Oktane19: How Priceline Drives Efficiency, Simplicity, and Security by “Okta-fying” Everything
Transcript
Details
Michelle B.: My name's Michelle, and I'm integrations manager at Okta. I'm part of a cross-functional team that brings you the Okta Integration Network, and when I first heard about Joe's story at Priceline, I thought, "What a great example of the Okta Integration Network in action."
Michelle B.: Joe is using Okta in many different ways, connecting to many different technologies, to solve important use cases. So, in this session, I will begin by sharing some examples of integrations I've helped deliver into the Okta Integration Network, then I'll hand it over to Joe. He'll give you even more examples of integrations that are important to Priceline and to Priceline's business.
Michelle B.: The Okta Integration Network includes more than 6,000 integrations and growing. Since last Oktane, we've delivered more than 150 new SAML integrations, more than 60 new SCIM provisioning integrations, and more than 40 advanced integrations to the Okta Integration Network.
Michelle B.: So, why is it that we spend time, resources, and effort bringing these integrations to you? It's because doing so is absolutely core to Okta's mission to enable any organization to use any technology.
Michelle B.: And how do we find out about the integrations to bring to you and to the Okta Integration Network? We work with you, our customers. You come to us with important questions for your business and your IT environments, and it's my hope that you'll find the answers in the Okta Integration Network.
Michelle B.: For example, many of our customers are looking to easily and secure provision and deprovision users, and Okta can do that. We integrate with any cloud application because we were born and built in the cloud, but it doesn't stop there. It's very easy to extend Okta's SCIM provisioning capabilities to on-premises applications as well so that you can use Okta to manage user access no matter where your application resides.
Michelle B.: In addition, you can enhance security. We all know that Okta comes with myriad security benefits, and myriad security controls, but if you're looking to extend security in other areas, Okta can help you with that, too.
Michelle B.: I recently worked on an integration with a email tool called Proofpoint, and this integration is really cool. Proofpoint can detect when a user has clicked on a malicious email, link, or attachment, and then can automatically trigger Okta to step up security, including provide multi-factor authentication for affected users.
Michelle B.: And what this means is, you're authentic users can easily get the access they need with a second factor, but the malicious attacker will not be able to gain access without that second factor.
Michelle B.: In addition to integrations with email security tools, Okta also integrates with endpoint management solutions that you may know, including VMware, MobileIron, JAMF, and IBM MaaS360. With these integrations, what you can do is add information that Okta knows about the user without information that you know about your devices so that you can make intelligent access decisions.
Michelle B.: And Okta has products that go beyond securing your workforce. You can put Okta to work in your customer applications as well. Why build your own authentication system, when you can use Okta to do that? And once you have Okta in place inside your customer app, managing user registration and authentication, you can integrate it with other tools.
Michelle B.: For example, you can add an identification verification step into your user workflow. This means that you can integrate Okta with tools like Jumio, Trusted Key, Experian, Accuent, and Evident, and you can have the user participate in this by providing a copy of his or her driver's license before you grant them permission or certain permissions to your application or platform.
Michelle B.: Or, you can do some checking behind the scenes. You can take information provided by the user during registration and validate that against a collection of authoritative data sources. And beyond that, if your application is under attack by malicious bots, Okta integrates with popular bot detectors, like Distill Networks, Shape Security, and PerimeterX. So this way, using Okta in those integrations, you have a double layer of defense against bad bots.
Michelle B.: Those are just some of the examples of the integrations available to you in the Okta Integration Network. You have questions that are important to your business, and again, it's my hope that you will find the answers in the Okta Integration Network.
Michelle B.: So there is a lot that Okta can do for you, and when I first met Joe, he called this flexibility of Okta, Oktify. And with that, I'd like to bring up Joe to give you examples of the way he's using Okta at Priceline.
Joe Dropkin: Good afternoon. I want to thank Okta for giving everybody a tryptophan sandwich right before my presentation. That's really appreciate.
Joe Dropkin: A little about myself. I have a basic philosophy that when I work with a software vendor, I need to be in a partnership with them. It needs to be something I want to use, and something that they want to help me use. If you are not enjoying working with your software vendor the way I enjoy working with Okta, then you're using the wrong software. It doesn't matter, Okta, anything you're doing. You need to have a partnership, because in the end, it's making your job easier.
Joe Dropkin: And to that, it's payback time with Okta. Is that a vendetta? No, quite the opposite. We bought Okta almost three years ago, and what we were looking to do was simple. Single sign on, we were moving to G Suite, and we wanted an identity provider. What we learned over the course of the years is that there's a lot more that Okta's doing for us that we had no idea was even possible.
Joe Dropkin: I'm the principal engineer at Priceline.com. What does that mean? Well, it means I sort of take care of a lot of everything. Stuff bubbles up to me. But a lot of my responsibility revolves around identity management, security, remote access, our new foray into zero trust.
Joe Dropkin: And for those of you that haven't heard of Priceline.com, well, maybe you've heard of our affiliate companies. We're all under Booking Holdings. So you've heard of Booking.com for those of you in Europe, OpenTable and Kayak for those of you that don't get out of California at all, and Rentalcars.com is over in the UK, and Agoda is over in Thailand.
Joe Dropkin: And I point this out to show that we are a global organization, and one of the things that we do is we let each of these organizations do their own thing. But sometimes, we also come together and we have joint projects, and we'll get into that on how Okta has helped with that.
Joe Dropkin: So, when we first got Okta, we bought professional services with it as well. Nobody told me this. But that's okay. Professional services called me about a month into our contract and says, "Okay, we're ready to get you going. Let's take a look at your tenant." And I said, "Well, for what? I've got about 30 applications going."
Joe Dropkin: Why? Because most applications can be done in about five steps. It is super-easy to implement. Not only is it easy to implement because there's not much to it, but Okta has done a great job of providing the users with an instruction sheet that says, "Go here. Click here. Upload your XML data. Have a nice day." It's really that simple.
Joe Dropkin: So I want to talk to you about four big wins that we've had at Priceline. We're going to talk about single sign on, diluted to one real reason we bought Okta to begin with. We're going to talk about source of truth, getting workday, and Active Directory, and everybody up to date, and making sure that everybody's titles and managers and all that information that seems to come from multiple sources really has some meaning.
Joe Dropkin: I want to talk to you about lifecycle management. How do we provision user licenses? How do we deprovision user licenses? What does that really mean?
Joe Dropkin: And then what I talked about, the global nature of Booking Holdings, that we are many companies and we have projects from time to time that need everybody connected from multiple resources.
Joe Dropkin: So our first thing. We have multiple teams with multiple projects, multiple implementations. Everyone wants their own solution. Well, what does that mean? That means that I want to build an app over here, and I want to build an app over here, and well, you have to authenticate to my app using these credentials, and this one needs its own LDAP lookup account, and this one can't handle multi-directory.
Joe Dropkin: So what did we do? We Oktafied. You point your developers to developer.Okta.com. They create a sample account. They get access to the Okta code, which is somewhere between five and 10 lines, and it's written in React, in Perl, in ... Those of you holding out for .Net. It's still relevant to some of you, that's okay. But the point is, Okta is providing all these resources so you can take whatever you're writing, take a snippet of code, and all of a sudden, now you don't have to worry about identity management. It's all taken care of in Okta.
Joe Dropkin: You get faster deployment. You have better security. The worst thing that your security department fears is, somebody set up a new application and they're not following the security protocols. Says you have a 16-character password. Well, we set up this new application, and it only has single-factor authentication, and it only requires eight characters, and your password can be "password." No!
Joe Dropkin: Okta allows you by pointing all your resources to a single source to maintain your security policies, and on top of it, you can add MFA. The idea that you can MFA to basically any application is a game-changer, because now you can say, "Look, this application is now under PCI." Okay, boom, we added MFA to it. Now it's secure. That's how easy it is.
Joe Dropkin: And with that, what do you get? Well, with a straight Active Directory authentication, you usually get a user name. With Okta, you get the full display name, you get to their email address, you know where they're coming from, you know their operating system, you know their browser version, and what they're using. You see more information about your users. We all just dealt with the Chrome zero-day vulnerability.
Joe Dropkin: Now, there are lots of ways you can chase down your users. Or, you can run a straight report that says, "Show me all the users that were authenticating with a version lower than this." Okta provided that support. It was very easy. You're not going to get that from Active Directory.
Joe Dropkin: Win number two, Workday as a master. There are many ways to implement Workday into your Okta environment. The textbook way is to just let Workday do everything, and it's going to create accounts, and it's going to put the users in their OUs, but the problem is is that our HR department has all the people info, and our IT department really wants to hold onto Active Directory. No one trusts the other.
Joe Dropkin: Fair enough. Your HR people, you don't want them making a change that may accidentally lock somebody out of their computer, and you don't want IT being able to change anything in Workday that may screw up HR.
Joe Dropkin: You Oktafy. Human resources controls all the people details, IT controls everything else. What does this do? This allows you to bring in the information from Workday into Okta. It syncs with Active Directory for title and manager, your phone number, office location, but you're not syncing stuff like account information that could affect the end user if that was not hired properly by non-IT folks. All of that data syncs into all of your cloud apps. Slack, GitHub, Zoom, whatever you're using, and it syncs into your on-prem apps that can handle that information because you sent your developers over to developer.Okta.com to pull in all of that information.
Joe Dropkin: Everything is kept up to date. Everyone knows everything. And everyone's happy.
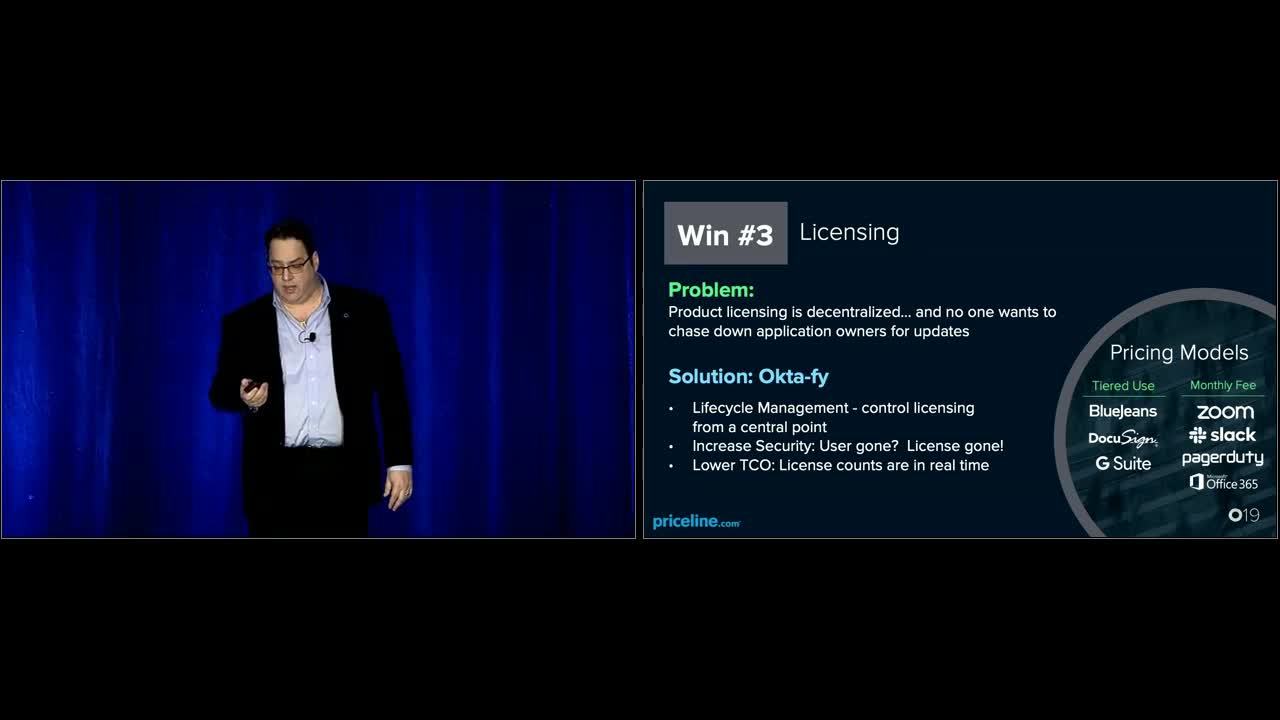
Joe Dropkin: Third win, licensing. Nobody likes a true up. Well, except for the sales guys over there in the corner. True ups are going to kill you if you do not keep track of your users properly. Okta Lifecycle Management allows you to keep tabs on all of your licenses in one place. Your problem is that you've got 30, 40, 50, whatever it is, number of Sass applications, and each of them is licensed by user. And when a user comes on board, you've gotta provision that license. When a user leaves your company, you gotta go around to all of those applications and you gotta make sure that you've removed that license and removed that access.
Joe Dropkin: With Lifecycle Management, you've Oktafied. You deactivate that user or you remove them from particular AD groups, whatever level you want to do. It automatically controls the licensing and you get accurate counts. This is going to go for any app that Okta has provisioning with such as Slack, PagerDuty, Zoom, G Suite, Office 365. Nobody wants to be paying extra licenses for Office 365. It's expensive and if you can avoid paying in jumped license costs because, wow, we onboarded 200 people in the last six months, but we forgot to deprovision the people that left. No, you want a smooth license count. You want your license count to reflect exactly the number of users that you have.
Joe Dropkin: Licenses are recycled properly. You're not wasting money. And this is one of the ways that Okta has shown to us a real return on investment, being able to pay for itself by not overpaying for licenses in other place, or for the people power that it takes to chase down all of that information.
Joe Dropkin: The last one that I want to talk to you about is really huge for us. I'm going to give you an example. We had a project with one of our affiliates with Agoda, and they needed to be able to get into our Tableau environment. And our Tableau environment was accessible from the Internet, so that wasn't a problem, but it was only capable of looking at a single source for authentication.
Joe Dropkin: And the problem was, we couldn't just set up another link, and we couldn't ... As I said, it could only handle a single source of identity, so what did we do?
Joe Dropkin: We Oktafied it. We didn't have to rely on an Active Directory trust. We didn't haven't to worry about recursive searches, doing a double-L DAP dip. We were able to use Okta's ubiquitous support for OpenLDAP, Active Directory, Universal Directory, and the biggest thing is, we allowed admins to control their own users. So what did we do?
Joe Dropkin: What we did, is we used the Okta Active Directory agent and we installed it in their domain. It makes a call out to Okta and uploads users that we're not going to automatically provision, because we don't need everybody, but we're going to take a group of users from our sister company and say, "Okay, these users now have access to this application." And really, in a matter of minutes, we're not worrying about firewall rules. As I said, we're not worrying about Active Directory trust. It could've been a sister company, it could've been a call center, it could be anybody, because you just want to bring them on board without having to worry about infrastructure issues.
Joe Dropkin: And it doesn't matter what they were using. They could've been using Active Directory. Well, they are. They could've been using OpenLDAP or they could've been using anything else. The point is is that we were able to feed them into Okta and then get that information out to our applications. And it doesn't matter if it's Sass applications, on-prem applications, our applications that we've built. It all works because it's all authenticating against Okta.
Joe Dropkin: And the big thing about it is when you bring on, be it consultants or any type of third party, it's like, well, how do we know they're still there? Well, we don't have to. Now we can see last log on. Now we can rely on a trusted admin to say, "Okay, look, you're going to be responsible for these users, and they're not going to be integrated in our Active Directory, and we're not going to have to worry about any audits of why are these people from a different company in your Active Directory?"
Joe Dropkin: Having to explain all that is really extra work when it comes to your PCI audits. And it allows you to quickly enable apps for multiple groups of people with very little effort.
Joe Dropkin: So, single sign on. That's an easy one. That's Okta basic. You do single sign on for your Sass apps, but up to date information, we have information from HR and from IT without them stepping on each other and knowing that, look, this department is responsible for this set of information, this department is responsible for that set of information, and that way you get a true mastered set of information in Okta.
Joe Dropkin: Lifecycle management. You are getting your licenses in an accurate count. There's no reason to be wasting money on it. Proper lifecycle management may end up just paying for your Okta installation, and multi-company integration ... You don't have to be part of a large company. We just did something with our call centers where we set up Okta to be integrated with that. Okay? This is a third party, not even part of the Booking Holdings companies, but we needed to set up authentication with a third party, and we said, "Okay, we're going to pay for the licenses. It's just part of what we're doing." But we need to be integrated, and we're going to allow for this integration. We're not going to ... Again, no trusts, no firewall rules, really plain and simple.
Joe Dropkin: And with that, I offer you any questions and answers. Thank you. There's a mic going around, which I can't see because I cannot tell you how bright these lights are.
Speaker 3: Thanks for sharing your journey with Okta. Is there anything ... You talked about a lot of services that you're able to use and leverage. Is there anything that you'd want to see done differently or any challenges that you face?
Joe Dropkin: I will look in your generation direction if I know where you are. There you are.
Joe Dropkin: Would I like to see anything different? Well, I'll tell you. One of the great things about Okta is that ... And not to sound like a cheerleader. I'm stating it as I see it. ... Is that Okta is constantly releasing new features. When Okta released OpenLDAP, that changed all sorts of things for us, because we were migrating our Macs from a JAMP environment on-prem to JAMP in the cloud, and by using the OpenLDAP connector that Okta had built in, we're now able to authenticate the users completely off-prem, which is been great. Not only does it allow for basically remote builds and on-the-fly ... You can basically go out to your Apple Store and say, "Yeah, I'm with Priceline or Booking Holdings. Yeah, I'm with my company." You're in DDP. You hook it up. JAMP sees it, and you authenticate totally in the cloud. You don't have to worry about anything on-prem, and you're good to go.
Joe Dropkin: So the point is, Okta is constantly releasing features that enhance our environment. I've certainly made requests of Okta. I've said, look, I'd like to see this. I'd like to see that. I ask for the world. Sometimes I get half of it, and I'm okay with that.
Joe Dropkin: Does that answer your question? Good.
Joe Dropkin: Is there any ... Besides my own colleagues, is there anybody here that is trying to do a mergers and acquisitions between two companies, and trying, saying ... How are we going to get everybody together? Really, there's no ... Well, maybe you can't talk about it. But I can tell you ... Oh, okay.
Joe Dropkin: The idea that you can just say, "Look, we're going to take one Active Directory from a company that we've never spoken with, and we're just going to import everybody into Okta, and now everybody has access to the same Sass applications." I mean, an hour and you're done. Think of that versus, okay, now we want to set up Dark Fire Burn. Now we want to do trusts between the Active Directory servers. Now we've got to deal with IP conflicts on the routing.
Joe Dropkin: It's just ... You look at it and you say, why would I do it that way when I can do it in a far easier way?
Joe Dropkin: In back there's somebody.
Speaker 4: When you're dealing with apps that don't already support one of the industry standard setups like SAML, what is your technology of choice for setting up the authentication?
Joe Dropkin: So when you're saying that it doesn't have a direct integration and ... I try to guide my app owners into applications that support SAML, but that's not always available. So what I'll do is, I'll still put the app in Okta, usually as a bookmark, but what that allows for is the integration with ...
Joe Dropkin: We're using a product like the Okta Access Gateway that allows us to put those apps behind Okta for not so much authentication but for MFA, because look, if the app is just going to take a simple password, there's really not much I can do about it. There are options to allow the user to save a password in it, but really, not trying to put a bandaid on it, it's really more about working with the app owner to say, "Okay, it's very nice that you have this application. Now, can we get it to a point where this is something that we can do securely?"
Joe Dropkin: Because at the end of the day, I own the infrastructure, not the applications, and I can't force a department to say, "You need to upgrade this application or else." That's a security department, that's not me. It's really a matter of, if an application is going to be weak, I can put as many fences around it, but at the end of the day I can't control the app.
Speaker 4: Thanks. Just a follow-up. I'm dealing with a situation right now where I have an application owner who says, "I want to make this application work on Okta but it doesn't support SAML." And there's just so many different approaches, and I'm just thinking, what's the most cost-effective, time-effective way for them to get on board?
Joe Dropkin: Home-grown application?
Speaker 4: Yeah.
Joe Dropkin: developer.okta.com.
Speaker 4: Okay. But there's so many choices.
Joe Dropkin: So many choices for what?
Speaker 4: At developer.okta.com.
Joe Dropkin: So, if you go there and somebody from Okta can correct me if I don't have this 100% ... You can basically say, "I want to do SAML integration, and this is the language that I'm writing in," and you'll get a snippet of code that says this is what you need to put in your authentication section to point to Okta for authentication. It's a matter of just replacing the current location authentication, for example, with Okta-based code for authentication.
Speaker 4: So, your choice is actually to go with the SAML libraries from that site. Thank you.
Joe Dropkin: Yeah, SAML or, really ... SAML is even becoming yesterday's technology. Do an Open ID connect.
Speaker 4: Have you done that?
Joe Dropkin: Yes.
Speaker 4: Thank you.
Joe Dropkin: Yep.
Speaker 4: Okay.
Speaker 5: So, down here in front. On behalf of Tableau Software, I thank you for using our product. I want to get a little more information about your design decision to go with an AD Agent in the other company as opposed to doing potentially a separate tenant in Okta and doing a B2B connection. I have something similar in the brew, and I'm trying to understand ... I understand that it's all part of the same holdings company, but if you ...
Speaker 5: What was your design thoughts when setting up that agent and just allowing it to go out in somebody else's network, I guess?
Joe Dropkin: As far as our integration with Agoda, the first thing is, we do trust them to some point. We are the same company. But it was also just a matter of ease that we needed to import about 100 people, and we knew that by giving them the agent that we could import their users. We didn't have to worry about identity because everybody's ID is their email address. We're Priceline.com, they're Agoda.com, so we're not going to run into any conflicts there. And we also had Tableau already set up for SAML authentication, so it was really just a matter of adding them in, and when it came up, it was ... I got a IT support ticket for a ... Hey, we need to integrate these people. How are we going to do it? We need to have meetings.
Joe Dropkin: And I scheduled the meeting, and then I showed up at the meeting and said, "It's done." It's really that simple. It really wasn't a security concern because I relied on our Tableau administrators to say, "Okay, we're going to bring in these users," and you have to determine what security level they have. I'm going to give you the users, but don't ask me about what they should have access to. That's an application question.
Speaker 5: Thank you.
Joe Dropkin: Sure.
Speaker 6: Right next door. So, regarding your comment about SAML. If you come across an application that doesn't support SAML, but does support Open ID Connect, would that give you pause, or would you have a preference of trying to keep everything on the same standard?
Joe Dropkin: No, I would say ... Well, I would be surprised that it doesn't support SAML, but I wouldn't give it a second thought. It just tells me that they're being more progressive in the way that they're doing authentication, because Open ID Connect is, as far as my view on it, is just the next standard in seamless authentication.
Speaker 6: Thank you.
Joe Dropkin: Have you run into an application that doesn't support SAML but does support Open ID Connect that's not something homegrown?
Speaker 6: Yeah.
Joe Dropkin: Okay. Did you write it?
Speaker 6: Yeah. Well, I didn't write it, but the previous question about how do you integrate with an existing app, sort of Engine X in front of that, there is an Open ID Connect, but not an off the shelf SAML.
Joe Dropkin: Nothing wrong with Open ID Connect. It works and it's even easier to set up than SAML, because all you're doing ... Basically, Open ID Connect is ... It's like sharing API keys versus having to worry about XML data.
Speaker 6: Damn right, and it's not 10 years old.
Joe Dropkin: That's what everybody's doing, dev ops and APIs.
Speaker 6: Hell, yeah.
Joe Dropkin: Keep them coming. We'll talk or ... Anything else? She's running. I'm going to trust there's a body voice.
Speaker 7: So, earlier you were mentioning that you've kind of got the flow set up, that you've got Workday and Active Directory going into Okta.
Joe Dropkin: Sure.
Speaker 7: Did you ever contemplate using other models, like for example, Workday fitting into Okta, and then into Active Directory, for example. And if so, how did you eventually land on this model that you've chosen?
Joe Dropkin: As far as allowing Workday to create Active Directory accounts?
Speaker 7: Yeah, so on the topic where you were saying, not having the two teams trample over each other.
Joe Dropkin: Show of hands, how many people are using Macs in their environment. And what happens if you change the SAM account name of a Mac user without changing it on the Mac? They lose access to file vault, anything encrypted. Look, nothing against my HR people. They're not IT folks, that's all there is to it. I don't need them accidentally updating, or even purposely updating, somebody's Workday information, but then flows over to Active Directory and locks out my Mac user. That's really one of the keys about it.
Joe Dropkin: Also, we have other tools that create our users, put them in the right groups, base it off of other users. That's just not a function. Look, if I had an integration into Workday ... You can talk about wishes. Okay, here's a wish. I want to take an integration into Workday. I want to model a user after another user. I want that to put them in all the right groups. I want to put them in the right OU, give them all the right security, and have a manager sign off on it. All of that doesn't exist as one thing today, so we have to do it in parts.
Joe Dropkin: But as I said, it's really a matter of, I can't have HR change something that's going to affect my IT operations no more so than I would want somebody at my help desk updating somebody's title, updating somebody's manager, and having that flow back up into Workday. It's just not their realm. We have different departments for a reason. It's checks and balances.
Joe Dropkin: Automation is good. I completely support automation. I tell all of my engineers, I want you engineering, not operating. But there's still ... We can't automate everything, otherwise nobody would have a job, so there's got to be something that somebody's doing just to make sure that the ship stays afloat.
Joe Dropkin: Get a microphone down here.
Speaker 8: Just generally curious, when you say you Oktafied everything when you guys came aboard-
Joe Dropkin: A little exaggeration, yeah.
Speaker 8: Is that including ... Did you guys use the secure web authentication apps as well, or have you ... Do you generally move away from that in favor of SAML and other ...
Joe Dropkin: We tend not to use a secure web-auth, because it's really just filling in a user name and password.
Speaker 8: Yeah. There had to be applications that you guys were using at the time where these more modern ways of authentication didn't exist.
Joe Dropkin: Sure. Absolutely.
Speaker 8: Curious what you did in those cases.
Joe Dropkin: We still ... Somebody asked earlier about older applications that just don't take SAML, and the nice thing about Okta is that it allows us to basically present the users with a single pane of glass. Here are all your apps, and you can sign into all your apps from here, both internally and externally. It gives them that single view that basically brings comfort.
Joe Dropkin: With the apps that don't support SAML, quarterly I go through them and I ask the app developer, or I reach out myself and say, "Why are you not doing SAML?"
Joe Dropkin: And I'll reach out to people like Michelle and say, "Hey, is there any ... Who owns the integration here?" Even some apps that support provisioning and support SAML and push groups and everything that makes the Okta integration network so great, there are other features that we'd like to see in it, and it's a matter of, okay, how can we make this better? Why? This'll make our lives easier. I don't want to have to chase ... I don't want to work with an application that's like, well, it does 95% of the stuff, and yes, this account is deactivated, and it's not counting against your license, but it's still sitting there in a garbage bin. Why?
Joe Dropkin: It's a matter of continuing to work with vendors so you really get an environment that runs seamlessly.
Speaker 9: Hi. I'm over here. This is more of a comment than a question, I guess, but this is related to the same account name, if there's any Workdays and master product developers here, that'd be great.
Speaker 9: When we went to Workday, we actually wrote a web service to update the same, or the account user name, in Workday, and we're not currently using the Workday as a master because you can't update that account name in Workday.
Speaker 9: So if there's anybody that has any idea how to do that with Okta, that would be amazing.
Joe Dropkin: I'm going to say we have time for probably two more questions unless one's lengthy, and then the second person doesn't get to ask. Or I can just give you two minutes of your lives back. Thank you very much.
Priceline serves travelers around the globe 24/7, and keeping everything secure and simple for internal teams empowering a world of travelers requires best-in-class technologies. Since deploying Okta, Priceline has expanded their use cases to “Okta-fy” a variety of enterprise challenges. Learn how Priceline utilizes Okta to add authentication quickly and painlessly to apps (built or bought), to bring IT and HR together (via AD and Workday) in one seamless system to manage employee accounts, to gain visibility into SaaS app usage, to connect independently-managed directories to a common app, and more.