Deploy MFA for Your Workforce
Secure authorization for your workforce using contextual policies and the factors of your choice
Enhance your organization’s security posture by deploying contextual MFA
Address a variety of business requirements with flexibility with Okta for MFA
Projects Okta can help with include:
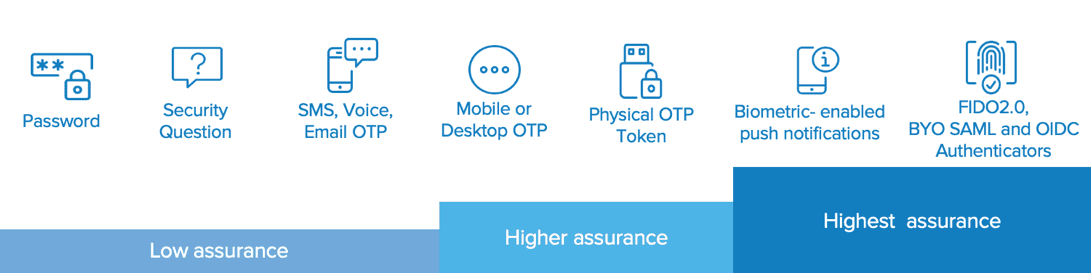
Use the factor(s) of your choice
Each organization has its own requirements for authentication and authorization. Choose the factor that best fits the security requirements of your business.
Integrations
Take advantage of our partner integrations to enhance your security posture. As a vendor-neutral platform, Okta focuses on integrating with leading security solutions, rather than proprietary stacks, enabling you to choose best-of-breed technologies that meet your business needs. Enrich your investment in MFA by using these security vendors.

