Oktane18 Integrating Office365 with HR and Security Systems
Transcript
Details
Sabrina: I hope all of you are as pumped up about the networking effect as I am after Todd's speech. Although we may have coined this term recently, it's from the inspiring stories through your journeys as customers that has come to fruition. I'm Sabrina. I work for Okta in the Product Marketing Group. There are no roadmap or future looking things in this presentation, but if we did have it, that would be covered by this legal disclaimer. This session is mostly about Nexteer who is the automotive industry leader. Their journey of adopting Office 365 and integrating it with their HR and Security Systems. I'm going to do a five, seven minute painting the backdrop. Giving you the context so that you can see how Nexteer’s journey is closely related to yours, regardless of which industry you're from.
You as IT leaders take on this journey of digital transformation because you're trying to keep up the pace of innovation and productivity for your organization. You're adopting best of breed applications. You're bringing in all the legacy infrastructure and on-prem applications. You're automating, integrating constantly to improve the efficiencies of your people and processes. While you're doing all this digitalization, you'd realize that the attack surface on your infrastructure application has broadened and so you're weaving in security into all the layers of your systems. Finally, you're preparing for the worst possibilities through tools that will help you analyze and respond and remediate when you're under attacks. As you're going through this entire journey, identity is that linchpin that's tying all these systems together. While I have logos, I've a few applications, vendors, networking vendors, security vendors up here, you know that the Okta integration network has thousands of these applications that you can search on our website, on our catalog.
Talking about the popular top used application, Office 365 is one of our most used application both in terms of how many companies that are our customers have adopted it and how many users log in every day. Now, why is Office 365 so used by Okta customers and why is Okta the choice of identity platform for these customers? Let's take a few minutes to understand that. Now if you are deploying Office 365, these users, their identities have to present in Azure AD. There's no way around it. Most customers will start off with having on-prem AD and they have to make decisions about what is going to be that single source of truth for them. As they decide between Okta and other options out there, they realize that Okta has the smallest foot print. It has the fastest time to deployment without having to open any firewall holes and all that with out of box high availability. The simplicity of Okta's architecture is even more apparent when you have complicated AD environments. If you have many different AD forests that need to be inter connected either because you have a large organization or perhaps you have a number of subsidiaries that have their own AD domains. In all these circumstances, Okta's deployment is fairly simple. Now if you remove Okta out of the picture, that's when you start to realize the simplicity that you have.
If you remove Okta out of the picture, you're left with a number of tools and choices that you have to make. Do you want small footprint or do you want full federation? Now, if you choose full federations, they go with ADFS, so you get high availability. Then you're going to have to invest in a number of servers. Whether you want them to be physical servers on-prem or virtual servers, it will be a complex architecture. The architecture gets more complex based on how many AD domains you have because you have to have that infrastructure for every AD domain.
Then you might also have to put in supporting infrastructure for your complicated AD environment with SQL servers and load balancers. Now, even if you take on all this pain, will that infrastructure support your identity platforms integration with your HR systems, with your security systems of your choice? That's the question. So, why? Why should you care about that? Because automating user lifecycle is not just about enabling single sign on into a number of cloud applications. It's about making sure that the user has access to their birthright applications and the right attributes of those users have been passed on to that application so that they can access what they need to access.
That's not just at the time of on boarding or off boarding. It's through the entire lifecycle of the user. On the right hand side you'll see a number of applications that can serve as masters into the Okta identity platform and this is very unique about how Okta is deployed both in terms of upstream and downstream application being able to get parameters and attributes passed on. Now you see this and you realize, oh, this makes it really easy for us to adopt the application. But you also realize that this is one sure way of securing these applications because when you remove the manual provisioning, which could have errors, that could have delays, all of which is opening up vulnerability windows, then you have secured these applications.
Now you can add the second factor of authentication into these applications. You can integrate this with your network that Okta threatened sites that you saw at the keynote with your network elements like the traditional firewall. You can do that to secure access for both your on-prem and your cloud applications. For those of you who are regulated by compliance, you may want to deploy CASB, the cloud access security brokers to control who's getting access to what. Regardless of which industry you're in, you want all your threat analytics tools to get real time information from your identity platform in terms of who should have access to what so that you can respond quickly and remediate in case of threats. With Okta, you have a wide variety of vendors to choose from, so you're in control. With that happy thought, I want to introduce the Chief Information Security Officer from Nexteer, Arun to share his valuable insights as he took on the journey of deploying office 365 and integrating. Welcome Arun.
Arun: Thank you Sabrina. Good morning everyone. It's a pleasure to be here talking about Nexteer's journey as we move through Office 365 HR system integration and so on. Hopefully you'll enjoy the talk as much as we enjoy deploying it at Nexteer. A little bit about Nexteer. Nexteer is a pretty old company started in 1906 actually and it's been around for quite a while. It's a global company with a rich tapestry of diverse cultures, great people who are focused on a sense of innovation and filled with collaborative spirit. That collaborative spirit is one of the key reasons that this particular project came to light and was brought to life. Today we're on the age of the fourth industrial revolution and is really a very exciting time for all of us in the industry. We have chartered technology such as mobile, cloud, the IOT, Artificial Intelligence, it's really terrific. It's a great time to be in IT, in security. We're able to fuel digital transformation as Sabrina indicated earlier. It's really a really exciting time for all of us. I think we can use this age to propel technology and actually walk in the way we spoke earlier. When Todd was on stage he was talking a lot about identity is a new challenge, the challenge of today and that is really true.
The reason that's very true is, with all this technology out there, the risk of is really humongous. It's a lot of opportunity, a lot of risk and how do we manage that risk? The risk out there, based on security perspective, we all heard about the data bridges, the hacks, and these kinds of things. But also privacy is the elephant in the room now. If you're a global company like us with presence in Europe, regulations such as GDPR can inflict up to 4% of our revenue as penalties. So, we want to these risks seriously. Whereas in the one side, we can feel digital transformation. We need to do it in a measured responsible manner.
How did we go about this process at Nexteer? It was a three phase journey. First of all, we embraced the cloud and we've got a variety of cloud applications, things like Concur, Office 365, DocuSign and all these things. The second step of it was to actually integrate our Okta ecosystem with Successfactor HRS system and actually drive provisioning automatically from success factors. The third and last pillar was actually integrating remaining parts of our key security partners such as Proofpoint and Scalar into the security architecture. With that preamble, let's get started. At Nexteer we chose Office 365 for three key things. The first business enablement because as a company grows, and we grow through mergers and acquisitions and joint ventures, we want the ability to have a platform that scales very well, integrate new companies. But at the same time for existing workforce and partners, have a system that can actually fuel productivity and collaboration.
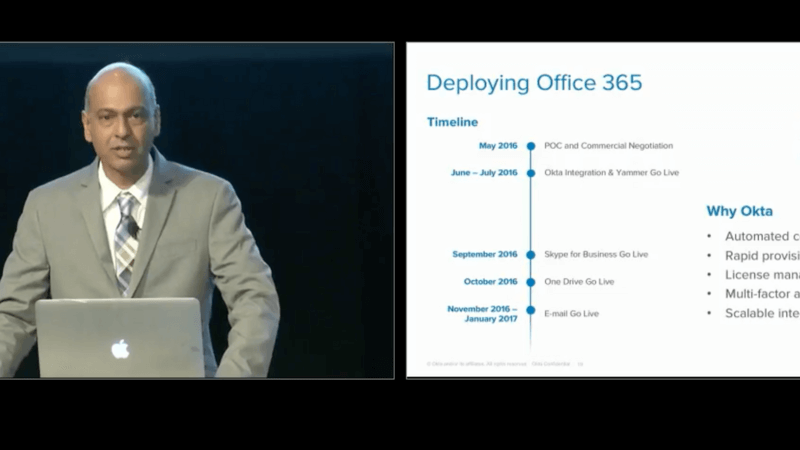
Secondly, cost optimization. We're in the automotive industry, and like most industries it's always a good thing if you can actually reduce costs. And, through Office 365 we are able to save costs by getting rid of things like AT&T web conferencing and so on. That was a good thing. Last but not the least, Okta is a security platform, an identity platform and really helped us to actually be mindful of those regulations that we talked about earlier, mainly the GDPR and so on, because we can secure the perimeter, secure users and data. Those were the three key dimensions why we went Office 365. A little bit about our Office 365 journey. To the left you will see a timeline that describes it, but simply now touched upon some points. With Okta we were able to power through the deployment. Really, it just took matter of a day or two to plug in Office 365 into Okta through the provisioning. Sabrina talked about all the technical moralities and they all very true. We were very fortunate with that. Some of the reasons we chose Okta for Office 365 was the automatic provisioning and de-provisioning, the ability to do seamless license management, the ability to provide anywhere, anytime, authorize access, the notion of multi factor. We started that at day 1 continuing Office 365, so as you provide Office 365 service for collaboration, whether it is SharePoint or any other service from O365, we can make sure our user base can access it from anywhere, anytime.
Last, but not the least, it's really a platform for scalable integration, so we can plug and play original Microsoft services that come in through the product pipeline and leverage them to fuel the digital transformation. Now I'm going to talk a little bit about our success factors of the master journey. This is really key. I think Serena touched upon it earlier. The fact is you need to have a single pane of glass, and a single source of truth. Just to rewind a little bit. When I joined Nexteer, I actually conducted an enterprise risk assessment. Out of that enterprise risk assessment, we had 7 key risks. Some of them were loss of intellectual property, cloud computing governance, onboarding and offboarding, and network security. One of the reasons we chose Okta, was the ability to actually achieve exactly the downstream provisioning driven through the HRIS system. At the end of the day, Nexteer is a company based on people. We want to reinforce the 1 Nexteer focus, and actually partner with the business, which is particularly HR and IT, to ensure this 1-stop integration. Back in the day, before we had this project, people used to come, people used to go, and there were a lot of risks, which we'll talk about in a minute.
What is the opportunity? In the past, before we integrated the HRIS system into us on-prem active directory and powered it to Okta, it was a bit painful because there was some data in the AD. There was some data in the other database systems. It was really crazy. How were we able to accomplish all this? That's why we wanted to get rid of these islands of information, if you will, and tie them into 1 cohesive favorite, powered by Okta and the on-prem active directory integrated with the success factor's HRIS system. The integrated hired to retire, identity life cycle management program that you put together integrating success factors through Okta, through power provisioning and privileges and the active directory, and cloud based applications. It's really a very unique thing because we were able to pull it all together with Okta as the hub of this identity integration.
As I mentioned earlier, before we had Okta, before we integrated the HRIS system through Okta, it was a pretty painful process when people came on board, right? There were a lot of tasks that they had to do like signing up for email account and creating users in the active directory, and various other tasks. Even if each individual task took 5 minutes to 10 minutes each, the lapse time, the connected lapse time was hours to days, right? Now look on the right hand side. All that stuff is being done automatically. When a new employee comes, a record is created, a button is pressed, and a lot of these things are done automatically. One can't even begin to imagine what a gain of productivity savings it is to our company. It's really fantastic. It's really proof testament of partnership between HR and IT to drive and fuel visual transformation.
I'm not going to read everything on the slide, but essentially, at Nexteer we have a movement called, Walk in the User's Shoes. This cohesive integration between Okta and success factors help power a lot of user self-service and 1-stop shopping and use for applications across the integrated ecosystem. It allows us to be more productive. Allows our global teams to collaborate and drive business efficiencies. Last but not least, minimize some of the risks that we had faced earlier, prior to this project. Now I'm going to talk about in medicine, where Okta and all the powerful legal systems fit all together. Before I do that, I want to introduce the trifecta of people, process and technology.
First, people. People are the heart of any company. They are a real asset. How do we make sure we provide them the right tools at the right time in a secure manner? I'm guilty as anyone else here, going home, turning on the phone, going to my home computer, logging in. How do you provide those services in the right manner? It's really a powerful paradigm shift that Okta helps us achieve. It's not only limited to workforce inside the company, but extended partners, suppliers and so on. Next is process. It's really key, especially when you embrace technologies like the cloud, and so on, to have good governance, good risk management, and work in a secure way. Sabrina talked about earlier the notion of identity analytics. Who's using what at what time? Looking at the data in Okta to see where the risk points are. That's another side benefit. It's really a great thing. As we seek to use Okta and leverage identity cloud, we can really benefit a lot.
Of course, knowing the fact that we integrated with the HRIS system, it's very important to manage entitlements as people move to the hired to retired life cycle with promotions, leaving the company, and so on. Turning off the access in a timely manner, and providing them access in a timely manner. Technology is the last one I'm going to talk about. The thing to note for technology is really 3 parts, right? The first thing is Okta and all the powerful legal systems a part of the security strategy that we've deployed it next year and the 3 dimensional application, services and infrastructure. That's the first thing.
Secondly, we need the ability to also at any time provide secure access anywhere, anytime, in an authorized fashion, so multifactor authentication or adaptive multi factor of indication. These are big things. Of course, obviously, we need to have cost platform synergies because Okta can be the traffic cop that helps pull together all the different systems that we have, and different partners, in addition to delivering good services. Back in the day, if you had a house, how would you protect the house? You'd put a barbed wire fence around the house. You'd probably have a dog patrolling the fence, and you would say, OK, my house is very safe. That's not very practical now a days because if you look at the enterprises of a digital house, you can't do that anymore. You're letting people in and out of your house digitally speaking all the time. Whereas the fence is important, which is like a fire wall, the dog is a content filtering system, and those kinds of things. At the end of the day, the thing that provides you secure access at any time is the notion of identity. Identity is the new digital parameter. No fooling, we heard a lot about it this morning from Sabrina. It's very true because it's not only the fact that you have a firewall or content filtering system, or you're able to get in the door, but how do you use your identity to provide you secure access to all the apps and data that you need to use in the enterprise?
As identity is the digital parameter, I introduce you to the notion of what I call the identity coin. That's 2 sides of the coin, the physical side, and the logical side. The physical side is well known to all of us, well understand, person, device, location, right? We get that. What about the logical access? The logical access is attribute based control, behavioral based control, contextual access control, and granular access control. How do you use both dimensions of identity coin to secure the digital parameter and use identity as a linchpin to secure the enterprise? That's a real paradigm. That's why technology success is adaptive MFA, adaptive SSO, as Tarp mentioned earlier. They're very very key. We don't have adaptive SSO, but we do have MFA. It's really great.
I know it's also paradigm shift when we start talking biometrics and behavior, but I think what we also have is device of invisible identity. The passwordless enterprise. The only way to accomplish that is to actually use both sides of the identity coin, the physical and the logical. Now, I mentioned earlier that Okta is the linchpin of a lot of security services we provide and mapped to different security layers, we see the different partners, how they play together and this is really the heart of the security strategy. There are others solutions that we use that are not listed here, but yesterday I'm talking about Okta, Proofpoint, Zscaler. I put on the slide where those three fit into the security strategy and our security architecture.
Let's talk a bit about Proofpoint and the integration with Okta. One of the fundamental themes that we have in our security strategy is the notion of the three I's, right? The first, identity, second interoperability and the third is integration. And nowhere is that truer than in the next two slides I'm going to talk about, in Proofpoint and Zscaler. Well and actually, Okta is the hub that pulls from my on-prem Active Directory and powers integrations and single sign on for apps, but also populates the Azure Active Directory and the O365 integration and with the case of Proofpoint, it's really a big factor for us because prior to that integration, prior to Office 365 and the downstream provisioning, we are to keep loading people, users, every day, every week, et cetera.
We don't need to do that anymore, right? Because Okta populates as your Proofpoint picks it up from the Azure Active Directory. We can put Proofpoint rules in there. So this is really an example of a synergy and again, Proofpoint by itself is a really powerful tool that allows us to strengthen email security. Remember I mentioned that network security and email security are one of the key risks. So, this integration and Proofpoint by itself. And now to Zscaler. So Zscaler is actually a key technology in our security arsenal. And it has a lot of users. We actually fell into our Zscaler implementation because when we went Office 365, we faced a lot of network performance problems. And the reason for that is quite simple. Whereas Office 365 is all managing powerful platform, the way client-based communication work with Office 365 is very heavy, so each client may open up to 20 connections, so you can imagine the problem with the network. So, we actually implemented Zscaler for its particular use and value to actually streamline the connections between Office 365 and our internal enterprise.
And it has some other advantages too because the Zscaler, being a flexible Cloud platform, we were able to eliminate the device-base appliance proxies that were also contributing and exacerbating those network problems when we went O365. It allows us also to give about 40% of our bandwidth on account Cloud platform to O365 traffic. So, all in all, a good thing. And in all these cases, the thing is its transparent service provision. Our users don't have to log in. Okta powers the service provision directly to Zscaler and Proofpoint, so this is a great thing.
Now, some things about the deployment playbook. It all starts, actually for all these technologies in a security portfolio, with Office 365, Okta, Zscaler, Proofpoint. Always starting with a business drivers and the vision where these technologies are going to fit in the portfolio. You need to be founding secure architectural principles because if you don't, now things are going to play together. They don't play nice. It's also a lot about business partnership and this is no truer than with our success factors' implementation, some of the things that benefited us, a strong business partnership, strong change management, treating it like proprietary software development project with scalable environment, proper use case testing, getting the global teams. So at all points, it's about that integrated business partnership. But as we go on, it's the notion of providing robust service assurance as well. And then the notion of federation because next year, as we provide services, we have a tagline called the power of federation, so using these tools in a secure manner, providing this service transparently.
So, the key takeaways that I will give you from our journey so far, because I want to leave time for questions, are on the slide here. Harnessing new technologies in a secure manner, managing security across the enterprise, making sure you have security architecture, you have the different layering of where the technologies fit together, using identity, interoperability, integration, utilizing a federated approach to security management. And really just implementing a cohesive set of security tools. And at the end of the day, pulling all this together is identity is a new digital parameter and Okta as a cornerstone in that particular journey.
Before I go on to Q and A, I have one more slide and I think as we get into the fourth industrial revolution, particularly for a manufacturer like Nexteer, we have a lot of opportunities to fuel digital transformation, enable the business by connecting devices through the IoT, through mobile and Cloud. And as we provide more and more of these services, identity is going to be certainly the cornerstone where there's opportunities not only for tradition identity as we know it, but also machine identity. And I think Okta solutions as the API Access Management can help in that realm as well. So I think the fourth industrial revolution is here. Identity is a challenge of the day. And I think we can all be very proud that we are customers, partners of Okta and it's part of our toolkit. I think that is time for Q and A. I left some for Q and A. Any questions?
Speaker 1: What was your biggest challenge as far as provisioning to Office 365? Did you have your ADs on-prem and your Azure AD in sync? Any GAL issues with global-
Arun: Yeah, as I said, thank you for the question. No, actually, to be truthful, we already had Okta in place before Office 365 and there was the line of thought saying, well, you know, why should we deal with Okta? Let's just use Azure AD and ADFS? And I can tell you we tried and we fail miserably, right? On the flip side of it, we had some design with Okta Professional Services, two hours here, two hours there. And in the span of four hours, we connected everything. It was totally seamless, there were no issues, there was nothing. And I'm so glad for that.
Speaker 2: Just to ducktail off of what he was saying, if you don't use Okta as the lifecycle management tool, what are the challenges for integrating and moving your user population into Office 365?
Arun: I think there's quite a few and I think Sabrina’s slide as well was very powerful. So the first thing is ... there are a couple of things. You need to rely on ADFS, you need to rely on syncs, you need to punch holes in firewalls and it's really a very complicated story. It's not a transparent service provision, so it's not easy. So the advantage of Okta DoS for the architecture is make it almost plug and play, really, assuming you had Okta already in place. It makes your life very simple and did for us too. I mean, we tried for two or three weeks in the infrastructure group, do it the traditional way and it was an abject failure, whereas in the span of a day or two, we plugged into Okta and it was really quick.
Speaker 3: So, continuing the theme of Office 365 provisioning, or deep provisioning in this case, how do you handle the deep provisioning of users, how it will just kind of block them from signing in? How did you handle the licensing, pulling licensing back?
Arun: So this is the first complex answer I'm going to give, sorry for that. So, actually, now that we have HRS-integrated provisioning, so typically what happens is if a person is going to leave, the HR person would press the button success factors and they would say, well, they're no longer with the company, as an example, so they get pin. Then what happens is we go into Office 365 and we change the flag in Office 365 and give it a 30 day count-down. At the end of 30 days, it's automatically decommissioned, no issue there. It's just all integrated. And we can set that to whatever we want, we just set it to 30 days, that's all. And we're going to recover the record for another 30 days, but after 60 days, they're tombstoning of that account. No more questions? We have about nine minutes, so feel free.
Speaker 4: I'm curious about the financial impact for the ease, the business enablement provisioning, deep provisioning, how much of a financial impact does it have on your company?
Arun: I think the financial impact is less of a story. Any time you look at any project, you have the tangible benefits, which is the project deployment cost and so on, the intangible benefits reflected in things like increased productivity, reduced paperwork and so on and better credibility with the business and I think that's where this particular project really shone. We had some project deployment costs, of course, for integrating Office 365, but the great power that we got to that is the time savings, the productivity savings, that HR can, where they used to chase people and a lot of inefficiency-, those have gone. And how do you quantify that? And I think even if you take end users that you save two hours in provisioning, I mean, when you count 7,000 users in the company, that's a lot of savings of time, right? And actually, you can get people to work on things that they should be working on, rather than just paperwork. Okay, so if no more questions, then please complete the session survey card and you will get an entry to win $100 Amazon gift card. So thank you very much everybody, appreciate your time.
Okta's identity platform is the linchpin that ties legacy apps, best of breed, and automation into one secure, efficient platform. Watch this presentation if you're interested in OIN managing identity and apps for your HR department.
Speakers:
Sibrina Subedar, Product Marketing Manager, Okta
Arun DeSouza, CISO, Nexteer Automotive