Bootstrapping Okta FastPass enrollment in a phishing-resistant manner
Deploying phishing-resistant multi-factor authentication helps prevent unauthorized access to your company’s sensitive resources. But what if the process to enroll in that factor is not phishing-resistant? At Okta, we recognize the phishing resistance of a factor traces all the way back to enrollment, and that’s why we have now built into Okta Verify a direct way to bootstrap additional enrollments onto new devices in a phishing-resistant manner.
Pat just got a new phone. Since Pat is used to accessing resources seamlessly and securely on their laptop by using Okta FastPass, a phishing-resistant factor, they want to enroll on their new phone as well. While authenticating during enrollment, Pat enters their password and triggers a push to their old phone that has Okta Verify Push. Pat can successfully enroll, but they used two factors that are not phishing resistant. Pat's IT department didn’t anticipate this. They automatically quarantine Pat's account with the power of Okta Workflows and perform identity verification. This solution is good, but is there a more streamlined process for Pat and IT that also reduces cost?
Why, yes, now there is! The Okta FastPass team is excited to introduce our latest enhancement that’ll allow users like Pat to use their Okta FastPass enrollments on existing devices to bootstrap enrollments on additional devices in a phishing-resistant manner without the headache of another identity verification step. This feature works across all four of our currently-supported platforms (Android, iOS, MacOS, and Windows), so users can seamlessly bootstrap enrollments across any combination of platforms!
How it works
Overview
We utilize Bluetooth Low Energy (BLE) to connect and transmit data between the Okta Verify app with the existing FastPass enrollment (Enrolled Okta Verify) and another Okta Verify app on a different device looking to enroll (New Okta Verify). By using Bluetooth, we ensure that the two devices must be in close proximity, reducing the possibility of a remote attack. After user authentication, Enrolled Okta Verify makes a request to Okta’s servers to get a one-time enrollment token and sends it encrypted over Bluetooth to New Okta Verify, enabling it to complete enrollment securely.
The enrollment bootstrap flow has four key steps:
- The user authenticates on Enrolled Okta Verify to get an enrollment token.
- Enrolled Okta Verify and New Okta Verify pair over Bluetooth.
- Enrolled Okta Verify and New Okta Verify establish a secure communications channel with end-to-end encryption.
- Enrolled Okta Verify sends New Okta Verify the enrollment token over the secure communications channel and New Okta Verify enrolls with this token.
User authentication to get an enrollment token
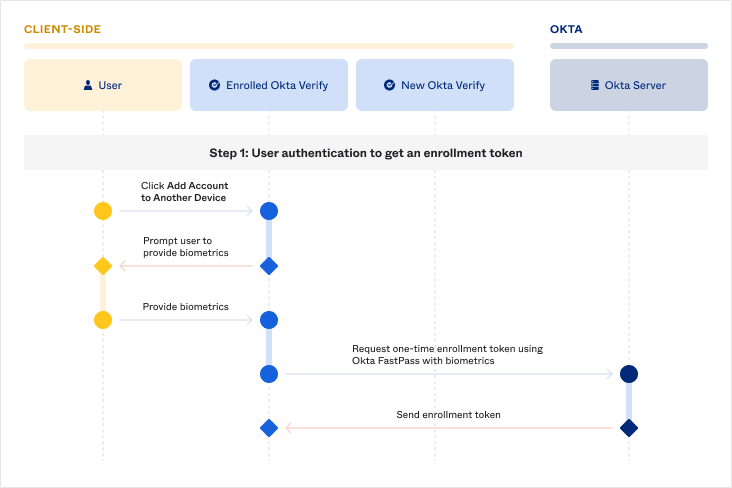
To ensure the rightful account holder is trying to add their account on another device, the user must authenticate with two factors and in a phishing-resistant manner for Enrolled Okta Verify to get an enrollment token. They can do so by using FastPass with biometrics, which serves as both a phishing-resistant possession factor and an inherence factor.
Device pairing
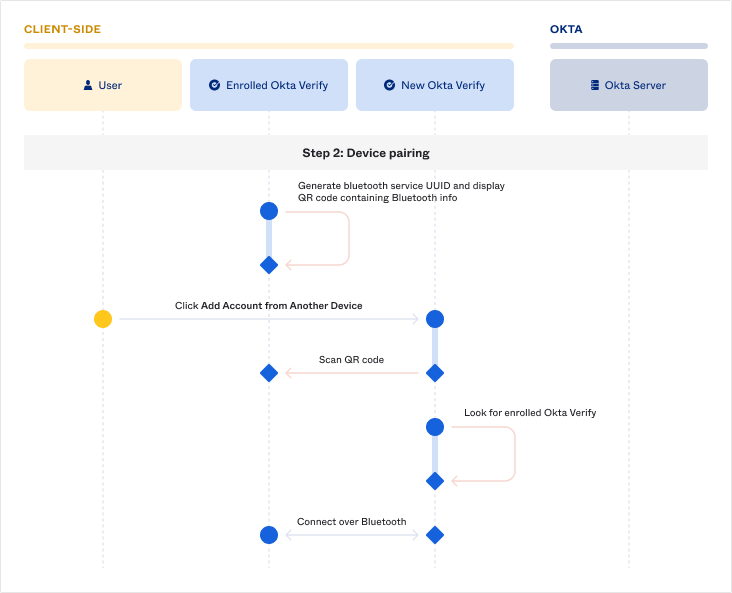
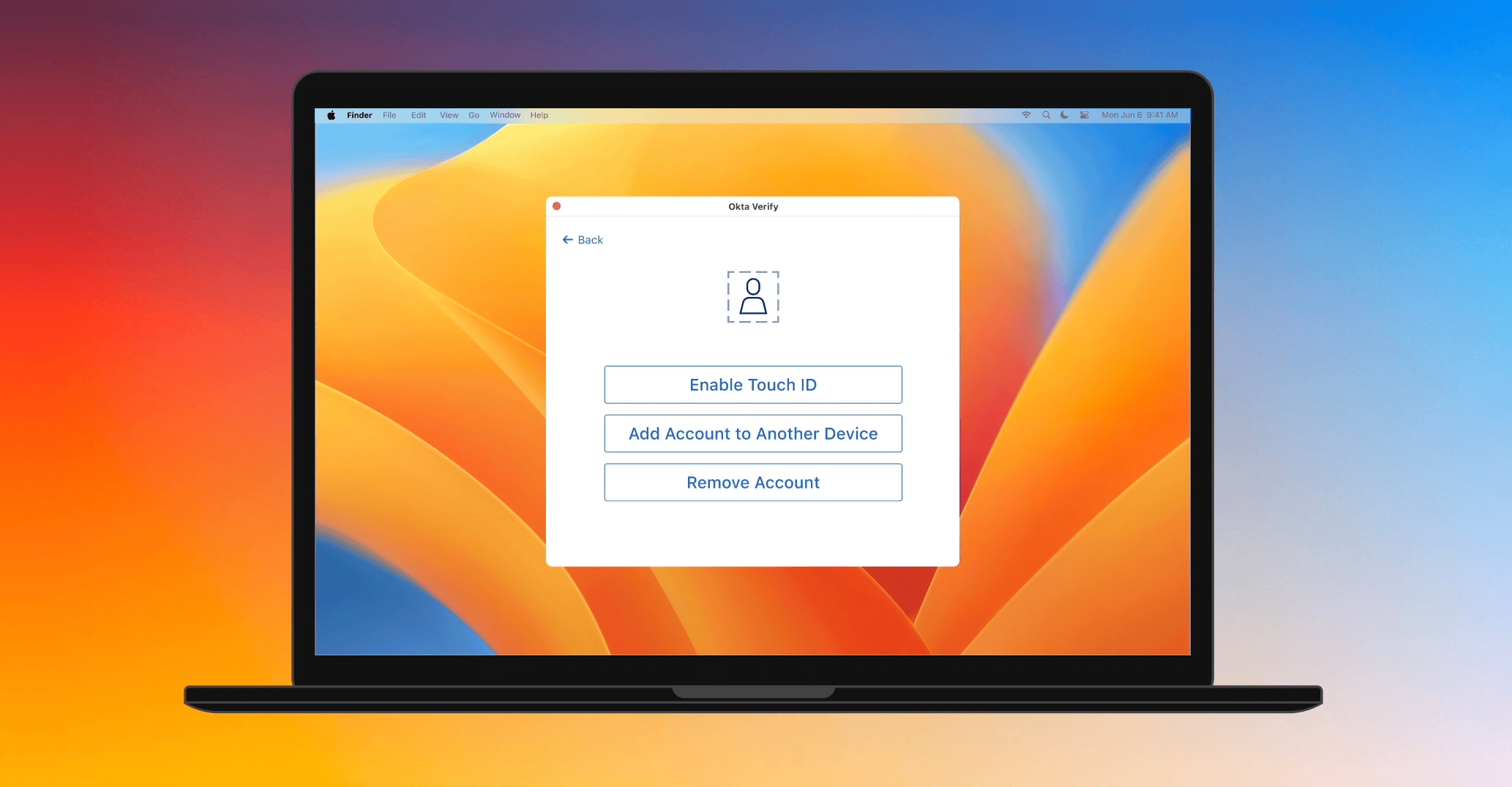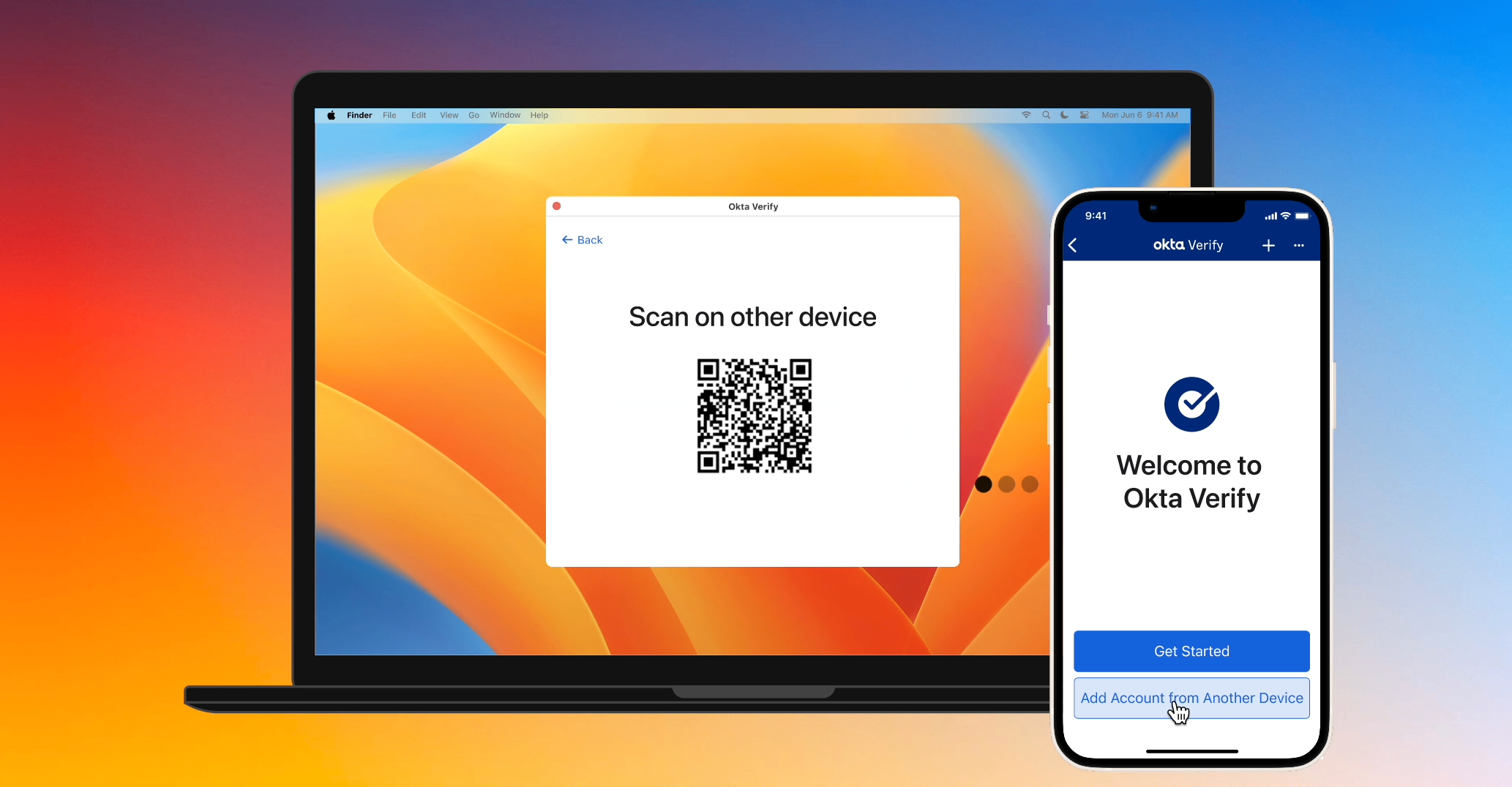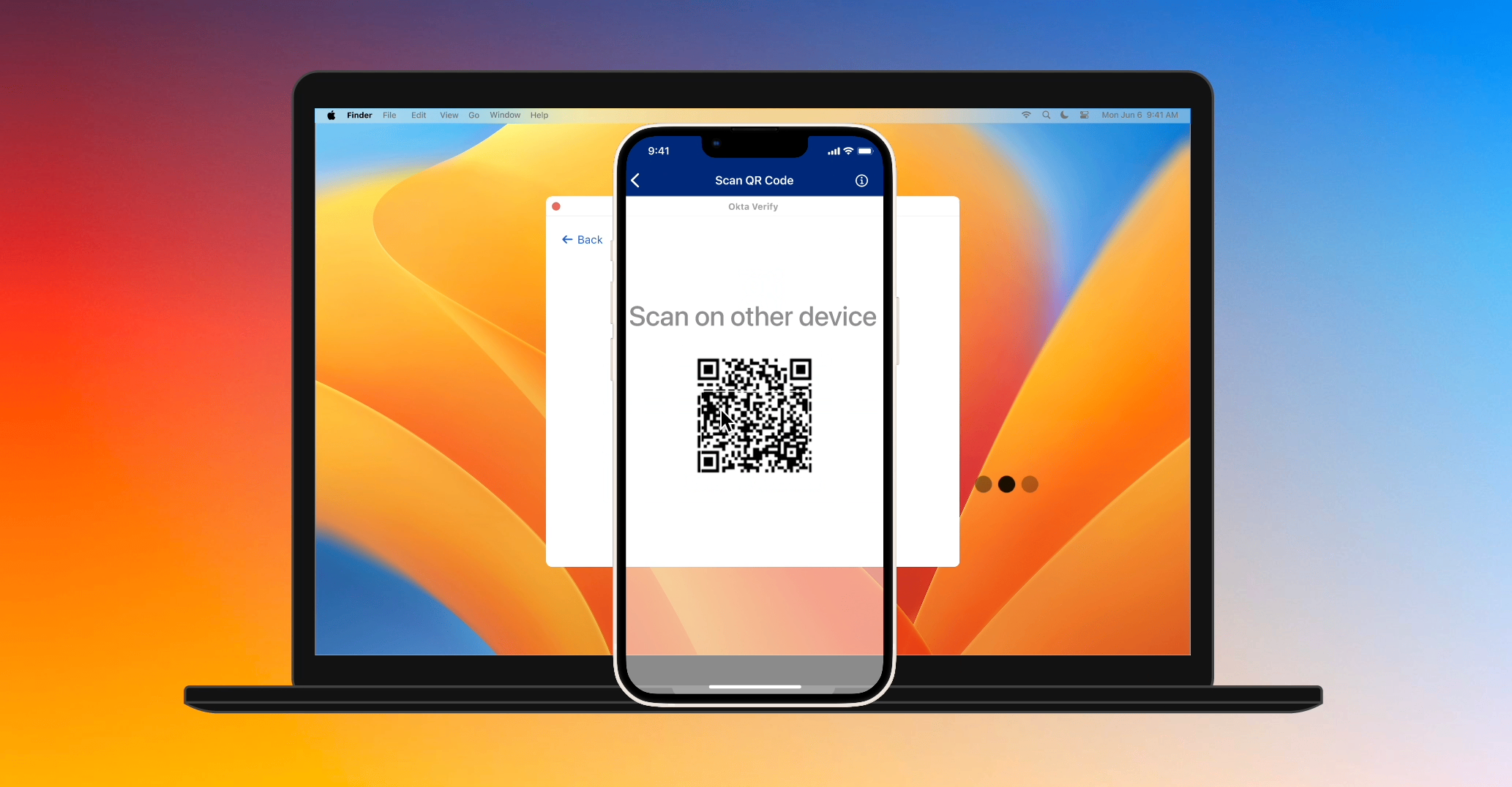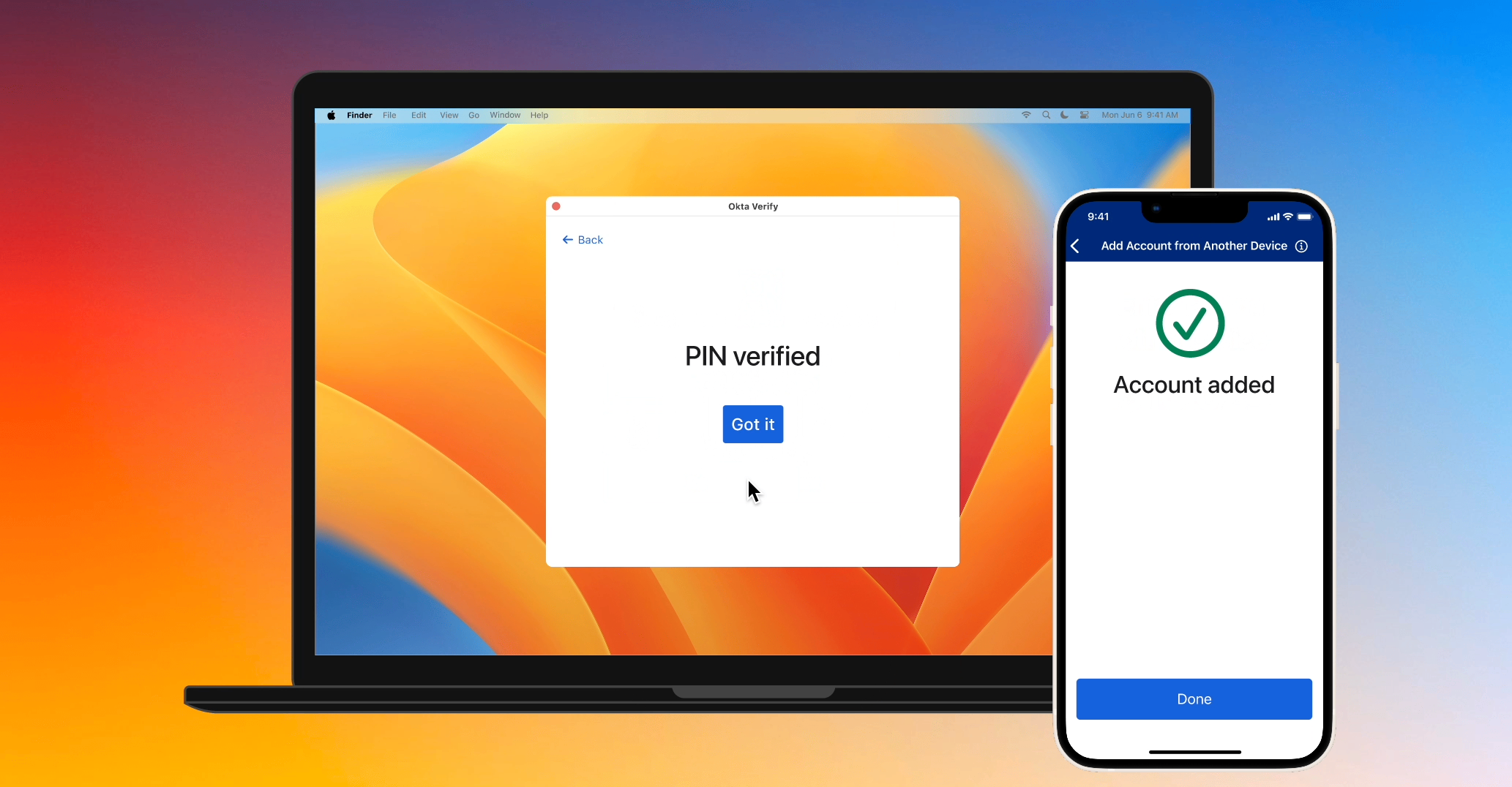
The next step is to ensure the user is connecting their Enrolled Okta Verify with their own New Okta Verify and not someone else's. Every time a user initiates an attempt to add their account on another device:
- Enrolled Okta Verify dynamically generates a Bluetooth service UUID that New Okta Verify will use to look for Enrolled Okta Verify.
- New Okta Verify can scan the QR code displayed on Enrolled Okta Verify to get the necessary information to look for Enrolled Okta Verify. To support devices where scanning the QR code is impossible or difficult, Enrolled Okta Verify also displays a code that the user can manually enter into New Okta Verify.
- Once New Okta Verify finds Enrolled Okta Verify using the dynamically-generated service UUID, the two form a Bluetooth connection to send data to each other.
Establishing a secure communications channel
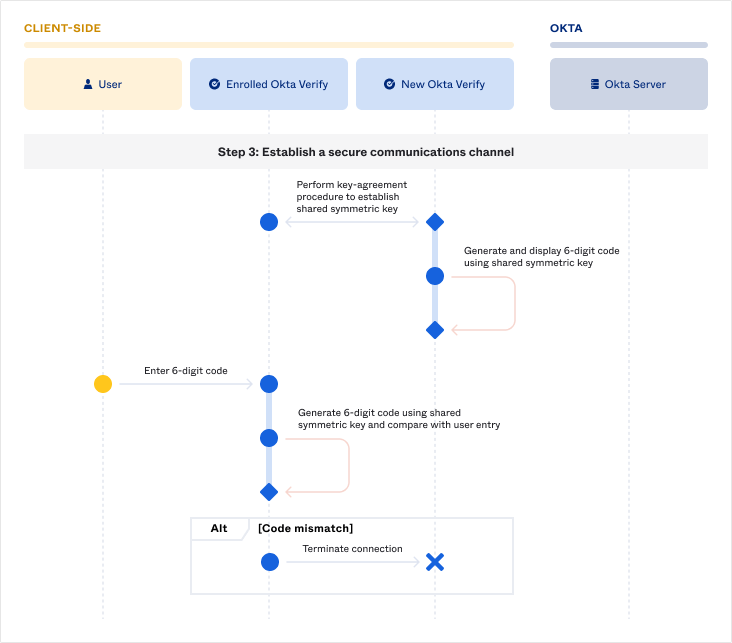
Since Enrolled Okta Verify will send the enrollment token to New Okta Verify over Bluetooth, we need to ensure that this sensitive information can be sent securely. While the BLE protocol supports secure data transport, we’ve added application-layer security just in case. To do so, the two sides go through a key-agreement procedure to establish a shared symmetric key with which to encrypt and decrypt data sent over the Bluetooth connection.
Once both sides have generated the shared symmetric key, we need to do one final check to ensure that the user alone is in full control of both devices. New Okta Verify will display a six-digit code generated using the shared key, and the user will be instructed to enter this code into Enrolled Okta Verify. Enrolled Okta Verify will also generate the six-digit code using the shared key and check if it matches what the user entered before proceeding to the next step. If the user unintentionally paired their Enrolled Okta Verify with someone else’s New Okta Verify, the code will not match and Enrolled Okta Verify can abort the flow.
Enrolled Okta Verify sends the enrollment token to New Okta Verify
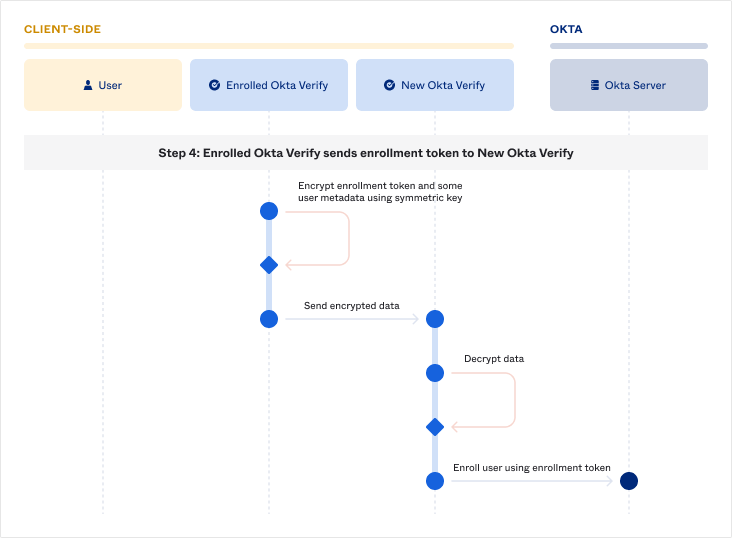
Finally, Enrolled Okta Verify will encrypt the one-time enrollment token and some metadata using the shared symmetric key and send it to New Okta Verify. New Okta Verify will decrypt the data and provide the one-time enrollment token when making the enrollment request to the Okta server.
Enhanced security and better user experience
With this new feature, Okta is making life easier and more secure for both users and IT admins alike. Now Pat can simply go into the Okta Verify app on their laptop to bootstrap an Okta FastPass enrollment on their new phone. Pat’s IT department no longer needs to worry about whether the new enrollment truly belongs to Pat or pay for expensive identity re-verification to be extra sure. We are super excited to offer this innovative solution that enhances the usability and security of Okta FastPass, and we can’t wait for all of you to try this out!
Have questions about this blog post? Reach out to us at [email protected].
Explore more insightful Engineering Blogs from Okta to expand your knowledge.
Ready to join our passionate team of exceptional engineers? Visit our career page.
Unlock the potential of modern and sophisticated identity management for your organization. Contact Sales for more information.

