then marked as VERIFIED or FAILED, determining whether the user can proceed.
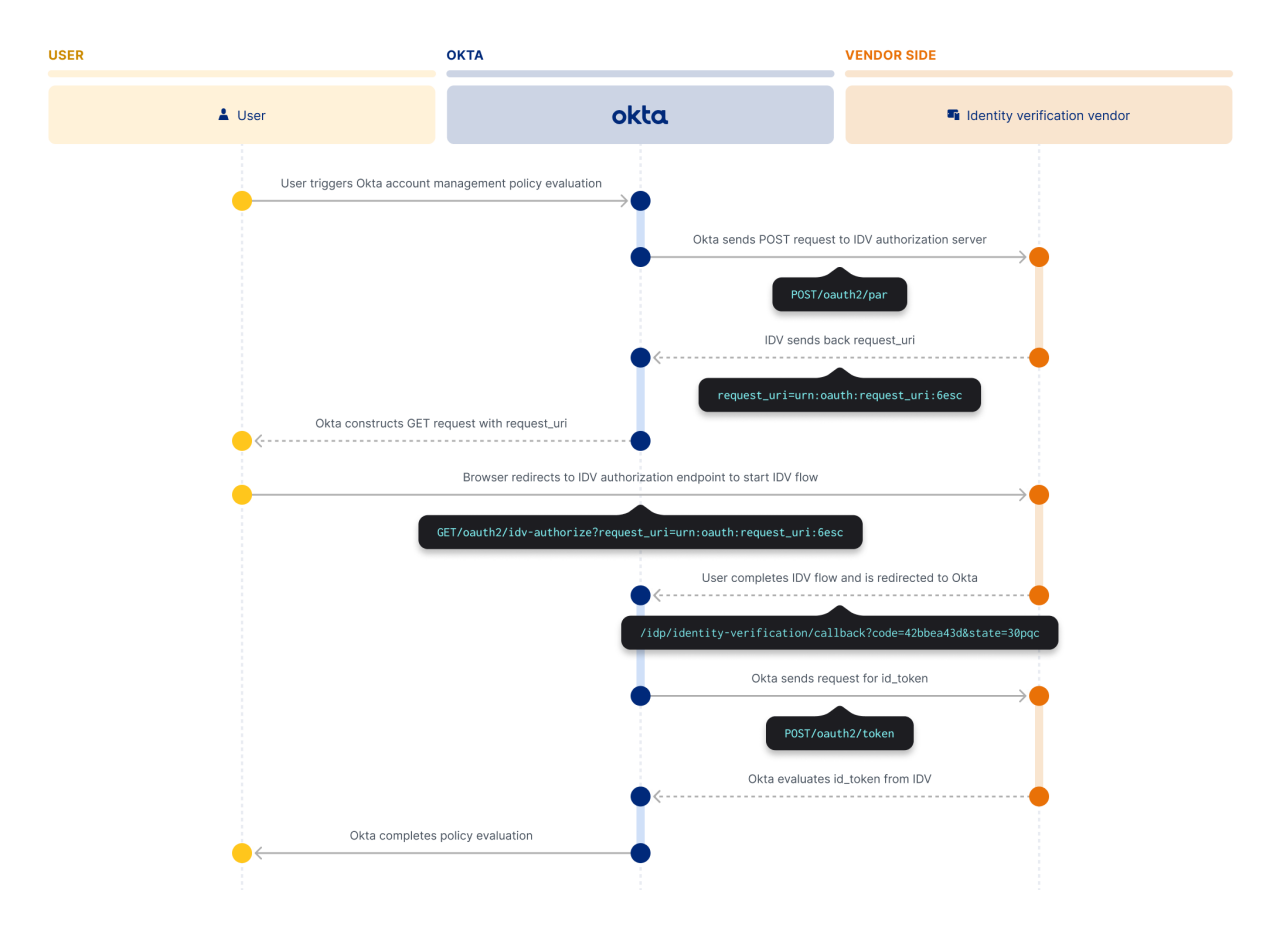
As an extra layer of assurance, Okta enables administrators to map user attributes (claims) from the Okta Universal Directory to the IDV vendor to facilitate accurate matching and verification, and then map the vendor's assurance result back to the user's profile for evaluation.
This allows security teams to require a high-confidence ID check to secure critical moments like new employee onboarding, self-service account recovery, and MFA factor enrollment, helping to ensure the person accessing the system is the legitimate user and not a fraudster.
Furthermore, Okta provides the flexibility to configure multiple IDV vendors, which means an organization can tailor the experience by region — for example, directing new hires in North America to vendor A while those in APAC are routed to vendor B — ensuring seamless and compliant onboarding globally.
For more information, check out our documentation on how to integrate Okta with identity verification vendors.
Getting started
Customers with MFA or Adaptive MFA can leverage Okta's BYO IDV offering today. This allows you to integrate identity checks from any compliant third-party vendor or in-house solution directly into the Okta Account Management Policy.
Resources
For more information, check out the following video:






