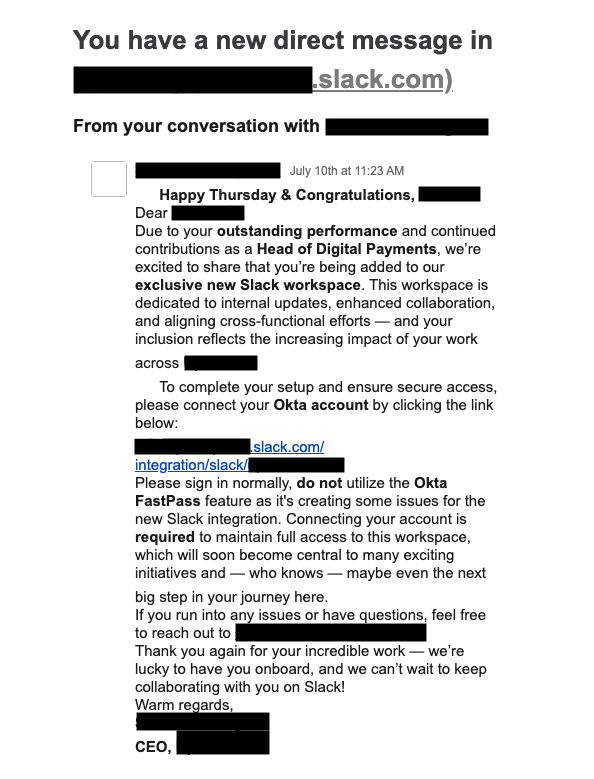
“Please sign in normally, do not use the Okta FastPass feature.”
This unusual instruction, delivered to targets of a recent social engineering campaign observed by Okta Threat Intelligence, offers a look into how cybercriminals are evolving their tactics in response to higher adoption of advanced, high-assurance sign-in methods.
During the observed phishing attacks, attackers impersonated a company CEO and tried to convince targeted users to evade security measures the company had in place. The campaign abused trusted instant messaging communications channels (in this case, Slack) to deliver lures to targeted users.
The security contacts at Okta customers can access a detailed threat advisory about this phishing campaign once they authenticate at security.okta.com.
Why do attackers have an opinion on your sign-in method?
The choice of sign-in methods (“authenticators”) you offer to users really matters.
The phishing lures we observed directed targeted users to visit phishing pages running Evilginx, an adversary-in-the-middle (AitM) transparent proxy.
These phishing kits can be used to pass a legitimate authentication request through attacker infrastructure, allowing the attacker access to both user passwords and any form of One Time Passcode (SMS, TOTP, etc.) required to access the resource. The phishing pages can also be configured to capture the session token returned to a user browser when they sign-in via these proxies.
AitM phishing kits are not effective, however, against organizations that implement strong, phishing-resistant authentication methods and enforce phishing resistance in policy.
When administrators enforce phishing resistance in an authentication policy rule, a user can only access the protected resource using Okta FastPass, FIDO2-based authentication or PIV Smart Cards. These sign-in methods will not allow access if the request is routed through a transparent proxy. Users can’t be tricked into selecting any other sign-in method.
In the past, we’ve also observed attackers attempting to convince privileged users to physically remove their FIDO2 security key, in the hope that authentication policies may still allow access using a less secure alternative. In more recent attacks, phishing actors have directed users enrolled in FIDO keys to sign-in pages that trick them into thinking their key is defective, again in the hope the user will manually choose a factor that is not phishing resistant. These “MFA downgrade” attacks are only possible if the user is enrolled in weaker forms of authentication and phishing resistance isn’t required in policy.
Some advanced authentication methods can go above and beyond what FIDO2 can achieve. For example, when phishing resistance is enabled in policy, FastPass both prevents the user being compromised and also creates a detection event in Okta System Log that can be used to identify if any other users have interacted with the phishing kit. It also checks device context whenever an attacker attempts to replay a session token stolen using infostealer malware from a different device. When combined with Identity Threat Protection, FastPass can automatically invoke a “Universal Logout” event, signing a compromised user out of downstream apps and, if desired, their device.
So if I enroll users in phishing-resistant authenticators, am I in the clear?
If all your users are enrolled in phishing-resistant authenticators, you’ve done most of the work.
The next thing you need to do is to ensure that phishing resistance is enforced in policy. This involves configuring each authentication policy rule to specifically require phishing resistance.
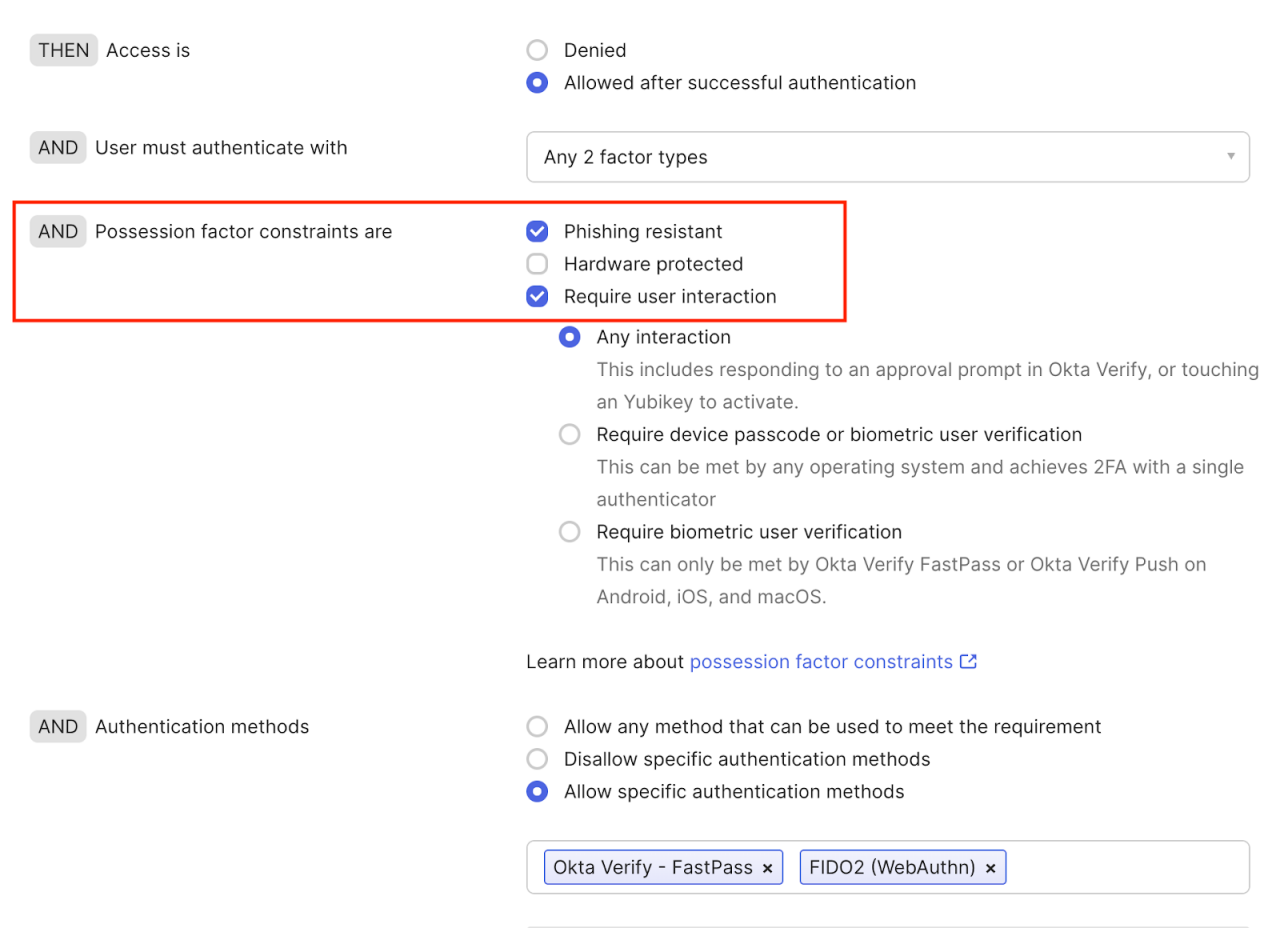
Okta Identity Engine also allows administrators to allowlist (or deny) specific authentication methods in policy rules.
For information on how FastPass enforces phishing resistance across different operating systems and browsers, check out the Okta FastPass Technical Whitepaper.
If you are confident your users no longer require weaker forms of authentication (knowledge-based factors, SMS etc), we recommend they are either disabled or restricted to specific, low risk scenarios where compensating controls can also be applied.
To access the detailed threat advisory about this social engineering campaign, the security contacts at Okta customers can sign-in to the Okta Security Trust Center.







