The Path to Continuous Authentication: Solving the Best of Breed Problem
For years the network perimeter has been the foundation for controlling access to digital resources: kill the network, and the user no longer has access. Today’s cloud-first world has changed that, shifting the security perimeter to users and devices—and as companies continue to adopt best of breed solutions that enable their workforce, they need identity providers that can effectively protect their systems.
Access management in the modern enterprise
Today, enterprise access control is built around an identity provider (IdP), which connects to applications through federation technologies like SAML and OpenID Connect. At the same time, protocols like SCIM allow for provisioning and revoking access to applications, while users and devices are managed through a central control panel. Meanwhile, HR systems hold and share employee lifecycle management information for a consistent view of access.
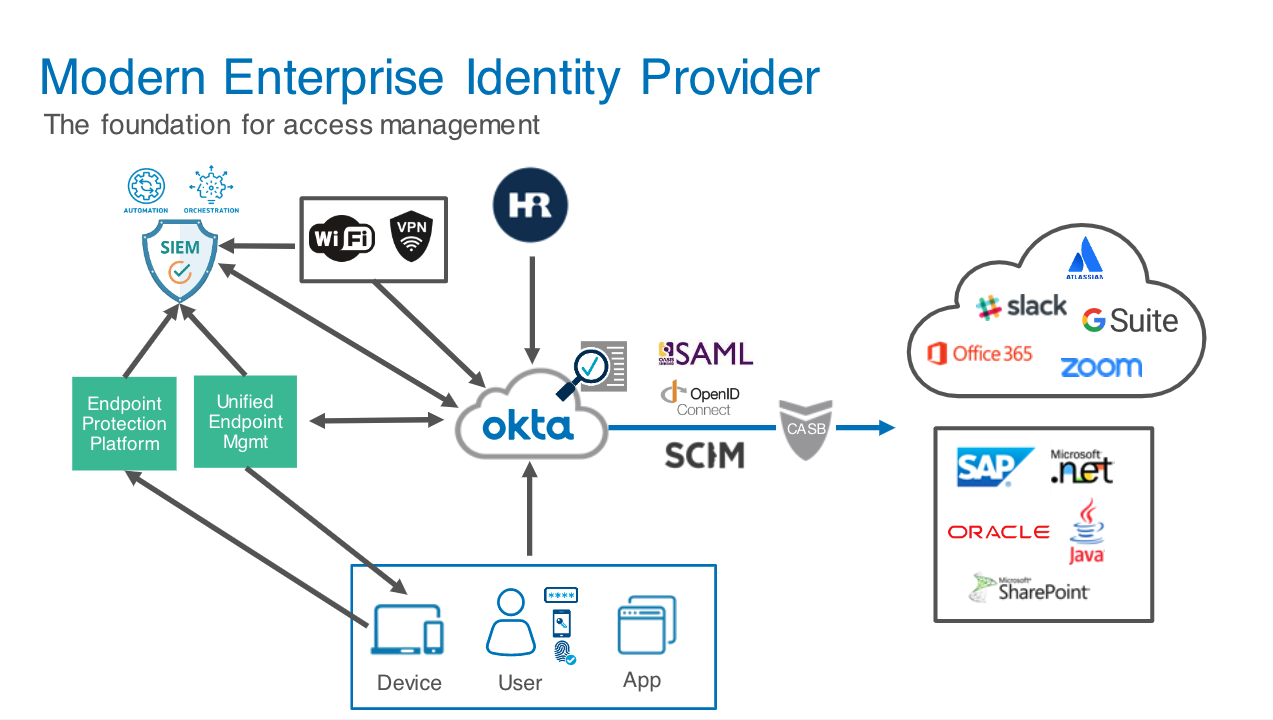
More and more, the enterprise IdP helps authenticate network access, through WiFi and VPN, and works with endpoint management systems to ensure only trusted devices gain access. This robust identity management framework may also be supported by security information and event management (SIEM) systems, as well as session-level access technologies like single sign-on (SSO).
Within this structure, the authentication model is moving away from the “connect first, authorize second” mindset to “authorize first, connect second.” Here, authentication decisions are made based on device assurance, identity assurance, authenticator assurance, and federation assurance. Most IdPs aren’t equipped to review this context, and that forces them to ask users to reauthenticate in any instance where they can’t do it behind the scenes.
So what can businesses do? They need identity management solutions that can continuously assess access, without compromising user experience.
Continuous authentication comes to the fore
Continuous authentication uses data rich tools like geo-location, device Bluetooth, or face ID to passively review your access to resources. Using a long-term “secret” or identity information, it helps provide consistent access, without compromising user experiences.
This approach has been powered by a big investment in standards like the FIDO Alliance and WebAuthN, which has opened up an ecosystem of authenticators that use best of breed technologies to validate the user. It also relies on a standard and consistent approach for assessing device security postures.
Because continuous authentication uses long-term secrets to review access, there needs to be an approach for managing changes to these long-term sessions. This isn’t a new problem—it’s been a challenge for identity architectures for years—but it’s been further complicated by changing use cases and client types, such as native applications built on mobile software, cloud-based apps, IoT devices, and APIs.
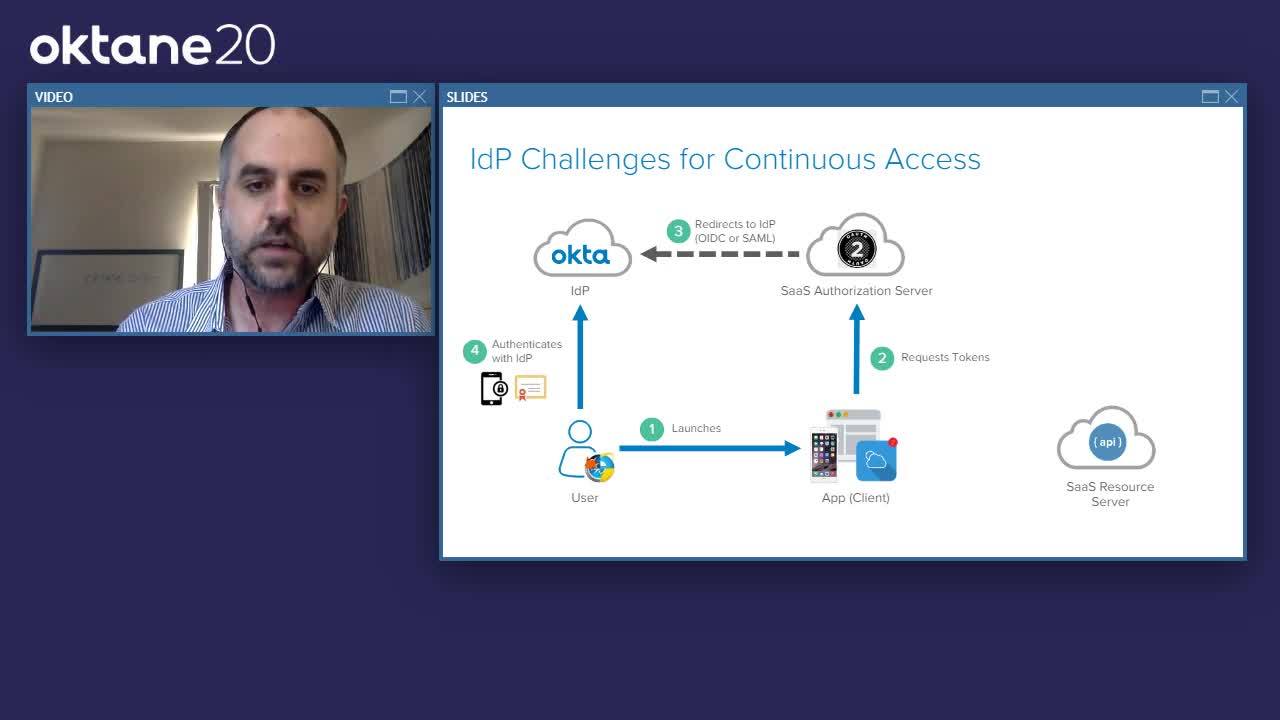
In this landscape, modern applications are native applications. Think of Slack: when we download the app we only ever authenticate our identities the first time we use it. Then, it sits on our machine and runs in the background continuously accessing corporate data and tools such as Google Drive, Mailchimp, Twitter, and Dropbox.
Such applications are often built on OAuth 2.0, which allows them to request new refresh tokens in the background and accesses APIs without prompting the user to log in. This creates continuous authentication challenges as the IdP is not making OAuth authentication decisions and only operates from a web context, which limits the businesses from establishing app and device context.
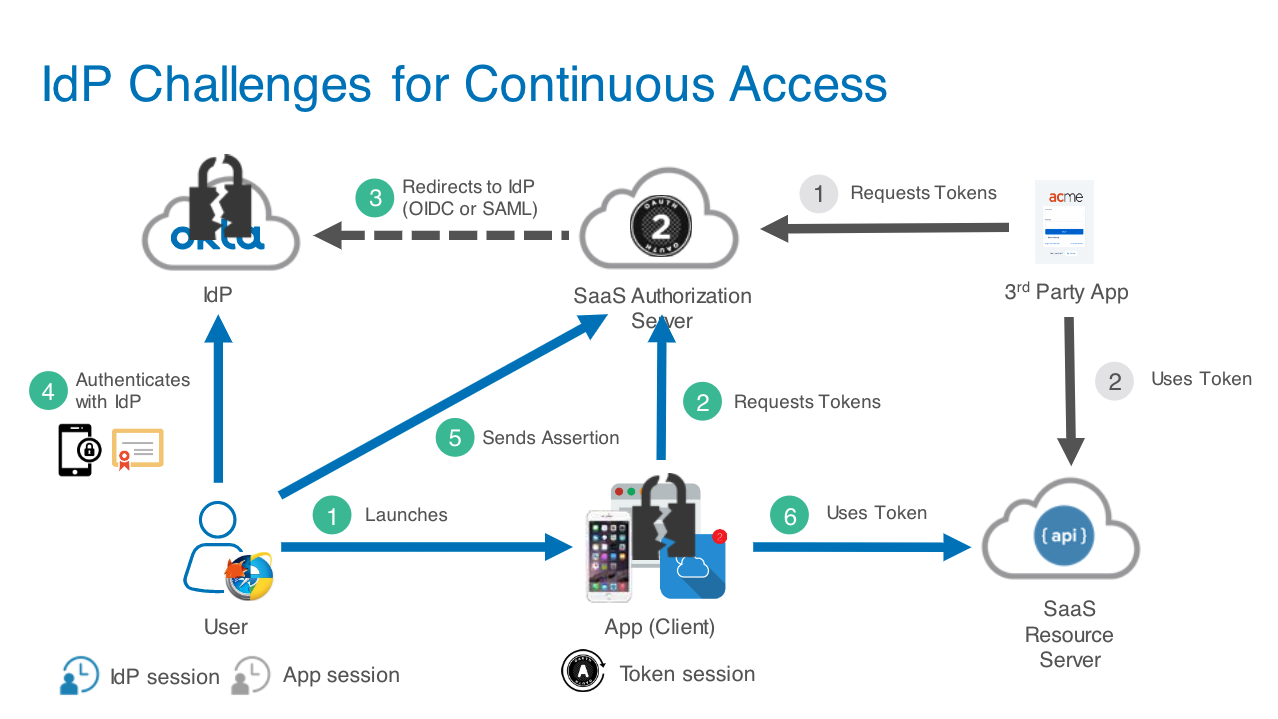
Additional challenges IdPs face include the following:
- IdP policies are only evaluated at SSO, and there is no standard API to revoke or re-evaluate access
- In a long-term session, risk can change after authentication is granted
- SaaS solutions are becoming interconnected platforms, and the IdP might not have access to the connected apps and services
It’s time we move beyond this traditional model.
A best of breed, continuous future
In order to solve the continuous authentication puzzle, enterprise IdPs need to evolve to handle real-time authentication and authorization, enabling the use of the best-of-breed technologies customers demand. To do that, they need to overcome four key challenges:
1. Device identity and security posture
Browsers increasingly try to protect end-users from a privacy and ad-tracking perspective, which makes it harder to identify what device a user is accessing them from. Meanwhile, native applications begin their flow talking to the back-end, which makes it difficult to provide the IdP the attributes needed to make context-based decisions. In order to increase their maturity, the ecosystem needs a standard to establish this context and integrate with the IdP flow, enabling communication with the application back-end in order to provide that device assurance.
2. Session/token attenuation and revocation
Currently, organizations may need to manage thousands of OAuth servers to manage application access, which isn’t practical manually. Instead, they should enable a standard API surface area to manage authorization server management, session revocation and changes, and device access.
Another way to support secure long-term sessions without compromising user experience is to develop a session handle that’s bound to a refresh token and device, allowing the authorization server to check back with the IdP to ensure the user is still who they say they are.
3. Session level controls
Session controls often get mapped to responses within a given application. To help scale this approach, there needs to be a link between the risk that changed and the appropriate security control to be enforced in the app. This can be addressed by enumerating session controls to provide context to the IdP, enabling it to switch between full trust and minimum trust policies during a certain session. Applying this as a standard approach—instead of per vendor—can help mitigate any scaling issues.
4. Shared signals and events
IdPs often know security risks, such as credential theft or unauthorized machine access, before a Service Provider, and vice-versa. Sharing visibility of key events such as changes to account lifecycle or user attributes would help make the enterprise IdP a signal hub that can share these signals across the organization, proactively protecting it from any threats.
Plugging these various approaches into an IdP can ensure an automatic real-time identity intelligence system that delivers and improves continuous authentication.
For more information on continuous authentication and how Okta is addressing this challenge, check out the full Oktane session, and these additional resources below: