Protect Against Data Breaches
Redefine security with modern identity
The challenge
Credential harvesting is a leading cause of data breaches
There is more data to protect in more places, including cloud, mobile, and legacy apps.
The solution
With identity, there’s a better approach


Centralize identity
Managing multiple passwords is hard. Managing multiple good, non-repetitive passwords is even harder. Reduce password management risk by centralizing identity with single sign-on so you can ensure the passwords you do use are as strong as possible.
Your success criteria:
- Eliminate passwords where possible
- Enable strong, unique passwords everywhere else
- Unify identity infrastructure for IT to reduce account management complexity
- Unify access for users to eliminate passwords while simplifying access
- Mitigate risk and reduce identity sprawl by restricting access to services via intelligent SAML connections
Enable strong authentication
Passwords have inherent limitations. Strengthen identity assurance with a variety of multi-factor authentication methods including one-time-passwords, soft or physical tokens, or even biometrics. Apply and manage these policies to all applications so you protect your data no matter where or how people access it.
Your success criteria:
- Harden critical applications with step-up authentication
- Apply unified policy to on-premises, cloud, and mobile

- Enable ‘MFA Everywhere’ through 7,000+ out-of-the-box connections on the Okta Integration Network
- Extend coverage to on-premises applications via support for RADIUS, RDP, ADFS, and LDAP
- Make intelligent, contextual access decisions based on device and connection attribute
Related product
Reduce attack surface
Not knowing who has access to what can leave you with security blindspots, especially if employees change roles or leave. Proper lifecycle management eliminates these gaps by reducing possible attacker entry points—plus it simplifies provisioning and deprovisioning.
Your success criteria:
- Automate provisioning with accurate entitlements
- Deprovision at scale, and enable visibility and reporting
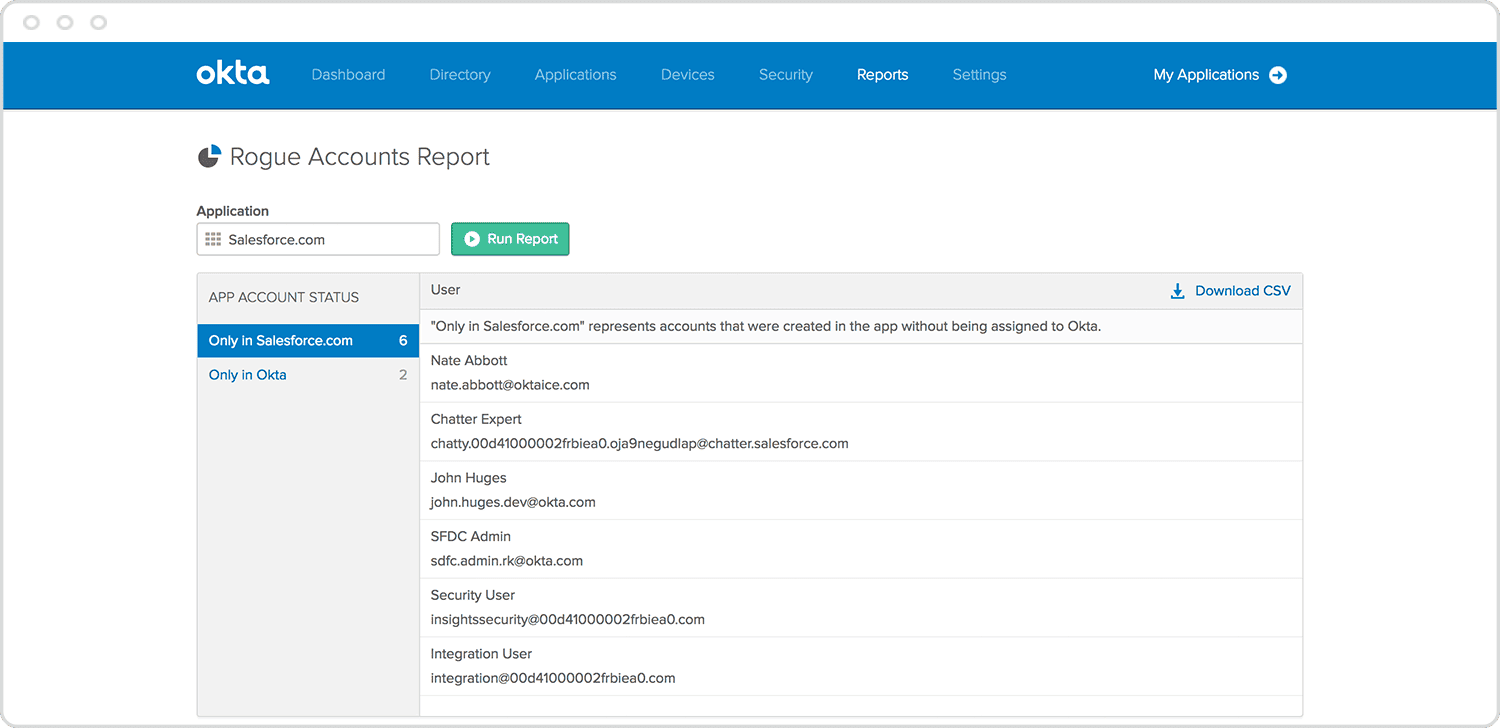
- Automated provisioning and deprovisioning accelerates consistent onboarding, while eliminating orphan accounts
- Extensible for custom applications via SCIM, SDK, and Okta’s API
- Complete lifecycle management ensures the right level of access to the right applications with access request workflows
Related product
Enable visibility and response
Security shouldn't be restricted to silos. With identity as the modern perimeter, it's essential for authentication data to be available across security systems to provide complete visibility. This gives you the opportunity to correlate seemingly disparate events, identify possible threats, and take action faster.
Your success criteria:
- Centralized, real-time reporting for all auth events
- Integrate with existing security tools
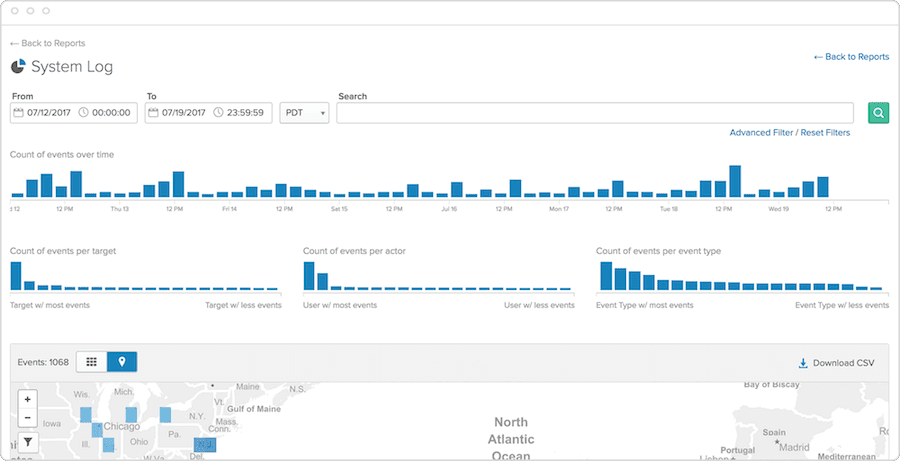
- Centralized view into all authentication data across cloud, mobile, and on-premises applications
- Identify unusual and suspicious behaviors
- Enrich and enhance your cybersecurity ecosystem via Okta's reporting and System Log API

Flex relies on Okta to secure the supply chain and manage employee access
Factory workers are now able to work securely and communicate with the business via mobile devices while Okta securely protects thousands of customers' intellectual property.