Situation: Legacy solution makes it difficult and expensive to securely manage employee identities – from provisioning to resetting accounts
Sonos, the world’s leading sound experience company, is still growing quickly 20 years after the introduction of its pioneering multi-room wireless home audio systems. With over 1,800 employees, 800 contract workers, and a steady flow of newcomers, the company has its hands full ensuring consistent security and compliance, while managing a growing number of employee identities.
As Sonos went public in 2018, it became even more important to quickly and accurately provision employees and reset locked accounts. “We want to ensure that the Sonos workforce on- and offboard at the right times. We also want to easily track that through the identity stack,” says Curtis Norman, Senior Identity Engineer at Sonos. Key tasks also included providing the right level of access for privileged identities and membership in the appropriate Slack channels. In addition to provisioning, the team needed a simple but secure way to reset passwords or an MFA factor.
However, Sonos’ legacy identity provider made it difficult and expensive to securely manage employee identities. Some of the main challenges they faced included:
- Difficulty troubleshooting a complex infrastructure: Sonos relied on a mix of five vendors for identity and provisioning, creating five potential points of failure. If a problem occurred, they had to spend valuable resources investigating the entire stack to determine where an issue was.
- Unpredictable provisioning: Complex provisioning rules often failed, created duplicate accounts, or would not create the user at all. Attributes would remain out of date until the next full sync. This took time to remediate, and posed a security risk.
- Lack of automation: Rules were hardcoded so if adjustments needed to be made they could take weeks or months rather than hours.
- Expensive professional services and hardware: Editing provisioning rules required a costly professional services engagement. The need for additional hardware for agent servers and virtual appliance servers further increased the cost of configuration.
Solution: Implementing HR-as-a-Source and Okta Workflows no-code automation
To simplify its architecture, Sonos reassessed how it handled identity, starting with HR-sourcing. By switching to Workday for HR and integrating it with Okta, Sonos enabled a real-time process between the two systems and was able to use Okta as a source for HR-driven provisioning. “We wanted it to be entirely in HR’s hands to control when a user should and shouldn’t be active, rather than having to send a ticket or IT request,” explains David Wurtzburg, Identity Security Engineer at Sonos. This provided Sonos with a simpler architecture and far fewer points of failure, making it more efficient and easier to troubleshoot issues.
The Sonos team then began implementing automation to improve provisioning and eliminate the need for costly professional services to make basic changes. They got off their legacy system and began using SCIM provisioning when available and Okta Workflows no/low code identity automation to further extend provisioning. Sonos now uses Workflows to automate a growing list of complex provisioning and onboarding tasks and to simplify MFA resets.
Creating unique identities for privileged accounts
Sonos quickly began using Workflows to enable smooth and secure provisioning for privileged accounts such as system administrators. While these users rely on their standard accounts for computer login, email, and other user tasks, they must log in to separate privileged accounts to perform higher-level administrative tasks. Incorrectly provisioning such powerful accounts can be dangerous and costly for the business.
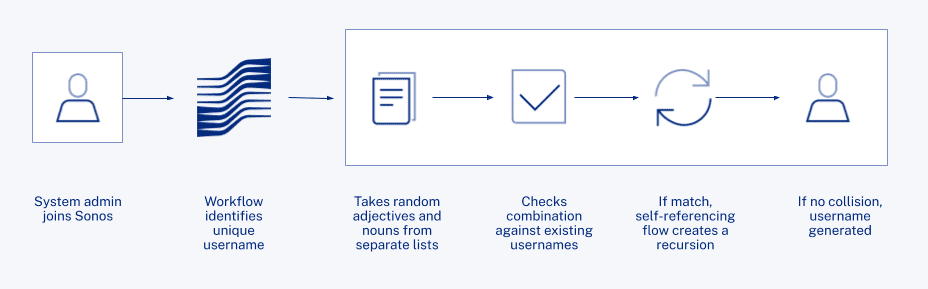
To provision these privileged accounts, Workflows creates unique identifiers for system administrators. While standard account usernames are set with a “<FirstInitial><LastName>” format, Sonos can now create privileged accounts using random adjective-noun pairs that are both anonymized and harder to guess. “The goal is both to increase the difficulty of compromising high-impact identities and to remove access from ‘standard’ identities so their authentication experience can be more convenient,” Norman explains. To this end, he created a flow to choose random adjectives and nouns from separate lists, put them together, and check the combination to see if there is a match with an existing account. If so, a self-referencing flow creates a recursion and tries again. “It’s like a one-stop shop for finding a unique username of this type.”
When the flow does not find a collision, it uses that combination to generate the privileged username. Okta Workflows then delivers the credential to the user to create their own password. “Having that self-service option out of Okta without having to deliver a password is definitely valuable to protect our privileged accounts,” Norman says.
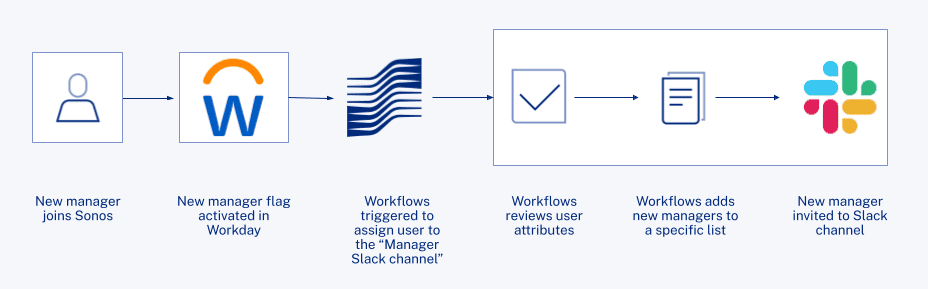
Adding employees to the right Slack channels automatically
Sonos simplifies onboarding by adding and removing users from the appropriate Slack channels. For example, Sonos uses Workflows to add new managers to a private Slack channel. “There wasn’t much handling of that lifecycle before, so it could take time to get them included,” Wurtzburg says. “We now have a flag for new managers that comes from Workday and I use a few standard Okta Workflow cards to find these users, look at their specific attributes, add them to a list, and have them invited to that specific Slack channel.”
A similar workflow automates the removal of channel members who have either left the company or reverted to individual contributor status. “There are a few cases of people who don’t have the manager flag, but still need to be part of that channel, such as HR personnel. To keep them from being removed, I excluded them from the flow with a card based on their organization level or other relevant attributes,” Wurtzburg explains.
Securing MFA factor resets
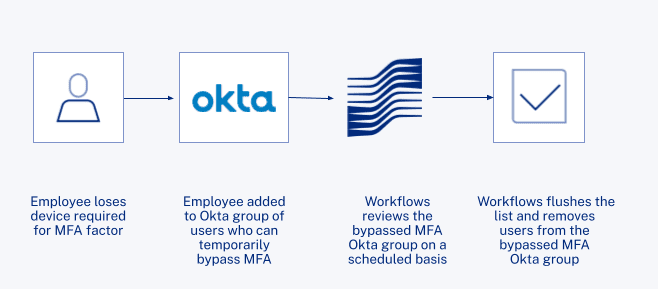
One of the company’s most used Workflows makes the factor reset process more secure. “We were running into an issue where someone would lose their phone and they would need to be bypassed in MFA, and that could be very scary for us—especially if they stayed on that list indefinitely. Six months later we could end up with 30 users having that status, long after admins had forgotten they’d added them,” said Wurtzburg. This posed a potential security threat for the company, and required manual review to take appropriate action.
To secure and simplify this factor reset process, the team turned to Workflows. They created a basic scheduled flow to handle people with the bypassed MFA status as an Okta group. The flow reviewed the list and flushed it out several times a week. “This flow helped us make sure we didn’t run into that security hole of a growing list of people with a bypass to MFA,” explained Wurtzburg.
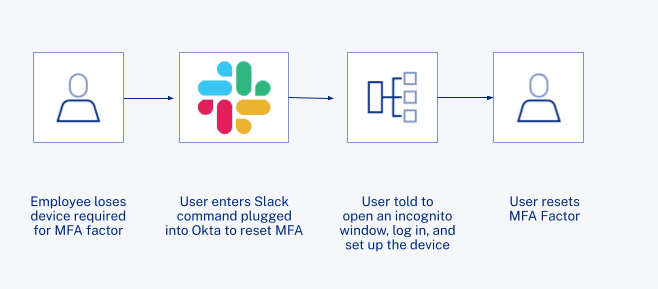
A second workflow helps users deal with the root issue. “It’s basically just a Slack command plugged into Okta to reset MFA. The user is told to open an incognito window, log in, and set up the device. That’s probably the most used workflow in the organization.”
Results: A more efficient and secure identity infrastructure
From provisioning privileged accounts, securing factor resets, and beyond, Okta Workflows has made Sonos identity management simpler, more efficient, and secure. Norman explains that “Workflows makes it easier to solve IT problems, without needing a technical background.” Wurtzburg agrees, “Okta Workflows has been just like Legos.”
Some of the most tangible benefits Sonos has received from Workflows include:
- Simplified troubleshooting and reduced potential points of failure: Consolidating their identity provider, automation, and HR-sourcing helped reduce points of failure from five to two, requiring less time and resources to troubleshoot.
- Fast and accurate provisioning: Workflows enabled Sonos to on- and offboard users in days instead of weeks, which was especially useful for last-minute creations.
- Time savings for IT and Support: IT and support teams no longer have to deal with issues like blank characters in account names—giving teams back their time.
- Reduced costs: Sonos eliminated the added hardware costs required by the previous identity vendor for agent servers and virtual appliance servers.
- Improved security: Workflows can help make MFA resets more secure, enabling the company to address potential security risks quickly through automation.
Moving forward with Okta
With its shift to HR-as-a-source complete and Okta in place as its identity source, Sonos has continued with a new phase of the initiative to incorporate its non-employee automation into Okta. “All of our non-employees are housed in SharePoint. We’ve begun using Okta’s on-premises provisioning agent with SharePoint as an authoritative source within the Okta system,” said Tarell Evans, Senior Manager, Identity and Security Operations at Sonos. “Okta can now master non-employees and write back to AD and third-party applications.” In a future phase, Sonos will create even more Okta Workflows automations for integrated flows with Jira, Google Workspace, and other third-party applications.






