The Benefits of Identity Federation for U.S. Government Agencies
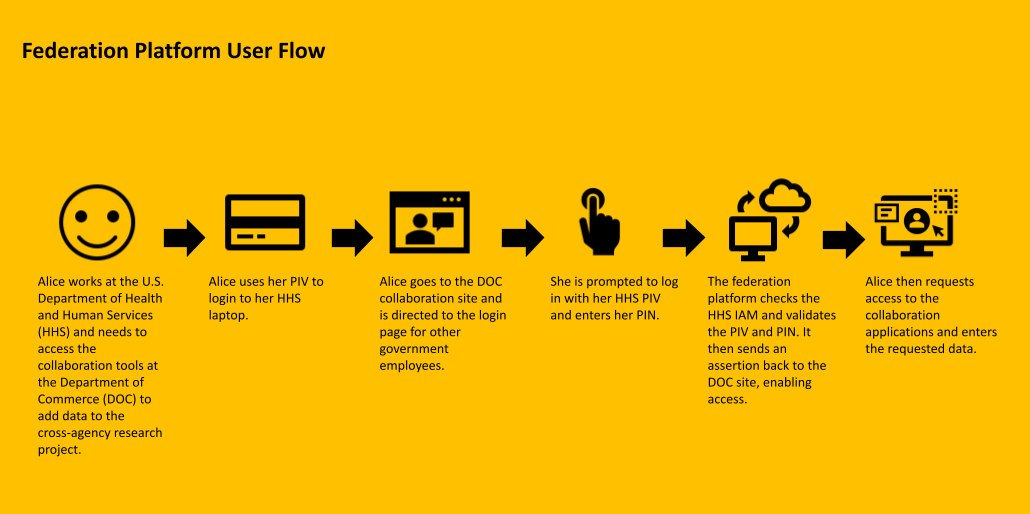
Imagine a scenario where an employee at the United States Department of Health and Human Services is working on a cross-agency project with staff at the Department of Commerce and the State Department.
Employees from the three agencies work together, share research and documents, and draft reports using common collaboration tools. All of the agencies use Personal Identity Verification (PIV) credentials, but secure, seamless access to one platform is challenging. While the PIV and Common Access Card (CAC) are interoperable across agencies, acceptance and use of different agency credentials is not something that has been adopted among U.S. agencies.
Federating government employee identities is feasible. Identity federation isn’t new and is actually called for in White House Office of Management and Budget Memorandum 19-17, “Enabling Mission Delivery through Improved Identity, Credential, and Access Management.” The idea of leveraging a credential issued by one organization and using it at another has existed for years and is something agencies do for citizen access to certain services. But it has not taken off for employees or contractors, even though the smart cards issued by federal agencies all work from the same underlying technology standard.
Cross-agency credentialing has been discussed but never implemented – even though the same background check is typically used, and credential issued – leaving each agency with a siloed identity and access management (IAM) system. The alternative has been issuing additional PIV or other less secure credentials to enable this cross collaboration.
Enabling standards-based federated identity across U.S. agencies could save costs in the long run – no need to issue multiple credentials from different agencies – and improve security since weaker security technologies would not be deployed. With a standards-based solution, agencies can use any IAM. All systems will work together, enabling better value for agencies and negating vendor lock-in.
The U.S. government has a big opportunity to accelerate its digital transformation by embracing identity federation. As multi-factor authentication and single sign-on have become the norm, and with Zero Trust on the horizon, it’s time to enable federation.
There are several ways to do this across U.S. agencies, the simplest being a standards-based federation platform. This platform would sit between different agency IAM systems. A new login page would enable employees or contractors from another agency to log in using another agency PIV. The federation platform would validate the credentials from the issuing agency and send an assertion to the agency saying the credentials are valid. Access could then be granted, and the individual could request access to the necessary application and data.
A federation platform would enable agencies to be:
- Supportive of mission outcomes: Federation can enable and secure privacy-enhancing access to shared resources across agencies. Allowing agencies to use their PIV or CAC for access to other resources would also expedite access to resources and make collaboration simpler.
- Technology agnostic: No matter the directory or IAM system in place, a federation platform can take the data and route it appropriately. This means agencies are not reliant on one vendor or system, and can avoid new systems or costly integrations.
- Flexible: One platform can sit between agency IAMs to enable access for collaboration across all U.S. agencies.
- Cloud-first: The platform could accept identities from agencies across government with dynamic scaling, low-cost implementation, and little to no maintenance after initial deployment
- Privacy-enhancing: When an employee is provisioned into another agency's IAM via the federation platform, none of their personal information is stored in that other agency’s directory. The exact details would have to be refined, but the platform would validate the PIV and send an assertion – not personal information – to the new IAM. The federation platform also would not store any personal data.
- Standards-based: Federated identities rely on standards, such as Security Assertion Markup Language (SAML) 2.0, OAuth 2.0, OpenID Connect, and the System for Cross-Domain Identity Management (SCIM). Legacy and modern IAM systems work with these standards and can be used to enable access.
In short, there’s never been a better time to implement a federation platform across U.S. agencies to enable easy, secure, privacy-enhancing access, and collaboration for employees across the government. We can make these important reforms by embracing solutions focused on privacy, standards, platform neutrality and interoperability, and flexibility. Learn more about how identity federation and other strategies can help federal government agencies secure identities, credentials, and access in the whitepaper here.

