How Mars Leveraged Identity to Protect Sensitive Content and Applications
Maintaining the security of a large digital infrastructure poses a critical challenge for many global enterprise organizations. With a vast network of systems and devices across multiple regions, Mars, the global manufacturer of some of the world's most famous confectionery and pet brands, needs comprehensive visibility into its environment, automated incident response, and a prioritized means of solving risk-based security issues.
In this interview, we explore how Mars partnered with Okta and Material Security to leverage Identity to protect sensitive content and applications. We sat down with several of Mars' security staff, including their CISO (Matt Pecorelli), security engineering director (Larry Clark), platform security engineer (Brian McCown), and identity director (Sasa Jankovic).
Q: When it first came to solving secure access for your employees, you were evaluating multiple suppliers. Why did you go with Okta?
Matt: Mars is more like a holding company than we are just one corporation. We have several different directories and platforms that must be cross-referenced and accessed by internal teams and contractors. My responsibility is to limit risks across all organizations under the Mars umbrella. But finding solutions that manage so many disparate tenants can be difficult. Okta allows us to add collaboration across tenants and integrate with our different systems to share directories across teams and platforms using a single multifactor authentication (MFA) provider.
Sasa: The primary reason we went with Okta for our Identity exchange was from an acquisition and integration perspective. Other options were very clunky and challenging, whereas Okta's solution was just fantastic regarding their Workforce Identity and universal directory. Okta enabled us to rapidly deploy a platform and provide application access to external companies without multiple accounts. We could integrate a new company within two days of an acquisition. There was loads of flexibility, and the provisioning was phenomenal.
An Identity Provider (IdP) is no longer optional internally. The MFA layer Okta provides for us is highly user centric. Users can just smile at their screen or tap a button, no password necessary. We get a nicer experience while also becoming more secure. This is huge in improving our security posture.
Q: Once you had an IDP in place, what additional protections were you looking for?
Matt: Once we integrated Okta as our Identity solution, we knew we could leverage it with other third-party applications. Rather than take a lot of out-of-the-box functionality from the big providers, we typically seek out third parties for additional protections. We are willing to pay for new functionality separately because it is important to explore innovative approaches and solutions that smaller companies provide. Once we had Okta in place, we looked for various ways to reduce the attack surface and improve the security posture of every organization under the Mars umbrella. Email was a massive vector for us. Fortunately, I was introduced to Material Security.
Larry: First and foremost, we were looking to secure our email and ensure data loss prevention. When people leave our business, what could they take with them? How do we prevent them from taking intellectual property we don’t want to be removed? When we heard about Material Security and the unique integration with Okta, it was obvious to evaluate.
Q: There are many email security vendors out there. What made Material’s approach stand out?
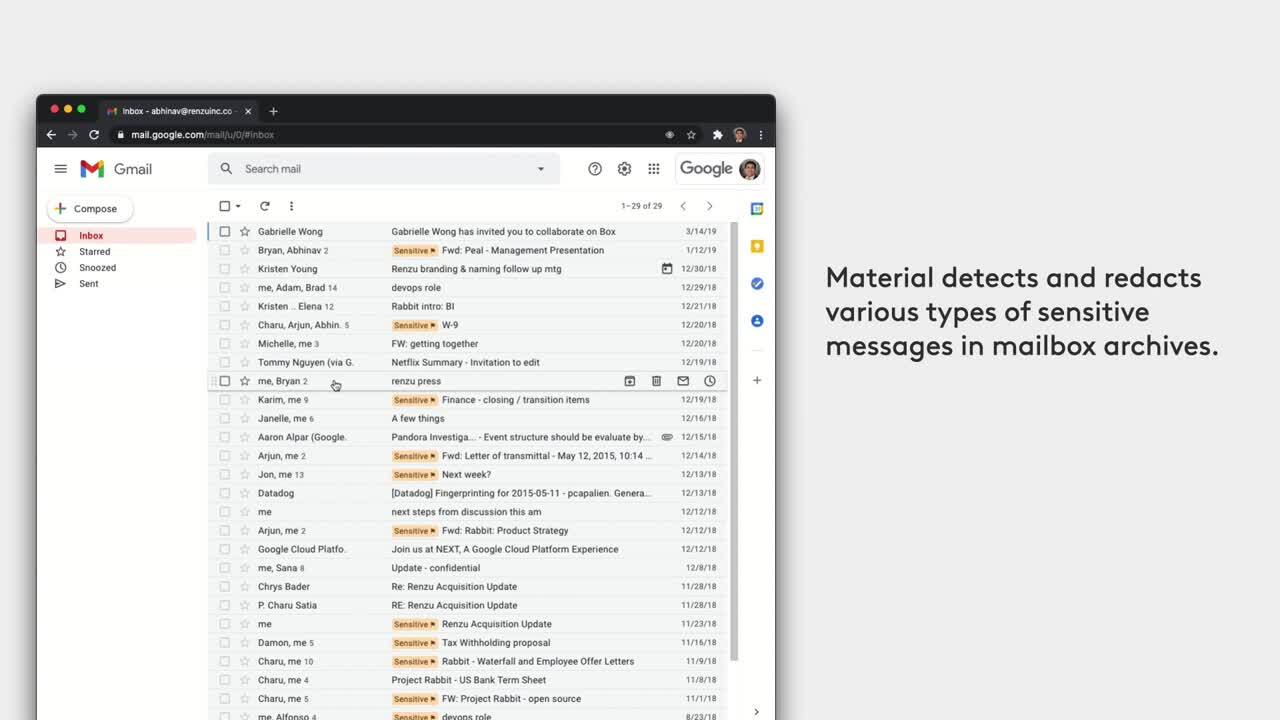
Larry: Material had a lot to offer. They were bringing together many different features we needed into one package. We looked at Material’s Data Protection feature, which protects sensitive data at rest in mailbox archives by adding a layer of Okta authentication to sensitive messages. Material will scan our associate’s mailboxes for sensitive content and redact anything flagged. If an associate needs to access a redacted message, they simply approve an Okta Verify request and immediately get access to the message. And on top of that, we gained full visibility into risky content across all our mailboxes. I’d never seen this kind of a thing before. We can now add an additional Identity check to protect our data. Plus, no need for user retraining or another tool. We just extend Okta to protect those sensitive messages.
Material with Okta has directly helped our NIST assessment framework scores. We’re held responsible for continuously driving improvements, and this partnership has helped close our open-gap items. It’s been easy to improve our score from both a deployment and end-user standpoint. We get to leverage our existing Identity service to protect even more, all while avoiding the need to retrain our associates. It was just so simple.
Matt: A standard gateway approach wasn’t appealing to us. We wanted something to enhance what we already had. With Material’s phishing protection, we’re in the process of automating the phishing incident response process. When a Mars associate reports a phishing incident, Material helps automatically cluster similar messages and apply warning messages or other remediations without the delay and manual effort of our security team’s review.
The API access allows us to run more sophisticated playbooks, and [the] search and investigation capabilities are much more efficient. There are no long wait times for searches to come back or weird result files. Plus, we can search across all of our tenants. It’s incredibly seamless, and we are receiving new visibility across all our disparate tenants and several teams under a single dashboard.
Q: Compared to other solutions you’ve deployed, what was your experience with rolling out Material?
Larry: The dedicated staff that Material provided helped us tremendously. Their team took the time to learn about our complex environment and then helped advise on deployment. Their team was willing to be highly flexible and develop and deploy the product alongside us. We wouldn't be where we are without that.
They've been a partner to us both during deployment and after. We had far fewer support tickets than any other solution rollout, and most were general end-user training rather than a bug in the Material and Okta deployment. The team has also been highly receptive to feedback and critique of their roadmap, and they listen to us and deliver on our needs. I consider us real partners. There's no bureaucracy, and it's just easy doing business together, even today, years after deployment. The flexibility and ease of doing business is the "aha" for me with Material. You don't see that a lot.
Brian: We had very low noise from the deployment, meaning very few issues. When we did have problems, Material worked with us to remediate them quickly. It's common to have some issues in a large deployment, but that aside, our support team rarely needs to interact with email security and make changes to it. Other tools break more often, and the support isn't as good. Material takes care of itself.
Q: How did users react to this new workflow?
Brian: A non-disruptive change to end-users was vital. Since our users were already familiar with using Okta for other applications, very little training was necessary. I’ve been at Mars for over ten years, and Material was one of the most intuitive and easy product deployments I've seen.
Matt: Change can be challenging for a large organization, especially for something that might at first appear to be more restrictive. So, anything we could do to add protection without necessarily adding interruptions was critical when we first evaluated Material. There were many early assumptions and fears about being unable to access older messages. But after the rollout, it was shocking how little folks interacted with older protected messages.
I saw Material and Okta's solution as a force multiplier for my team first and foremost. For anyone evaluating their joint solution, assume there will be less interruption than you might think. It took only a few clicks to get up and running. Go prove the concept out. It's a light lift, and you can roll it out to a small community first.
Q: How do you plan to continue leveraging Okta?
Sasa: We’ll continue to leverage Okta as much as we can moving forward. Our stance is that even though you’re through the front door, additional checks should still be implemented. Okta helps provide that extra “check” or layer of authentication for us. From a corporate level, support for Identity protection is no longer optional. It’s a requirement.
Matt: We’re always looking for new and novel ways for their tech to provide value. I’m already anticipating Material and Okta to continue to work together to maximize value to customers even more.
To learn how you can use Material and Okta at your organization to protect sensitive content and applications, request time with the Material team at https://material.security/request-demo.