Oktane18: Future of Identity and Identity Proofing with Experian
Transcript
Details
Tom Smith: As Danny mentioned, I'm Tom Smith; I'm a Partner Solutions Architect with Okta. I'm joined by Chris Danese: Business Consultant with Experian. The way we're going to do this today is Chris is going to walk through the future of identity and identity proofing with Experian, and then I'll follow up with an architecture overview and a demo of a pattern of how this flow can work between Okta and Experian. So, with that, I'm going to turn it over to Chris.
Chris Danese: Thank you. Good afternoon, thank you for coming to our session. Honestly, what an amazing conference Okta has put on; this is my first time. Having the opportunity to not only attend, but certainly I'm very humbled to have the opportunity to speak and present to you today. As introduced, I am with Experian. I would ask you to raise your hands to let me know how many people are familiar with Experian, but I can't see back that far. Oh, there's one! So, excellent.
Experian is primarily, most people would know us as, a credit reporting agency. We collect and aggregate data over 1 billion consumers worldwide. We are a global company. We serve a number of different client bases, from financial institutions, banks, credit unions, e-commerce, retailers, utility companies, government agencies, and a wide range of other host channels. Ultimately, I just want to share with you the types of consumers and clients that we support. In addition to that, we also offer a number of products for direct to consumer. So, Experian, for example, offers credit monitoring services for consumers. Many of you who have a relationship with financial institutions may offer some form of credit monitoring; whether that credit monitoring is for credit risk or credit repair, and/or for fraud prevention/identity theft type monitoring. That's a little bit of a history relative to Experian. We employ over about 15,000 individuals worldwide, and I'm very proud to be in front of you today as a member of our fraud and identity verification business. I'm a business consultant who provides expert advice to our clients, relative to potential fraud risk that may exist within their organization.
How do we go about in helping our clients? Well, we attempt to identify potential risks across their organization and provide for them the relevant data to help them with their identity proofing process, and to help improve the potential for existing risk. My specialty is operational excellence. What that means is I help clients ultimately make better decisions relative to the improvement upon their customer experience. We do that by helping them develop more insightful decisions through the usage of data and fraud strategies. Experian dramatically improves the return on investment. We lower operating costs, we provide a quicker, more seamless consumer experience through our passive authentication, which Tom is going to share with you just one of the ways in which we go about to achieve that.
As we all know, there's a lot of change going on in the digital marketplace. The digital world is here to stay. Yesterday, I think, for me it was rather interesting for me to hear President Obama when he had shared ... He's in a small village in South Africa and he sees children running around with a mobile phone; just something, again, how the digital environment has grown so rapidly and how it's really become a global ... The globalization of the digital world. What's really important to that, I had read an article recently which kind of emphasized the fact of what the President had shared yesterday, that about 80% of all data has become available in the last 3 years. Think about just the amount of data that's being processed and becoming available. What does that mean for our clients, and how do we work with Okta to help solve for that?
There's so much data available that the question of most clients is, we don't know which data is relevant. We need to understand the source of truth, because you have conflicting data sources that may be telling you different responses back relevant to your identity verification. In addition to that, the digital environment has created a consumer demand on most clients that, quite frankly, is difficult to keep up with. Our consumers are expecting clients to provide an immediate response, immediate decision, immediate product, immediate service, all of which as we know, is delivered within milliseconds. That creates quite a burden to make sure you're operating a business safely through fraud and identity proofing, and delivering an accurate response back, really, within seconds. The last element is big data: the velocity, the variety of data is growing, the sources of data continues to grow. You see in the industry where we're looking at data sources different to determine how it can be used effectively, what data is regulated versus non-regulated data, and whether it can be utilized to help solve problems that really didn't exist before.
The last element relative to the somewhat changing is the regulatory requirements. I'm not going to get into a lot of detail relative to regulatory change, regulatory requirements. There's absolutely a shift. There was a very strong emphasis on regulation; some would say over-regulation. You now see us moving toward a deregulated, or less regulated, space. So the interpretation of those regulations is, quite frankly, still up for debate. We do a lot of work with, meaning Experian, we work with lobbyists, we work in Washington, and a lot of our focusing efforts is to help drive some of that change forward. Lastly, data security, which is what most of us are probably here for, is how do you protect all of this assets, and the alternate data assets, effectively? Well, we'll talk about that through some of the different challenges that have come up because of the vast amount of data that's become available.
The first is positive and passive. What is passive authentication? What is the level of disruption or discomfort a consumer is willing to endure in order to complete the service they're looking to render? Compliance and regulatory scrutiny often in the industry that I primarily support, the financial industry, there's a tremendous amount of misunderstanding, inconsistencies in interpretation of the requirements. An example being you know your customer requirements, know your customer is CIP, or Customer Identification Program. What often, our clients may, at times, confuse or bring together is the compliance requirements for knowing your customer and fraud authentication are two separate steps. Often, in our industries, where we see the merge is that they think one satisfies the other. That's not necessarily the case, and that creates regulatory risk at times.
In addition to that omni channel, the number of channels just continues to grow of which we are serving our consumers. I'll use an example in banking: a channel of which we all know, phone, online, digital, face-to-face type of transactions, but an area that's often at risk and where I think identity proofing still has opportunity to improve, is in your chat space. How do you authenticate a consumer in a chat conversation? What's considered authenticated space in chat? So those channels of which we're communicating with potential consumers continues to evolve, and I would anticipate we will be talking about channels 2 years from now that many of us haven't even had exposure to. Lastly is user experience. We want in quick, we want it simple, we want it right the first time. Nobody wants to have to drive a consumer into a call center or to go through additional discomfort through authentication. Now, step-up authentication is certainly part of the process, multi factual authentication. There's is an element where it becomes disruptive and a consumer will abandon. Often, what we do is we help with driving the relationship with the consumer to say how do we help you mitigate the risk before you get to the point where your consumer abandons that process?
Lastly, this channel, compelling expectations. This is probably something we all experience. Marketing has an objective, that's to grow revenue. Credit may have an underwriting objective; your collections, your fraud departments, your sales teams, all may have competing and different objectives, but you're all trying to get to the same place. Those internal competing objectives often through lack of communication, and again I'll use the President as an example, when he said sitting on a round table and the people that really know what's going on or making the real decisions are those sitting in the second row that are taking the notes. Ultimately, that's an area in which a lot of clients struggle. They don't have all the key stakeholders at the table at the right time, and that's where you have inconsistencies in identity proofing for different products and different channels that one organization may offer.
The identity life cycle has changed pretty dramatically over the last ten years. I've been in the identity verification business for about 30 years; I started when I was 7. Through that course, really what's changed, and I think this slide although very simplistic, illustrates where the markets are going, most markets. The first is, and I call the identity proofing, and underneath you'll see 'once'; you really only need to verify your consumer one time. Do all of your identity proofing upfront. As that consumer wants to add products or add services, you've already completed the identity proofing. Really, the second step of identity, whether it's an existing consumer or a new relationship to an existing consumer, that authentication process is done repeatedly, but it's done against what you've already done one time at the time of membership, the time of enrollment, or the time of a new account opening.
Then lastly is the ongoing portfolio for customer based monitoring, an area where oftentimes we see individuals at clients and businesses fall down. I'll use a banking example. In the financial sector, there's many requirements which regulators have a great deal of interest, one being portfolio monitoring. Banks are required to make sure that an individual's not on a OFAC list. An OFAC list basically consists upon potential terrorists, any money laundering, drug money, things of that nature. OFAC is looking for those types of individuals. If I bring Tom on as a customer tomorrow, and Tom passes that check, and he has gone through identity proofing, he's opened additional relationships, and we never look at Tom again for the 20 year relationship, Tom may appear on an OFAC or a high-risk list at some point. If you fail to monitor your existing portfolio for those incremental risks, what you've done upfront, quite frankly, is for naught. We talked a little bit when we were preparing for this session as to whether or not, from an identity proofing landscape ... There was a topic that came up through the National Institution of Standards and Technology. What I highlight here for you on the slide, specifically is the second part, is the step-up relative to the standard of identity, what levels of assurance are considered acceptable, especially through the remote and identity proofing. My next slide's going to show you a little bit about what has changed.
I did tell you I wouldn't spend too much time on compliance and regulatory, so I promise this is my only slide. In the old environments, what you see on the left hand side, is a reasonable level of assurance that you've conducted identity proofing and that the individual is who they say they are. The new requirements, although the font may be small, I'm going to kind of share with you real quickly what you need to know. The first box is ultimately asking you for the source of truth. Two companies in the same industry trying to verify the same individual may or may not be required to use the same source of truth. So the question is: what do you consider the source of truth for when you're verifying the identity of your consumer? The second is multiple data sources, so that if Tom shows up in one data base, that doesn't necessarily mean you need to be completely reliant that that information is accurate. You need to now go to multiple data sources to help you identify and verify the identity of the individual. Lastly is a combination of both, which we're going to talk about a little bit in this slide.
So, old environment: asking for a copy of a driver's license number, asking for a driver's license number, may have been an acceptable form of identity verification. The new standards are saying that is no longer a reasonable level of assurance. The driver's license itself would be a higher level of assurance, because it has your PII information on it excluding Social Security, you'll have the physical address, you'll have a physical document that can be ... We'll talk to you in a little bit about how that can be measured in a standard ... And the photograph itself. So, those additional enhancements to the same driver's license number versus driver's license document, are some of the things you're seeing change. Another example is passport, visa, or any other documents provided by the government. Ultimately two strong identity verification elements to satisfy the new requirements.
What Experian's excited to tell you is we came here with the solution for you. The solution is product that we have called Crosscore. Crosscore, although we think is outstanding, we're not the only ones. So, a few recent awards through Javelin and Juniper, and a few others. I was just made aware of one yesterday, Forester came out and recognized Experian
Chris Danese: I was just made aware of one yesterday. Forrester came out and recognized Experian as the number one used company for identity verification, so we're certainly proud of it, but it's great to see that those accolades are coming from other institutions within the fraud and identity space. Let me tell you a little bit about CrossCore, and then Tom's going to share with you a demo of how CrossCore ultimately works and integrates. It's flexible. It's a JSON API. It has a single integration suite, and what we're going to share with you is how through the use of CrossCore, we can call out to respective data finders, data sources, and/or third-party sources to bring in the information necessary to meet those previous requirements that we talked about to meet the new standards.
It's an open approach. You're not limited or predetermined to any particular source. Did anybody attend the microservices presentation yesterday? There was a great example in there for the individuals that we're talking about, coupons.com, and ultimately how they were able to go to different data sources to bring in information very seamlessly. That's going to be consistent with what you're going to see here today. It has a workflow decisioning process, which allows you, based on the risk that's present, to determine what the next action should be, whether you want to accept that individual through enrollment, whether you want to step them up to additional information, different additional documentation or some form of authentication, or if you simply want to refer them out of the process into a manual review or decline them in the final state. Within CrossCore, a number of things that really are critical and separate us from the rest of the industry, you're personally identifiable but we bring in the collection of the PII, so that information is brought in to help with the decision. The example that you're going to see here is how, through the use of completing a form, PII is brought in through that form, and it runs behind the scenes, through CrossCore, to call out to different sources of truth to give you a risk factor that will tell you what do we do with it from here.
Strong, and fair evidence, so that's the collection of the evidence. What's considered strong? The driver's license versus someone's provided, I provided to you my social security number, not checked against any third party source. The workflow, the orchestration of the decisioning, what does the strategy manager look like? How do we draw the right conclusion for you based off of the information available? Enhanced identity recognition, it's a risk assessment based on what we know, and the sources that we have checked, the probability of the identity posing risk to you is going to come back to you in some form of a decision score.
User population in monitoring provides you the opportunity for that outsource of a manual review in the event that the risk is high enough that you need a step-up process, and then lastly, which is really what my group does through the consulting aspect, we help build that identity process flow based on your organization, based on what your current capabilities are and what we believe, collectively, your needs will be long-term. Here's an example of the workflow and how it works. Imagine that you needed to provide service across multiple products, multiple channels of your business, and I'll give a real quick example of multiple channels within your business. There's a company that they buy and sell tobacco products. Tobacco comes in a lot of different forms, which it comes in chewable, it comes in smokable, it comes in vapor, and it comes in … A new format is going to be introduced to the market relatively soon.
With that, you have four different products, all of which have one standard requirement. You have to be age appropriate to become a consumer. Certain products, you need to be a different age, so the level of authentication to do service with that company varies by product. We're able to help orchestrate for them, based on the consumer themselves, which product they qualify for and which products they won't. An example here is the incoming user data. That's the information that's provided by the user. Coming in, I am who I say that I am. We're running through that single API. That API is drawing through the workflow decision saying based on the identity elements and the information that we've collected on that identity, the decisioning process says to go to, what?
The example that Tom's going to share for you in just a few moments is the first step of that step of authentication. The identity verification, that could include device. It could include the user of the device. It could include the biometrics of the device itself. How does someone interact with the device? Where is the device coming from? How has the device been used in the past? You have document verification, which my next slide's going to share with you an example of what documentation would look like, account verification for existing consumers. We can use your own data for existing consumers. If you have your own black lists or white lists, we can incorporate those into your decision flows. We can take internal, external third-party and Experian data all into that decision workflow process to render for you a decision. How do we do it? One-time passcode is an example of that step-up authentication. If the process and the risk score suggests the high element of risk, we could send a one-time passcode, and that could be conducted through the form of a text or through the form of an email. There are a couple of ways to do that. Some instances, do you need to verify the phone number? Do you need to verify the email before you send the text? Depends on the product, depends on the risk, depends on the transaction amount, but we can help you with that. We can help you verify the email or the phone number in advance of, and/or take it for what the customer's worth because the risk score is within a certain threshold.
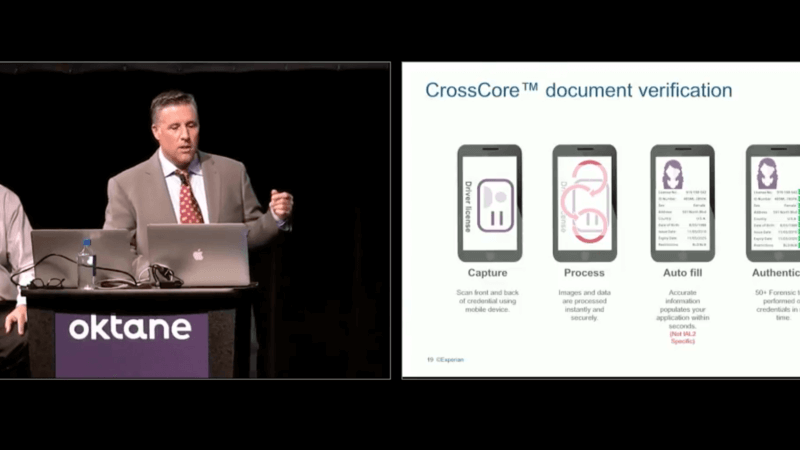
Biometrics. We talked a little bit about physical biometrics as well. We can help deploy step-up authentication through biometrics, and there's been a couple of sessions, and certainly, many of us are probably already using biometrics today. I know for myself. I use the thumbprint to log into my accounts. Facial recognition and other opportunities are becoming more and more prevalent, almost standard at the time that your device is being purchased or deployed to you. Device intelligence. We spoke a little bit about the importance of device intelligence and where that consumer is coming from. Document verification. I'm going to show you that example next, and then, we're going to give you an example in a demo on the knowledge based authentication. How do you create an easy account opening process? I went through that quickly, but I'm going to share with you the example here of manual documentation. Over 50 authentication tests can be conducted on that driver's license. All of that comes down to font, the spacing of the font, the placement of different elements of that document, the hologram behind it, the color that's used in the font, the image quality, the image color, the background color. All of that information is included in the decisioning process outside of just, "Is the name on the document itself valid?"
We take all of those attributes of the driver's license or state-issued government … That could be a visa, passport, any other thing. We run that up against a number of data elements and come back with you for a score. That score would suggest, yes, the individual has passed document verification, which is typically a higher step-up process. If so, if they have passed, proceed, and if they have not, well, what's the next step? That could drive you to a one-time passcode. It could drive you to a second form of identity documentation, things of that nature.
Sometimes, it even requires in certain industries to send in the physical documents themselves, paper copies of certain things. The industry is doing a whole lot better at not having consumers or high-risk individuals send photocopies of documents, photocopies of licenses, photocopies of birth certificates and social security cards. This is why, because we've been able to deliver a solution that allows you to get a real-time decision with a high degree of confidence that you can take action on immediately. When you have to request documentation from a consumer, you're talking seven to 10 days. At that point, they've taken their business elsewhere and/or your cost per sale has gone up dramatically. How does it work? We capture it, take a picture of it. we process the data behind. It pre-fills on a form all of the information off of that document, driver's license, passport. It'll authenticate each of those steps and elements, provide back to you which of those elements passed, which did not, and then a response to verify. It's relatively real-time. It may take a couple of seconds. How does it do that? It's taking hundreds of photographs very rapidly as opposed to just one, so that we're able to determine that it's a live document.
Here comes the exciting part. How do you put it all together? Tom's going to share with you how Experian and Okta have come together to provide the solutions that we just shared with you in a way that delivers an immediate response back with a high degree of confidence relative to identity proofing. I really appreciate your coming today. Thank you very much for your time, and Tom?
Tom Smith: Sure.
Chris Danese: Thank you.
Tom Smith: Thanks, Chris. I'm just going to make a couple adjustments here. Okay. What I'm going to do is I'm going to go through this architecture diagram. For any of the geeks in the room, this should be a … I'll go through it pretty quickly, but I wanted to give you kind of the Slideware overview of the actual software demo that I'm going to show you. The way this flow works is that the user is going to fill out a form. They're going to fill out their personal information. There's a number of different ways and a number of different points where you can insert identity proofing into the registration flow. In the case that I'm going to show you, the user must pass identity proofing before the user record is created in Okta. There are other situations where you might want to have the user record be created in Okta, and then insert identity proofing when that user tries to do some kind of step-up privileged access or get access to a protected resource, but again, the flow that I'm going to talk about today is inserting identity proofing into the beginning of the registration process.
The way that works is that the user fills out a web form and submits that to an application. The web application takes the information from that form and sends it to the CrossCore API. Now, as Chris mentioned, the CrossCore API can do a number of different things with that information depending on the way you've set up Experian, but it basically, and this is what I'm going to show you in the demo, assigns a risk score to that set of data that the consumer has submitted. In this case, if the risk score is above a certain threshold, in this case, it's about 500, then the Experian's going to give that user a thumbs up, return with the accept response. If the risk score is below that threshold, then the Experian's going to return a refer response along with some knowledge-based questions that the user has to answer. The user answers those questions, and then hopefully, the user has answered enough of them correctly so that the combination of their precise ID score along with the answers to those questions gets them to get that thumbs up from Experian, and then that user record can be created in Okta. Basically, you get to that thumbs up state from Experian, and then the application calls the Okta API to create the user record in Okta. By default, and many of you probably know this already, when you create a user record in Okta, an email verification is sent to the user, and that's what the user clicks on to complete setting up their account including setting up a password. It's not required, but that's the default Okta registration flow.
What does that look like from an end-user perspective? I've got over here on the left, kind of a vanilla interface for what that experience looks like from an end-user perspective. Then, over on the right, we're going to see the server responses coming back from Experian and from Okta. Our first user is Roger Stanley. Roger Stanley is going to fill out his information, and he is going to register. Okay, great. We've gotten back a success response. That response is coming back from the CrossCore API. You can see we've gotten an accept and the value that is generating that is this score of 737. I mentioned that in this case, that threshold was a score of 500. In this case, the score was 737 based on all of those factors that Chris described that Experian is evaluating, so Experian is recommending an accept decision. At this point, Roger is good to go. We're going to press the register button again. That wouldn't happen in the real world. That would all happen automatically. I'm just kind of breaking it out here for demo purposes, but when he registers, now, we're going to get a response back from Okta saying, "Great. The user has been provisioned." Now, Roger has a user account in Okta, and he can go in and complete setting that up, and I'll walk you through that.
Tom Smith: So this is Roger's Welcome to Okta email. It's going to go ahead and activate his Okta account. Choose a password. Bless you. Okay. So now he's been redirected to the application. He's now fully authenticated, fully registered with Okta, all good to go. We've saved his record of that transaction in his Okta user profile. Let's see what it looks like when the user doesn't pass that initial score. So now I'm going to be Rodney Keys. Rodney Keys is going to fill out his form. He's going to attempt to register. And in this case, we'll look at the right side here quickly, the response coming back is a "refer." So Precise ID is saying this guy is not ... the data doesn't check out to the same degree of confidence that it did for Roger Stanley. He's got a score of 443. So we're going to recommend that you challenge Rodney with some knowledge based questions.
So we've got those knowledge based questions over here on the left. Just for demo purposes, I've highlighted all the correct answers in green. But we're going to see what happens when Rodney gets some wrong answers. So he's going to attempt to register there, and he's going to get a "sorry" message here. So at this point, the directive is to call customer service or to call the help desk, but you could also here have another step in the Experian identity proofing process, where maybe you ask Rodney to submit his driver's license. So take pictures of his driver's license and then complete the full registration process and get that thumbs up from Experian. So lots of different ways that you can configure this.
We don't want to leave Rodney hanging, so let's try that one more time. I'm going to try to register again. So of course, we still again get the "refer" response, with the challenge questions. This time I'm going to leave all the correct answers checked. I'm going to attempt to register again. And this time we get a "success" response. And Experian is basing that based on Rodney's initial Precise ID score, combined with those correct answers to the knowledge based questions. So now Rodney's good to go. He can go ahead and register with Okta. He's been provisioned with Okta. So now he has a user account in Okta. He just needs to go through that same email activation flow and he'll be fully registered and authenticated. So those are two very kind of basic ways that Okta and Experian can work together. It's a very complementary solution, with the identity proofing from Experian and the user registration and authentication with Okta. With that, I'm going to turn it back over to Chris. Do you want to talk about the last thoughts? I think we've got one more ... Yeah. Why now, why Experian, why Okta.
Chris Danese: Well, I think the obvious reason is because of what we just showed you. However, reliable and accurate data, one of the things that is a constant concern to customers and clients is the reliability of the data. Where's the data source coming from, what is the reliability of it, how recently or frequently is that data updated, am I making decisions off of the freshest version of that data, or is this stale data? The reliability of the data that Experian offers is by far the most superior in industry. It's what we do. It's what we've been doing for decades. And the way we deliver that to you, instantaneously and refreshed, many of our data sources on a real-time basis, give you the most reliable information, hour by hour, throughout the course of the day, depending on where that data source is coming from.
Superior decision and analytics. So ultimately, there are so many configurations that we could show you in this demo, depending on the type of transaction, the type of business that you're in, depending on the type of service that you're looking to provide. Anything and everything could be customized, and quite frankly, with CrossCore, I don't really see that there's any limits. What's exciting is the fact that new use cases continue to come up, and we're able to continually to solve problems for clients, that first of all, those problems didn't exist all that long ago, but very quickly, very readily, we're able to put a confident solution for them in place. The continued innovation, this is a perfect example. This entire conference is an example of just the innovation that continues to get introduced into the identity proofing component of businesses. I can go back to the days of when I started in identity proofing, and that consisted of looking at a copy of a check and a signature, and matching it to an application. We've come a long way, and I can't wait to see what the next couple of years bring to us.
Continuous innovation, as we share in the state of the art technology. Experian has recognized the fact that we do a lot of things well, but we don't do everything well. And where we need support, we bring in partners like Okta and many others, to make sure that you, as a client, as a consumer, have the most up to date, state of the art technology available at your decisions, to help deliver for you the solution that makes sense based on the business that you're in, to get you that decision that you need as quickly as possible. And lastly, the partnership, this is a perfect example of partnership. We have many relationships with industry leaders, just like Okta, to help match your risk with our capabilities, to make sure that there's no problems that the industry is facing that we can't help you solve. We've been really excited to work on this project together. I think the example that we put in front, although is very simplistic, it just goes to show from a user perspective how quickly we can provision an individual with really relatively no disruption, as quickly as possible. All of the things that we said at the beginning of the presentation, the example shows how we are able to do that.
So we do have a couple of minutes left. If there are any questions, we will be happy to take some questions. Yes sir, thank you. This question's for Tom.
Speaker 1: Thank you. Very eye opening presentation. My question, there's two parts to it. First, are there any regulations that mandate ID proofing for the healthcare space? That's my first question. The second question is, Okta plus Experian, have you guys implemented ID proofing in the healthcare space? Clearly, I'm from the healthcare space, so I'm on the verge of trying to get something like this done and I'm very interested. Thank you for the presentation.
Tom Smith: You want to take the first one, with the regulations?
Chris Danese: Yeah. Absolutely, there's regulations in every industry. The healthcare industry is by no means an exception to that rule. I am in the process of finishing up a very large project, specific to identity proofing, with a healthcare provider that any one of us would see their commercial on a regular basis. They don't call it identity proofing, it's customer assurance or policy holder assurance. Some of the differences in the healthcare industry is that there's an agent involved in that transaction, which makes their identity proofing process a little bit different than what we're seeing in other industries. So we're ... there's two parts to that. There's identity proofing of the agent, and then there's the identity proofing of the policy holder. So there's two pieces of that. We've put together a very custom solution for this client, through the use of CrossCore and some of its capabilities, but I will say that they're different, this example. Our mindset was geared towards financial services, but applies to any, but there are other sources of data that we introduced to the healthcare client that are a little bit different than what you would traditionally do. Again, it goes to regulated data, unregulated data, and what were they trying to solve for. Specifically, their area of risk was with disability claims. So where they were experiencing risk was more in account takeover than in identity theft. So Tom is a disability holder. He signed up for a policy several years ago, and his $35 a month comes out of his DDA account monthly. The last time he looked at his policy was when he sat down with his agent a couple of years ago. I'm the fraudster. I have, through account takeover techniques, gained access to Tom's account. I have filed a disability claim. That disability claim was disbursed. And I, the fraudster, because I changed either his bank account information or his physical address, am now receiving the benefit check. All of which Tom has no knowledge of. So the difference is, are the types of fraud that you might be experiencing. Healthcare has some unique fraud challenges. I will say, from my observations in working at the healthcare industry, they have a lot more catch up to do than some of the other industries, but it's great to be a part of projects like that, to see that the focus is there, the understanding and the appreciation for what needs to be done, and finally, the investment in the technology to not create so much disruption to the consumer. In today's environment, there is a lot of paper trail in the healthcare industry that we're able to help solve for in a much more real time, with a higher degree of confidence.
Tom Smith: As for customers, off the top of my head, I don't know any specifically, but I have been a part of discussions recently that are very far along in the healthcare space, with a combined Okta and Experian solution.
Chris Danese: Thank you. Yes, sir. Do we have time for one, I'm sorry?
Speaker 2: Last one.
Chris Danese: Okay, so you're it.
Speaker 2: About two minutes.
Speaker 3: I'm sorry, where was the hand?
Tom Smith: I'm sorry, Rocco, did you have a question?
Speaker 3: Right here up front.
Tom Smith: We'll go with you, Rocco. Sorry, Andrew.
Speaker 4: So on your document scanning and verification, do you guys have a roadmap for combining that with taking a photo of the person so you can tie the real time person to the document?
Chris Danese: I would be happy to share with you our roadmap for all of our CrossCore capabilities. I think we can make some of that information available immediately, through the course of the presentation I think we'll be able to get your information, we'll send that to you. But absolutely, yes, there's ...
Speaker 3: So guys, we're going to wrap it up for this session. I would say if you have questions, be sure to seek our speakers out. We are getting ready to head down to lunch. Maybe they can find you there. And enjoy the rest of the conference. Please be sure to drop off your card at the back as you go out. Thanks for joining us today.
Chris Danese: Thank you.
Tom Smith: Thanks everybody.
Given today's fraud attack vectors, 2018 is they year to talk about identity proofing. Watch as Experian details its findings in the Experian Global Fraud Survey and also how they utilize Okta's platform for a variety of combined capabilities across analytics and credential insurance.
Speakers:
Christopher Danese, Business Consultant, Experian
Tom Smith, Partner Solutions Technical Architect, Okta