To Secure DevOps, We Need to Shift Identity Left
You know it, we know it: DevOps is a core function for any company that wants to deliver exceptional digital products to its customers. But as customers become used to rapid updates and new features from the applications they use every day, there’s an added pressure for your DevOps team to be continually innovating so that your business can do the same.
Unfortunately, within this landscape of rapid production, security has often been an afterthought. At a business level, this causes noticeable silos between DevOps and security teams, and negatively impacts your security posture. At an application level, this means that you risk introducing identity vulnerabilities that could leave the door open to attacks on your systems. And at the operations level, this could mean missing guardrails across your critical infrastructure resources.
In our previous post on this topic, we talked about the need for security in DevOps and how it’s shaping the role of identity in the software development lifecycle. This is an increasingly important practice, as failing to implement guardrails before automation takes over can cause security roadblocks as you try to scale your application. In this post, we’ll discuss the benefits of embedding identity and access management (IAM) and offer suggestions for how to enhance your identity maturity within DevOps.
Identity’s role in DevOps
As DevOps functions increasingly add security to the mix (see DevSecOps), IAM is a crucial component. Identity represents access and privileges, ensuring automated activities are properly authenticated, authorized, and audited. The more you automate, and the more you scale, the more important it is to get identity right.
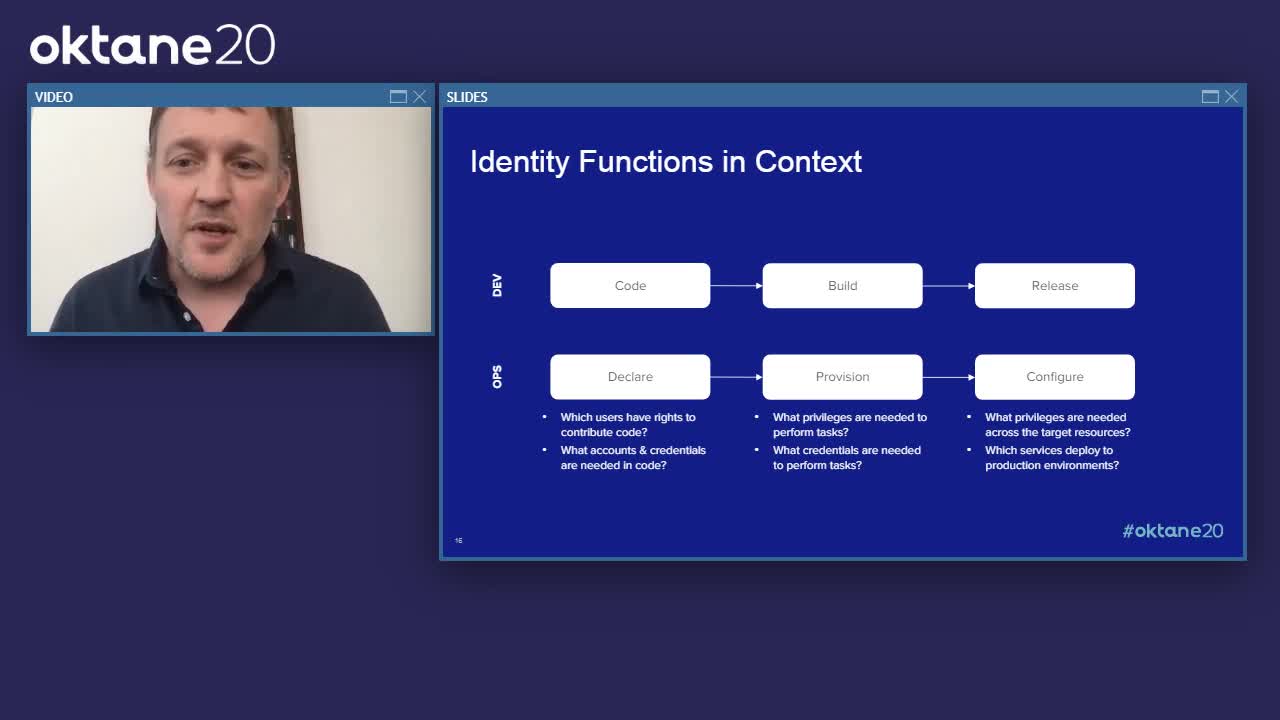
Across every phase of the software development lifecycle, it’s important to focus on identity in the context of each Dev function (plan, code, build, test) and each Ops function (release, deploy, operate, monitor). At each stage, IAM helps answer questions such as which users have the rights to contribute code, what accounts and credentials are needed in the code, what privileges are required across target resources, and more. In doing so, it helps mitigate any security threats and vulnerabilities that could compromise the organization, its users, and its provisioned infrastructure once the software has been deployed.
Despite these benefits, many teams still use a traditionally mix-and-match approach to identity, leaving them open to a variety of challenges:
- Static credentials: Hard to attribute to a user, which means too much time is spent on protecting them from getting into the wrong hands.
- Shared accounts: Difficult to audit and make it challenging to confirm who the user is and their role.
- Local accounts: No tie-backs to systems of record, making it nearly impossible to track whether users have the right permission access level.
This approach makes it difficult for developers to effectively provision and deprovision users. Onboarding new users to dynamic systems and applications is complex, as is decommissioning their access when you don’t have visibility into where their accounts and credentials might live.
So how do we actively solve these issues?
Putting identity into every step
Injecting identity as early as possible into automation pipelines is a key step to minimizing the exposure of sensitive accounts and credentials. This way, your DevOps team can remove static credentials from code, replacing them with just-in-time credentials that help to reduce the threat surface and enterprise-wide risk.
Incorporating a robust IAM solution also enables automatic user provisioning and deprovisioning at each stage of production, removing the need for manual tasks that hinder productivity and increase risk. A centralized management system can also allow for simplified visibility into access permissions and authentication requests, making it easy for your security team to monitor IAM activity around your APIs and applications.
In parallel, taking an “everything as code” approach to DevOps security will ensure that all elements are controlled, documented, reviewed, and retractable. At the end of the day, your security controls will only ever be as good as you build them.
An elegant solution for DevOps security challenges
Designed to support DevOps teams as they embed identity across their various functions, Okta’s Advanced Server Access (ASA) provides Zero Trust identity and a cloud-first approach to access management. The solution enables just-in-time passwordless authentication to Linux and Windows servers, automates the end-to-end lifecycle of user and group accounts, and enforces role-based access controls and command-level permissions. As an added bonus, ASA removes the need for static credentials and ensures excellent user experiences.
Without implementing a robust IAM approach, your DevOps team is bound to be plagued with manual tasks and security vulnerabilities that get in the way of their goal of deploying secure, usable software at a rapid pace. With a tool like ASA, you can enable your team to automate identity across the board, avoid operational burdens, and deliver seamless and secure user experiences.
To discover how Okta can help your business to shift identity left, check out the following resources: