The Enterprise Strikes Back: A Star Wars Story
I spent many of my childhood weekends watching Episodes IV-VI of Star Wars, the world's most famous “space opera.” Recently, it occurred to me that if the Galactic Empire had adopted a Zero Trust security model, it might have prevailed over Skywalker and the Rebels. Specifically, one could argue that the destruction of the Death Star was caused by... poor IT.
Think of the Galactic Empire as the enterprise of its day: a sprawling, multi-faceted organization attempting to modernize infrastructure (how many Death Stars can they build?) and improve M&A agility (albeit a bit forcefully) while dealing with a distributed workforce, legacy technology, and a dynamic threat landscape. While your company may not face armed resistance from a Rebel Alliance, you’re certainly confronting competitors, cybercriminals, and aging infrastructure.
To celebrate Star Wars Day, let’s explore the key lessons that your company can learn from the destruction of the Death Star. We’ll work chronologically from the Rebel’s discovery of the first Death Star’s weakness to its ultimate destruction at the Battle of Yavin.
Disclaimer for Star Wars fans: this analysis is limited to in-canon, major motion pictures and, admittedly, excludes a lot of material for the sake of brevity.
#1: Lifecycle management is a lifesaver
Bodhi Rook was a lowly Imperial cargo pilot who defected with information that turned the tides of galactic history. He informed the Rebels of a fundamental design flaw within the Death Star that could be exploited if the complete plans were obtained from the Imperial Data Vault on Scarif. Piloting his stolen Imperial cargo plane (“Rogue One”) to Scarif with a team of rebels on board, Rook is asked to provide a clearance code to gain entry through the planet’s Shield Gate. Miraculously, the code still works, despite the fact that Rook left his job with the Empire weeks earlier.
At this point, any IT manager worth her salt knows that Bodhi Rook should have been deprovisioned (or at least suspended) from all business systems as soon as he left the organization. If the Empire had used Okta Lifecycle Management for deprovisioning, Rook’s clearance code would have been rejected and the Rebels would likely have been apprehended. It’s no small wonder that Lifecycle Management is one of the biggest value drivers for Okta customers.
#2: People are the perimeter
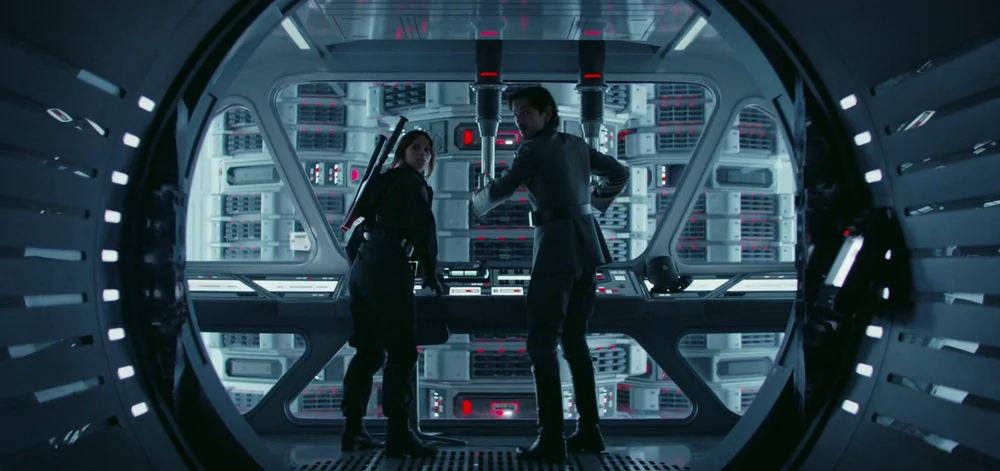
Once the Rebels landed on Scarif, stealing the Death Star plans from the Imperial Data Vault was a simple snatch-and-grab operation. The Empire went through the trouble of surrounding the entire planet with an “impenetrable” defense shield but, once inside, the intruders had access to everything. It’s hard to imagine a more on-the-nose example of how the traditional IT “perimeter” has dissolved.
Jyn Erso and Cassian Andor, not prompted for a second factor while stealing the Death Star plans from the Imperial Data Vault (Photo credit: Wookiepedia)
Today (and a long time ago in a galaxy far, far away), people are the perimeter. To be fair, Imperial forces were alerted to the “unauthorized access of the Data Vault” after Jyn Erso and Cassian Andor steal the Death Star plans. However, an ounce of prevention is worth a pound of cure. Thankfully, Okta customers can protect applications from intruders while reducing friction for authorized employees through adaptive multi-factor authentication. Also, shouldn’t anything with “Data Vault” in its name require some kind of privileged access management?
#3: Identity includes infrastructure
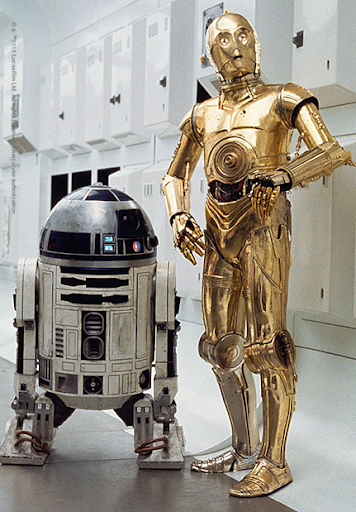
Erso and Andor transmit the stolen Death Star plans to Princess Leia Organa, who stashes them inside R2-D2. When their ship is boarded by Darth Vader in the opening scene of Episode IV, R2-D2 and C-3PO flee in an escape pod which was almost shot down by the Empire, but it was determined that “no lifeforms were aboard.”
The Empire failed to identify the droids as “lifeforms,” but modern enterprises understand that identity extends beyond people to include devices and infrastructure (i.e., droids) as well.
Okta helps companies strengthen the connections between identity and devices in a variety of ways. For example, we recently announced new strategic partnerships with leading endpoint protection and management providers VMware Carbon Black, CrowdStrike, and Tanium to bring device risk signals into the Okta Identity Cloud. In addition, with Advanced Server Access, Okta customers can extend identity and access management to server infrastructure (our protocol droids speak SSH and RDP).
R2-D2 and C-3PO, critical infrastructure, ignored by the Empire (Photo credit: Smithsonian)
#4: Make scale an asset, not a liability
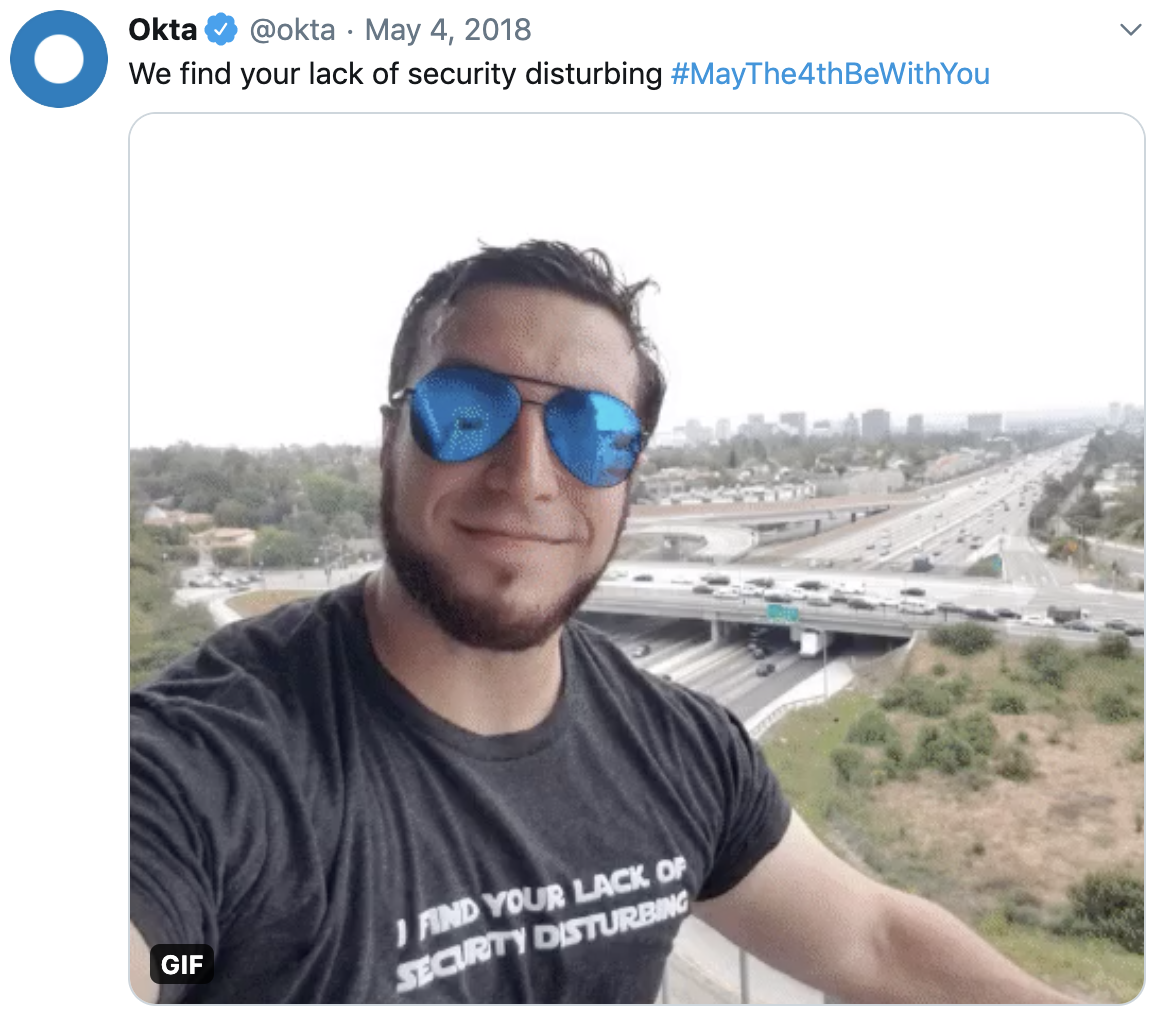
Once they learn that the plans are in the hands of the Rebels, a debate breaks out among Imperial leadership aboard the Death Star. General Motti asserts that “any attack made by the Rebels against this station would be a useless gesture, no matter what technical data they’ve obtained.” After Darth Vader cautions him against hubris, Motti dismisses Vader and his “sorcerer’s ways.” Vader finds this lack of faith disturbing and Force-chokes General Motti. We certainly don’t condone violence at Okta, but we do find some people’s lack of security disturbing:
While size can lead large organizations to derive a false sense of security, it can be a real competitive advantage. We may not have clairvoyance, but SecurityInsights enables organizations to take meaningful action at the admin, user, and customer network levels. By aggregating data from thousands of organizations and millions of users, SecurityInsights leverages the size of Okta’s network for the benefit of every Okta customer. For example, Okta admins can access a dashboard that continuously monitors their organization’s security policies and settings within Okta, offering personalized recommendations for how they might adjust configurations to enhance their security posture. General Motti thought the Death Star was too big to fail and he got Force-choked. Don’t be like General Motti; enable SecurityInsights and make size a real advantage.
#5: Secure mobile devices
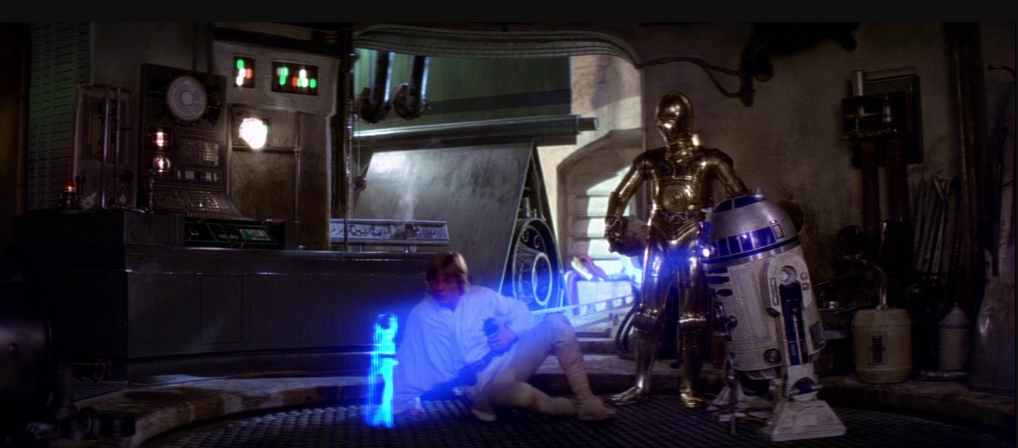
Shortly after their escape pod lands on Tatooine, R2-D2 and C-3PO are taken captive by the Jawas who fit R2-D2 with a restraining bolt before selling the droids to Luke Skywalker’s family. Specializing in capturing, repairing and reselling droids, the Jawas are essentially acquiring and selling managed devices. Later, while Luke is cleaning R2-D2, the crafty droid plays a fragment of Princess Leia’s famous distress message (“Help me Obi-Wan Kenobi, you’re my only hope”). A smitten Luke (gross), is eager to see the rest of the message. C-3PO, translating R2-D2, tells Luke that “the restraining bolt has short-circuited his memory system. He suggests that if you remove the bolt he might be able to play back the entire recording.” Luke easily pries off the restraining bolt, enabling R2-D2 to slip away and continue on his mission to find Obi-Wan Kenobi.
Luke watching unauthorized videos on his mobile device as a result of poor Empire MDM (Photo credit: Destination Hollywood).
Now, if the Empire had halfway-decent MDM, R2-D2 might never have led Skywalker to Kenobi. With Okta’s device trust solutions, you can automate device management for the entire user lifecycle, eliminating manual effort and making your mobile environment more secure. You might say that Okta Mobility Management is a more elegant weapon for a more civilized age.
#6: Phishing is still a major threat
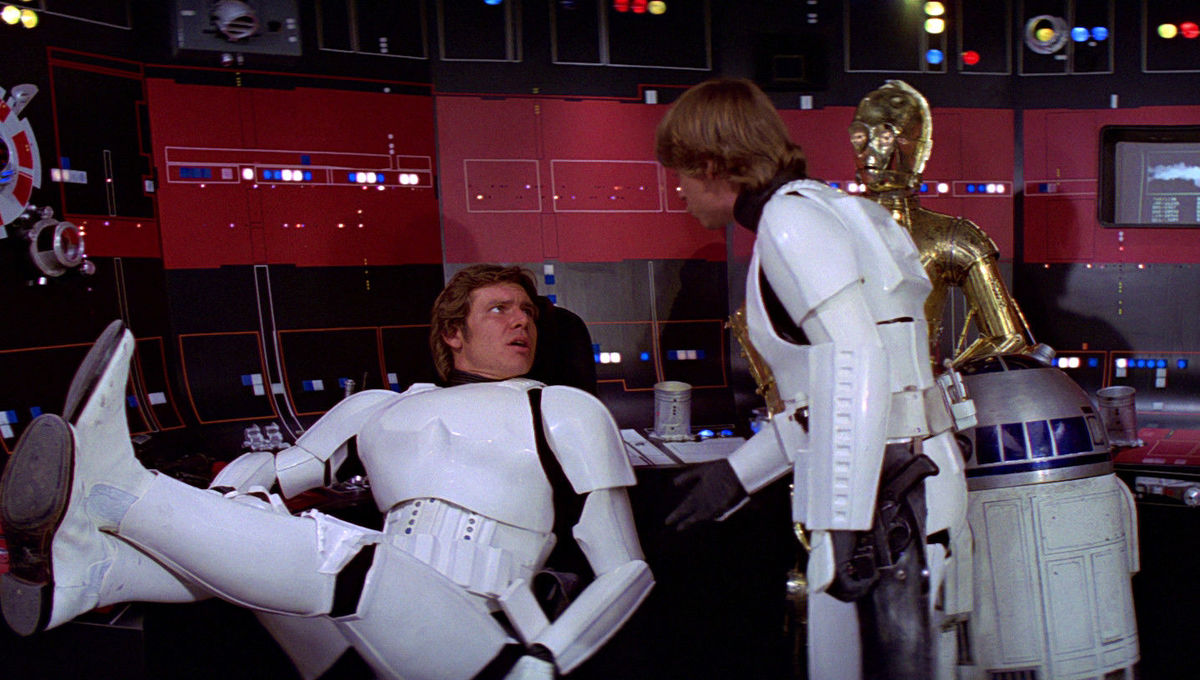
At one point during Episode IV, the Empire captures Luke Skywalker, Han Solo, Chewbacca, Obi-Wan Kenobi, R2-D2, C-3PO, and Princess Leia. With all of the protagonists in custody aboard the Death Star, it appeared that the Empire had won. However, Han and Luke were able to pose as Imperial stormtroopers and gain access to a control room. Classic phishing.
Han Solo and Luke Skywalker phish their way into a control room aboard the Death Star (Photo credit: Syfy.com).
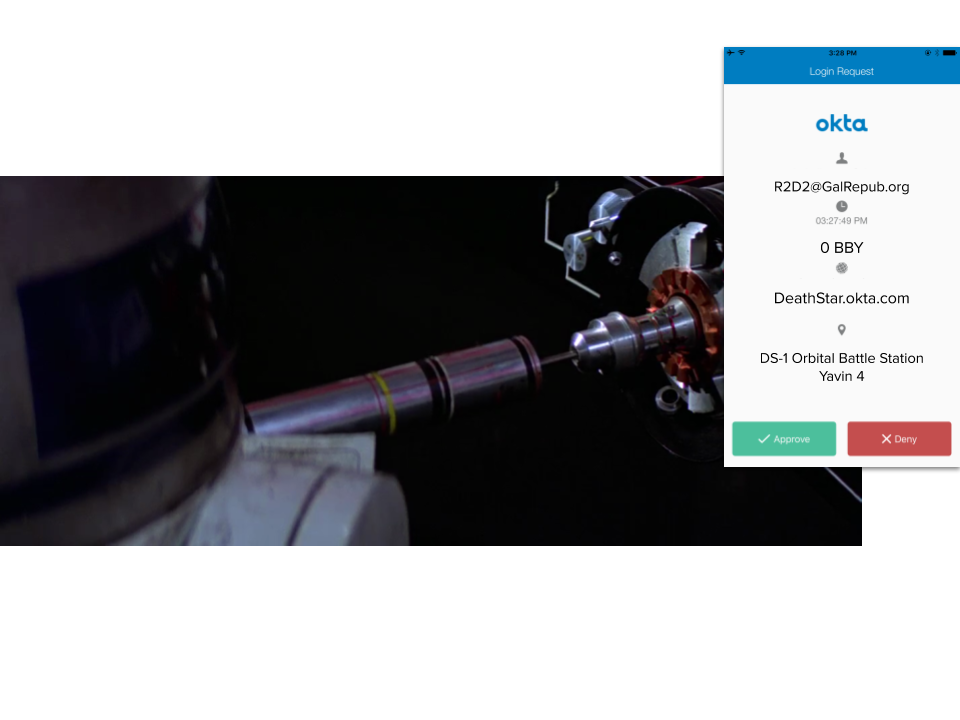
Once inside, Obi-Wan instructs R2-D2 to “plug in. You should be able to interpret the entire Imperial network.” Another brief but poignant moment where MFA would have thwarted the Rebels. From there, it was only a matter of time before the rebels discovered Princess Leia’s location and launched their successful rescue mission.
R2-D2 never received an MFA prompt while bringing down the Empire with an early-model thumb drive (Photo credit: Vice)
In truth, R2-D2 wasn’t even looking for Princess Leia when he accessed the Imperial network (they were trying to disable the Death Star’s tractor beam in order to escape aboard the seized Millenium Falcon). However, while snooping undetected on the network, R2-D2 stumbled across the information about Princess Leia, which turned out to be quite consequential.
Skywalker and the Rebels ultimately destroyed the Death Star and, whether or not you believe that Okta could have prevented it, we hope you see how your organization can benefit from a Zero Trust approach to security. Since Okta is consistently recognized by Forrester as a leader in the Zero Trust eXtended Ecosystem, it might just be your destiny to join us.
May the Force be with you.