Oktane20: The Future of Device Identity
Transcript
Details
Tanvir Ahmed: Hi, my name is Tanvir Ahmed and I'm a senior product manager at Okta.
Aakash Mehta: Hey, everyone. My name is Aakash Mehta. I'm also a PM at Okta in the devices team.
Tanvir Ahmed: In this session, we'll talk about how the new Okta Devices Platform Service can be used to establish device identity in your organization, and also determine how devices can be trusted. As a reminder, Aakash And I will both be around in the chat section throughout this presentation to answer any questions you may have throughout. So let's get started.
Tanvir Ahmed: To begin, we have to show the legal paperwork. The most important part here is that everything in this deck is forward looking statements, and all business decisions should be made on current, generally available software.
Tanvir Ahmed: So let's look at an overview of how this session is going to be structured. We'll start by going over some of the challenges that we see in IT environments today. We'll then dive into the Okta devices platform service, and look into the innovations that we're making in each of the different areas that make up the Okta devices platform. And finally, we'll give you all a sneak peek at the upcoming innovations that are coming in Okta devices, as well as the rest of the ecosystem. So let's dive right in.
Tanvir Ahmed: When we look at some of the top priorities for IT admins today, inevitably, one of the first things that come up are how do you handle personal devices in the workplace? And I'm really talking about the Bring Your Own Device movement or BYOD. And in summary, really no good way to determine whether a personal device is secure. In fact, if you look at the cybersecurity insider survey, it's in one of the top three priorities for IT admins today.
Tanvir Ahmed: And what does this mean? Well, for me, if I want to be able to use my personal phone to answer a quick email or look at a design document, I should be able to do so, but from an IT admin's perspective, how do they make sure that my device is secure? Are they going to enforce management software on my device? Are they going to ask me to do redundant passwords or other factors to help me establish my identity or help me establish a secure channel to my organization's resources? Maybe, but at the end of the day, that's not really that great of a process. And there's no standardized way to be able to do this across all different platforms, whether you're on your Mac or an Android device or a Windows machine. And we feel that this is an area that requires a good solution, and it will be really helpful for IT admins.
Tanvir Ahmed: Next, going along the same path, we found that not having a single platform to be able to manage your managed devices as well as your unmanaged devices is a real pain point. In fact, what this ends up being is admins end up having a separate service, often something like Mobile Application Management, or MAM, where they'll use the separate manageability channel to then enforce basic policies on your unmanaged devices. And now that might sound nice, but that also means as an IT admin, you have to now author different sets of policies for your managed and your unmanaged devices, which ends up being extra overhead.
Tanvir Ahmed: And one of the common pain points we've seen is, well, wouldn't it be nice if all of your devices in your estate, whether they're managed or personal, showed up in a single layer, where as an admin, you can now author policies once, and it affects both your manager and your unmanaged devices. What we're really talking about here is this need for the ability to say, I want to be able to establish a certain assurance level of what a device should meet, as a minimum requirement. Whether that's a corporate owned device or a personal device, it shouldn't matter. As long as the device meets that minimum assurance level, it should be okay to access resources within my organization. And really, there's no clear single control panel that allows you to do that.
Tanvir Ahmed: And finally, we're looking at organizations and how they handle authentication today. And for the most part, authentication is handled through passwords plus some second factor. But here's the thing. Passwords are just not secure, and they end up offering a poor user experience. And it's no wonder that you look at data from Have I been Poned, for example. Nine billion plus passwords have been stolen since 2013. And why is that? Well, it's because organizations generally tend to adopt policies that try to strengthen the security posture of an unsecured password mechanism. What does that mean? Well, basically, when was the last time you were asked to rotate your password or change your password?
Tanvir Ahmed: I'm sure it happens every three months or so. That's usually the standard. But what does that really mean for an end user when they do that? Well, I've talked to many IT admins, and I've heard horror stories of how a simple security incident started because a user either had to reuse a password they've used on another website, or they've simply appended a one or another digit to the end of their existing password, because they were just so fed up with having to change their password so many times.
Tanvir Ahmed: And it's this reason why using a password is inherently not secure. And it would be great for IT admins around the world to have an experience where they can offer the same level of fidelity that's easy to deploy, yet not rely on a password mechanism. And for end users, this would be amazing also because you wouldn't have to worry about constantly remembering which password you use where, and whether you have to change your password or not.
Tanvir Ahmed: And so when we looked at these three market trends in these three very prevalent pieces of feedback from our customers, we started to do some thinking around, what would the ideal IT admin experience look like? And what would the ideal end user experience look like? Because we didn't feel like something existed today that allowed you to have that.
Tanvir Ahmed: So when we started thinking about the ideal IT admin experience, here's what we came up with. To start, it's very important to be able to, first of all, see all the devices in your organization that are being used today to access resources. Not only that, it's super important to be able to see which users own which devices that are being used. And if you have a single control plane where you're able to see all of the devices in your organization, you can have an accurate inventory of all the devices in your organization, and it allows you to do even more.
Tanvir Ahmed: It allows you to do lifecycle management of these devices. You can prevent certain devices from ever accessing other resources ever again in your organization. But more importantly, it leads into the second piece here. It allows you to have the foundation for creating this single control plane across all of your devices. You're now able to view all devices, whether they're managed or unmanaged. And now you're able to author policies in a single layer that will allow you to control access, based on things like assurance levels, whether the device can be trusted or not. And instead of having to go to different screens or different vendors to figure this out, you now have a single location where you can go to view all of your devices and have a single control plane for all of your devices.
Tanvir Ahmed: And finally, what we believe this is going to light up as a ideal experience for IT admins, is the ability for admins to be able to light up ideal end user experiences for their users. They'll be able to easily deploy things like passwordless solutions in the organization. Imagine if you have the ability to now trust the devices that are being used to access resources. Well, now maybe you don't have to ask them for a password and a second factor. Maybe you can just stick with the trust that you have in the device, maybe another biometric or something along those lines. And we feel that admins don't want to be pushing these obtrusive factors. And instead, what you'll end up with are delightful, yet secure experiences available for everyone in the organization. It'll keep security folks happy, and it'll keep the end users happy.
Tanvir Ahmed: And when we started thinking about the ideal end user experience, we believe that first and foremost, you should have the ability to use any device to access work resources and just to do work. For me personally, I definitely don't want to have to pull out my company issued laptop every time I want to make a quick edit to a design document. I should be able to just pull out my phone or really just any device. As long as I can prove it's really me in a secure way that meets my admin's requirements, I should be able to use that device. It's just that simple.
Tanvir Ahmed: Next, along the same lines, I should be able to easily access work resources. And what does that mean? Well, if I'm on a mobile device, I don't want to have to type out my really long password every time. I wanted to be able to just use the native biometrics on that device, or just use Okta verify to quickly and easily get access to my resources. I don't want to have to constantly manage a fixed set of factors, just so I get access to work.
Tanvir Ahmed: And finally, we've all been there. You either lose a device or you purchase a new one, the pain and the struggle it is to get that new device set up and productive. Well, we believe that the ideal end user experience should include this as well. And what this means, is that you should be able to quickly set up new devices, as and when you get them, with minimal extra steps.
Tanvir Ahmed: And so when we look at the ideal sets of end user experiences for both... Sorry, ideal sets of experiences for both end users and IT admins, we came up with the Okta devices platform service. And you may have seen this in Todd's keynote, but to recap, the whole platform revolves around three pillars, the first of which is being able to establish device identity. In this pillar, what we're really focusing on is being able to accurately identify the devices that are being used to access resources in the organization. Not only that, but also providing admins and end users with the ability to do two main things. One, get a complete holistic view of all the devices that are being used to access resources in the organization. And two, to provide you with a manageability layer, which allows you to do things like suspend devices or deactivate them, to prevent them from accessing additional things in the organization.
Tanvir Ahmed: The second pillar revolves around really understanding what each device is, in terms of its security posture, so that you can make a determination on whether the device can be trusted. In this step, we call this collecting and sharing device context. And in this phase, what we're really looking at is being able to collect signals from all vendors across your organization into a single context that we can use to make powerful authentication decisions, as well as other use cases that we'll go into later in this presentation.
Tanvir Ahmed: And finally, the third pillar is around enabling new experiences. Now, in Todd's keynote, you've definitely seen Okta FastPass and we're really excited about it. But Okta FastPass is just one of the things that get lit up as part of the new Okta devices platform service. FastPass is made possible because there is a certain assurance level that's made about the device in terms of its security posture. And because of that, we're able to quickly and easily, and securely by the way, sign you into your applications without having you to be prompted for additional factors.
Tanvir Ahmed: So for the rest of this deck, what we'll do is we'll dive into each pillar, and we'll review some of the key innovations that are coming out of each one. And we'll start with establishing device identity. Now, as I mentioned, the crux of device registration is really around... Establishing device identity is really around establishing device registration. And device registration revolves around new Okta Verify apps. So what we've been building our new updates to the iOS and the Android versions of Okta Verify, and we've also been working on brand new versions of Okta Verify on Windows and Mac OS. And what these new versions of Okta Verify are able to do, they're able to create device records in Okta's Universal Directory for your devices, as and when you sign into Okta Verify.
Tanvir Ahmed: So why is that important? Well, once your devices are registered, what we can now enable are two things. Being able to view all the devices in your organization, as well as get basic device lifecycle management capabilities, which we'll go into in a little bit.
Tanvir Ahmed: And finally, all of this, device registration through Okta Verify, the visibility of devices, or the lifecycle management, all of this is available in new developer SDKs that we're releasing later this year in a beta. With these developer SDKs, you'll be able to embed all of these experiences in your custom applications, whether they're for consumer side applications or line of business applications.
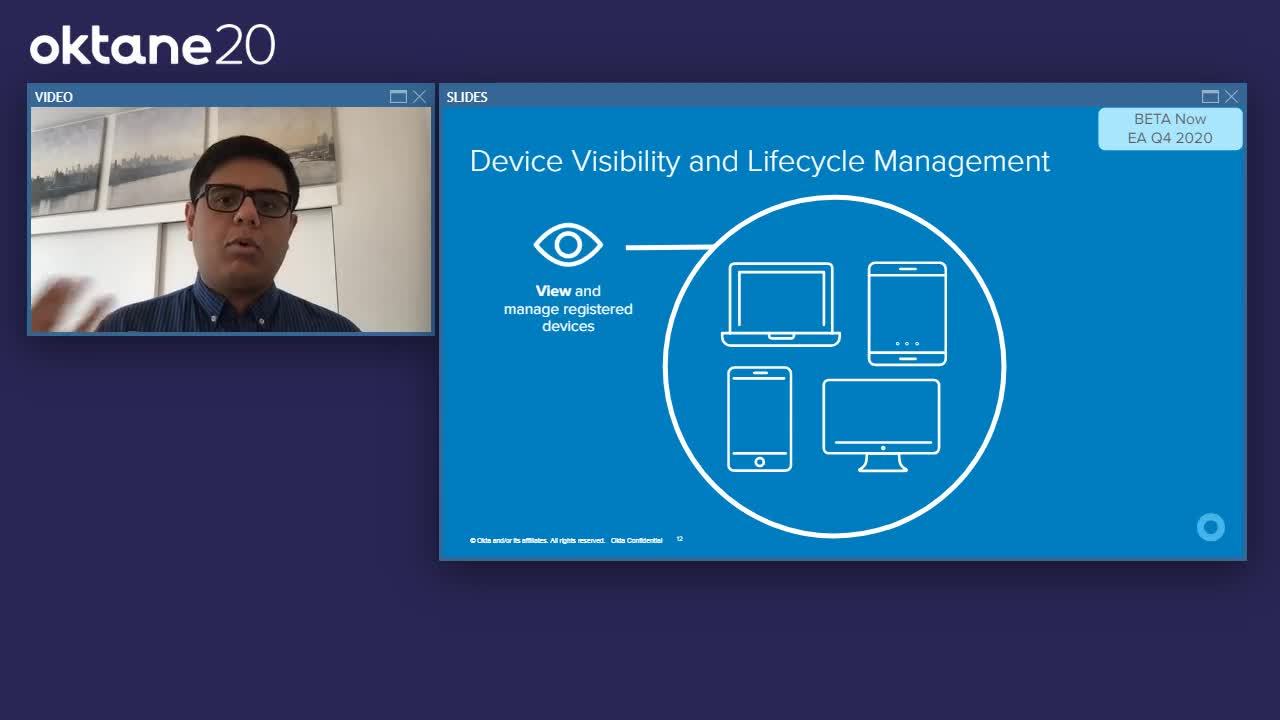
Tanvir Ahmed: When we look at device life cycle management and visibility, it revolves around four things. The first is being able to view and manage registered devices. So a single console that will allow you to view all of the devices in your organization. From here, you can perform actions, like being able to suspend the device from accessing resources. Here, you'll be able to temporarily prevent a device from being able to access a resource.
Tanvir Ahmed: You can also deactivate devices to prevent use in your tenant. So this will be the equivalent of saying, I don't like this device, it can't be trusted, and you can prevent this device from accessing resources further down the line. And finally, you can delete them to permanently remove them from your tenant.
Tanvir Ahmed: Let's take a quick look at how device registration works, using the new Okta Verify apps, specifically the one for Windows. As you can see here, we have a user, they have no devices registered. We'll go into the desktop, and we'll double click the installer for Okta Verify on Windows. We'll continue clicking through this. And once we're done, we'll open the new version of Okta Verify. And here, just like before, we'll go ahead and try to add an account, and we'll enter in the org sign in URL. So we'll give this a moment.
Tanvir Ahmed: Once you've entered in your sign in URL, you'll be prompted to sign into your organization. So this is the same as before, but what's happening in the background now is that as you're signing into Okta verify, we're actually going to be creating a device record for you in universal directory. So the account got added. And if you refresh this page, you'll see that there is now a new device that shows up under the devices list.
Tanvir Ahmed: Let's take a quick look at what life cycle management looks like, once the device is registered. So again, in our same user, what we'll do is we'll add another device, and I'm not sure what that second device is. So we'll get to that in a little bit. But for this first device we just had registered, we can actually suspend this device, if we want to prevent it from temporarily accessing resources. Perhaps I'm not sure what it is, and I choose to suspend it temporarily. I can also reactivate the device, once I verify that it's a valid device.
Tanvir Ahmed: Now for the second device, I don't know what is or where it came from, but it's an active device. What I can do is deactivate this device. And what will happen is, this device will be prevented from accessing any additional resources in my organization until I, as an IT admin, take an explicit action. I can either activate or delete this device entirely. In this case, we'll choose to delete the device entirely. And what you'll see is, when we go back to the user's profile and look at the devices registered under this user, it only shows the device we registered during the demo.
Tanvir Ahmed: Now, all of these switches for you are very powerful, yet they may seem a little bit manual. So what we've done is integrated with Okta Workflows to create device specific workflows that allow you to automate a lot of these tasks with little to no code. So, as an example, if you feel that a device's security posture has deteriorated, you can automatically trigger a workflow that will automatically remove all the SaaS app sessions from that device automatically. If the user is signing in from a suspicious location, you can automatically trigger a workflow that will suspend the device temporarily, until you verify using additional steps.
Tanvir Ahmed: All of this will be available as early access in Q4 of 2020. And now I'd like to hand it over to Aakash to talk about the remaining two pillars.
Aakash Mehta: Cool. Thanks, Tanvir. So now that we have talked about establishing device identity, let's move to the second part of the device identity platform, which is collecting and sharing device context.
Aakash Mehta: Device state can fall under four broad buckets. The first bucket is the unknown devices. So these are the devices that have not accessed Okta services in the past or are not registered with Okta Verify already. Then there's the registered devices. So these are the devices that have registered with Okta Verify, and we can treat them as such. Next is the managed devices. So these are the devices that are managed through your management tool, which could be an MDM or some other tool. And we can use managed policies on these devices. And fourth is the secure devices. So these are based on the security and compliance needs that you have set in your organization. And we can check against those.
Aakash Mehta: Overall, what we want to do is collect all of these device context through EDRs, MDMs, and other security tools, to build a cohesive collective picture of the devices that are accessing resources in your organization.
Aakash Mehta: So let's talk about device context integrations. Here on the left, you'll see the UI of where we want to integrate all of these device context together. So this is going to be your single secure panel and platform for integrating all of these device conditions together. And you can set policies for any combination of these device contexts.
Aakash Mehta: At EA in Q4 of this year, we're going to have integrations with Tanium and Carbon Clack. What you're also going to be able to do is integrate with Windows Defender. Since Windows Defender is built on Microsoft Graph APIs, which are public APIs, you can integrate those into... Or you can integrate from device context integrations in Okta to Windows Defender as well.
Aakash Mehta: So let's take a look at how all of this works in a demo. What we're going to see is how device context from Tanium is passed to Okta about a possible malware on a device.
Aakash Mehta: So first, we start by trying to log into Salesforce on a clean device with no malware, and see how that works. Great. So based on the policies, we were allowed through, and we had no issues there. Let's see what user a has registered with Okta Verify already. So you see desktop user has already registered with Okta Verify, and that's the same user we logged into Salesforce with.
Aakash Mehta: Now, somebody sent us a folder named funny cat videos. We always love to see cat videos. So let's see what's in this. We unzipped this folder, and it looks like there are some cool video in there. But actually behind this, unknown to us, there's malware that's been installed on this device. So let's see how Tanium assesses that and passes that to Okta.
Aakash Mehta: It looks like now that the malware is on my device, I am blocked from accessing Okta resources. The admin also gets further assist log and information about why my login was blocked and why there might be possible malware on my device.
Aakash Mehta: Next, let's talk about Okta Limited Access. So Okta Limited Access is something that we pushed to GA earlier this year. But what we want to do is enable admins to send not just managed and unmanaged device conditions to ISV apps, but also send all of these device context from our device context integrations to ISV applications. So now apps like Salesforce and Workday can change the experience within their app, not just based on if the user is allowed access or not, but actually get the device conditions that the user is signing in from. This is built as a platform layer, and any ISV app can take advantage of this. The device conditions are shared with the ISV app through the [inaudible 00:24:39] assertion itself as a custom attribute.
Aakash Mehta: So let's take a look at Okta Limited Access in action. We're going to look at this with Salesforce. So here, let's first see how the policies have been set up for Salesforce on the Okta side. We've set a policy to actually allow access to not trust the devices to Salesforce. But what we've done is add an additional device context attribute that will be shared with Salesforce in the [inaudible 00:25:18] assertion itself.
Aakash Mehta: On the Salesforce side, what we've done is block access to certain parts of the application, unless the user is coming in from a high assurance session or a trusted device. So first, trying to log in from this black device, which is a not trusted device, we try to access Salesforce by clicking on the app through Okta. Based on the policies, we're allowed access to Salesforce without any issues. Now, let's see what happens if we try to access the roles section within Salesforce. Because we were coming from an unmanaged device, we have insufficient privileges.
Aakash Mehta: Now let's move over to a green device, which is a device managed by [inaudible 00:26:12]. Again, we access Salesforce through Okta and are allowed access seamlessly. But now, let's again try to access the roles and report section within Salesforce.
Aakash Mehta: It looks like this time, Salesforce recognizes that we're coming in from a managed device and gives us access to these roles and reports section of the app, without any additional MFA or any additional prompts. They've got the device context from Okta in the [inaudible 00:26:51] assertion itself and are able to act on it.
Aakash Mehta: So we talked about establishing device identity, and then we talked about collecting and sharing device context. Finally, what this enables is seamless experiences for admins and end users. So let's talk about this third piece of the device identity platform.
Aakash Mehta: Let's start off with a few quick demos on how Okta FastPass works on Windows, Mac, iOS, and Android devices. What you're going to see is devices that are managed by an MDM and are already registered with Okta through Okta Verify. So first a Windows device, we're going to unlock the device using Windows Hello. And let's see what happens when we try to access Salesforce through the browser.
Aakash Mehta: So after just selecting the domain and user, we want to sign in as, Okta is able to probe the device for device context in the background and sign the user in seamlessly without any additional problems or passwords. You can see that this user has already registered with Okta Verify, using the same user credentials.
Aakash Mehta: Next, we see a similar flow on macOS devices. So here the same user who has registered with Okta Verify is going to log into Salesforce. It's so cool that Okta is able to get all the device conditions in the background without prompting the user for passwords or any additional prompts. So users get the seamless experience that they want, while admins also get the security conditions and attributes that they want on.
Aakash Mehta: On a iOS device also, it works quite similarly and in a seamless way. So after unlocking the iOS device, we're going to access Salesforce through the app. After putting in the domain and user that we want to log in as, the user is signed into Salesforce seamlessly, without even going through any app switching. So that's a great improvement for iOS users.
Aakash Mehta: And finally, on Android devices, we're going to access Salesforce. And here, this Okta sign in widget is able to probe for device conditions, which are provided through the Okta Verify app in the background. And the user credentials and device credentials are passed on to the Okta sign in widget. And the user is signed in without passwords, without any additional prompts.
Aakash Mehta: So I think that is really cool. And I know the team that worked on this is really excited about this. I'm sure customers who are going to use this are going to be very excited, as well. So let's do a quick recap of Okta FastPass. What it enables is granular device conditions. So you can not only get out of stations if the device is managed or unmanaged, but also if the user has already registered with Okta, if the device has a DPM or not, if for mobile devices, if it's jail broken or rooted, even if the user has set up biometrics on their device or not. So there's a ton of granular device conditions that you can take advantage of behind the Okta FastPass flows.
Aakash Mehta: It's also going to have this silent validation of user and device credentials. So users don't have to interact with the sign in widget. They don't have to go through and prove the device conditions. We're able to probe the device and get all of those conditions in the background, without even doing any app switching on any of the platforms.
Aakash Mehta: And finally, for those really sensitive apps and users, you can set up a step up authentication using the native biometrics on the device itself. So you get an additional layer of security for those flows, and you can be certain that you have some user verification there. So Okta FastPass is already in beta, and it's going to be in EA in Q4 of this year.
Aakash Mehta: So I want to talk about device risk based access experiences. So with all of these conditions and all of these flows coming in, we want to make it much easier for admins to set up policies on a risk level and risk basis. So here on the left, you see a bunch of devices with different conditions and attributes. Some of them are registered and managed. Some of them are jail broken. Some of them are somewhere in between.
Aakash Mehta: So when these users access Okta resources through these devices, Okta gives these devices a device risk score. So in blue are the low risk devices, in yellow are the medium risk, and in red are the high risk devices. Let's see how this works on the experiences side.
Aakash Mehta: So on the experiences side, we have set policies for low risk devices to have access through the seamless Okta FastPass flows. For the medium risk devices, they'll get a step up authentication that they have to do through biometrics. And the high risk devices are blocked entirely. The power of this platform is really that the admins can only set policies a few times for the risk levels. And then Okta does all the hard work of figuring out each device that's accessing resources, which bucket it falls under, either low risk, medium risk, or high risk. And you don't have to set policies for every permutation and combination of device conditions out there. This is going to be EA in Q4 of this year.
Aakash Mehta: Something else we've heard a lot about from admins and end users is the pain of getting a new device or setting up a new device, after losing an old device. So what we're doing is enabling multiple Okta Verify enrollments. So this means you can enroll multiple devices with Okta Verify, and then when you lose one device or you upgrade one of your devices, you can still get access to your Okta dashboard through the other device, which has already registered with Okta Verify, and then go and de-provision the last device and set up MFA on your new device easily. So this is going to cut out calls do the IT help desk and tickets, which is going to be a massive win for end users and admins.
Aakash Mehta: We're also allowing enrollment of new devices using already enrolled Okta Verify devices. So this is going to add an additional layer of security and protection for your Okta Verify enrollments. And we're also going to enable self-service password reset, using Okta Verify as a factor, amongst other factors that are unable to do so as well. This is all going to come in EA in Q4 of this year.
Aakash Mehta: For all the developers watching this, we have been working really hard to get device SDKs and APIs built that you can take advantage of in your apps. So all the cool stuff that we talked about today, you can integrate into your own custom applications using these SDKs. Some of the use cases you can enable are checking if a user is coming in from a jail broken or rooted device and blocking access, or you can also have biometrics and push and [inaudible 00:35:48] factors built directly into your application. So users don't have to use an additional separate MFA tool to do second factor authentication. So this is really cool. This is going to go to beta in Q4 of this year and EA sometime next year.
Aakash Mehta: So let's take a recap and look at the roadmap of all the stuff we talked about today. We talked about three major buckets. First was the establishing device identity. Second is a collecting and sharing device context. And the third is enabling seamless experiences for admins and end users.
Aakash Mehta: In the first half of this year, we're going to take a lot of these features to beta, and we want to get these into the hands of customers and partners, to see what the feedback is and how we can improve these things towards EA. In the second half of this year is when we're going to start pushing a lot of these features to EA. You're going to have Okta FastPass, device registration and life cycle actions, all the device context integrations in EA and Q4 of this year. And we're also going to push that device SDK to beta in the second half of this year.
Aakash Mehta: So next steps, if you're a customer, reach out to your CSM or AM to get on that Okta FastPass beta. We'd love to get your feedback, get all your thoughts, show you what all the cool stuff, and see what we can improve and make even better towards EA.
Aakash Mehta: If you're a security partner, reach out to [email protected], and we would love to get you integrated into the device context integrations platform and have customers take advantage of your tools through Okta. And if you're a developer, look out for that device SDK beta later this year.
Aakash Mehta: So thank you for watching and joining us. You can always reach out directly to me or Tanvir. These are our email IDs on the screen, but we would also love for you to reach out to us through the Okta ideas platform. This makes sure that we get everything directly, and everything is prioritized based on what customers really care about, and what they're really asking for. So thank you for joining us and take care.
Devices have become a critical part of any modern organization's Identity and Access Management strategy. From managing a BYOD policy to supporting outside partners and contractors to adopting MacBooks, the growing number of devices has increased the attack surface for IT to manage. At the same time, devices also enabled new opportunities to leverage device context for more secure authentication and better user experiences. At Okta, we continue to make core investments in Device Identity to enable a more secure and frictionless access experience on every device. Come hear our product team walk through their roadmap on how they are elevating devices to become a first class citizen within the Okta Identity Cloud and the new use cases that unlocks.